 A cohort study published in The Journal of the American Medical Association in December of 2022 revealed that Ransomware attacks targeting Healthcare delivery organizations more than doubled from 2016 to 2021. This exposed the Personal Health Information of nearly 42 million patients. During the study period, it was observed that Ransomware attacks were more likely to target large organizations with multiple facilities.
A cohort study published in The Journal of the American Medical Association in December of 2022 revealed that Ransomware attacks targeting Healthcare delivery organizations more than doubled from 2016 to 2021. This exposed the Personal Health Information of nearly 42 million patients. During the study period, it was observed that Ransomware attacks were more likely to target large organizations with multiple facilities.
Healthcare systems are usually targets of Ransomware attacks due to their critical importance and the high value of their data. Therefore, Healthcare providers and their vendors (including business associates and subcontractors) must maintain strong cybersecurity defenses and best practices, use advanced threat detection tools and mitigate the unrelenting risk of Ransomware attacks. While benchmarks under the Health Insurance Portability and Accountability Act (HIPAA) are mandatory, hackers have found ways to create loopholes in HIPAA-compliant systems, embed Ransomware, and trick users (usually employees of Healthcare providers and their vendors) into downloading it.
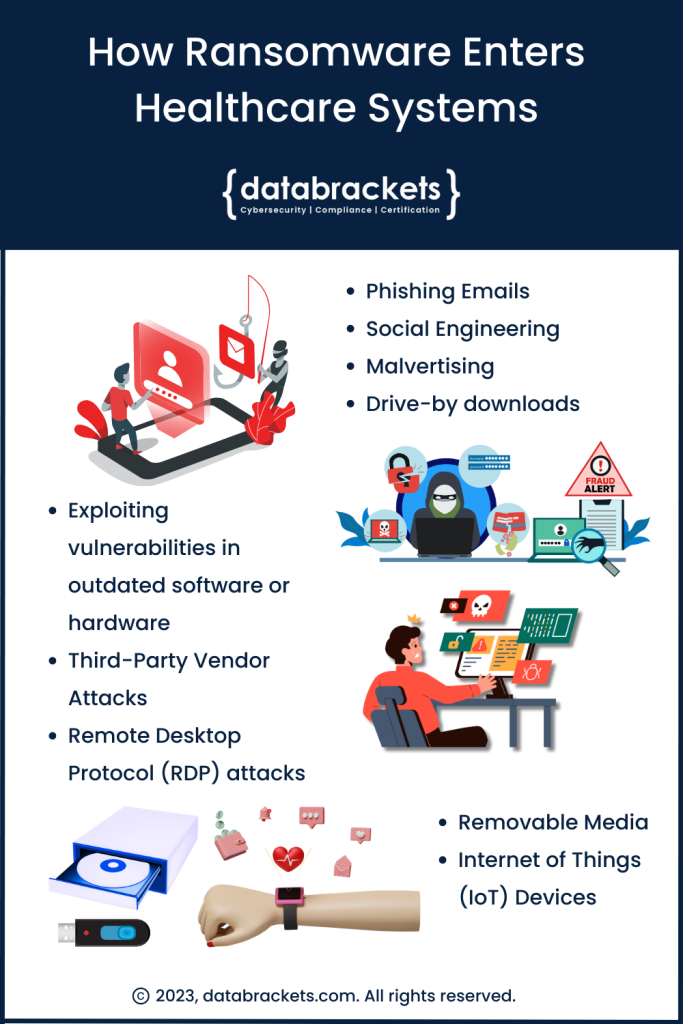
How Ransomware Enters Healthcare Systems
Ransomware, one of the most malicious software, can enter Healthcare systems in several ways. Hackers usually look for a loophole or create one through a single user’s computer and then infiltrate the network and spread it to other devices. Once Ransomware spreads, the data in the core systems are encrypted using unique keys that are known only to the hackers. Unless the hackers get compensated, the data in the core systems is unusable by the healthcare systems. This severely impacts service delivery and patient care.
There are several ways they can use to enter a healthcare provider, business associate, vendor or, subcontractor’s systems. This includes, but is not limited to:
1. Phishing Emails:
One of the most common methods for Ransomware to enter an IT infrastructure is through phishing emails. These are emails disguised as legitimate, often impersonating a trusted sender like HR, professionals working in the Billing / Finance department, Vendors, or trusted senders from other departments. The emails contain malicious links or attachments. Once an employee clicks on the link or downloads the attachment, the Ransomware can infect their computer and spread to other systems in the network.
2. Malvertising and drive-by downloads:
Malvertising involves injecting malicious code into online advertising networks. When a user clicks on an infected ad, the Ransomware is downloaded onto their system. Drive-by downloads are similar but happen on compromised websites or even legitimate ones with a security weakness.
3. Exploiting vulnerabilities in outdated software or hardware:
Attackers often exploit security vulnerabilities in software or hardware that haven’t been patched or updated regularly. These vulnerabilities can be in operating systems, applications, databases, network equipment, and medical devices. When security patches are released to fix these vulnerabilities, organizations need to update their systems promptly to protect them.
4. Social Engineering:
This involves manipulating individuals into performing actions or divulging confidential information that can be used to gain unauthorized access to systems or data. It could be a phone call or an online interaction, convincing someone to install a file with Ransomware. Common examples include Pretexting, Baiting, and Tailgating.
5. Third-party vendor attacks:
In this method, attackers compromise a trusted software vendor’s system and insert their Ransomware into software updates. When the healthcare organization installs the infected update, the Ransomware enters its system.
6. Remote Desktop Protocol (RDP) attacks:
RDP is a protocol that allows one computer to connect to another over a network. If an attacker can guess or crack the login credentials for an RDP session, they can install Ransomware on the remote system. This is especially problematic in healthcare settings where RDP is commonly used for telemedicine and remote patient monitoring.
7. Removable Media:
Ransomware can spread through infected USB drives, CDs, or other removable media.
8. Internet of Things (IoT)/Medical Devices:
As healthcare increasingly utilizes connected devices, these devices become targets. Many IoT/medical devices lack robust security, making them an attractive entry point for attackers.
This list is not exhaustive, and there is only one certainty in the field of Ransomware attacks – Hackers continue to find innovative ways to infiltrate healthcare systems. Vendors who directly and indirectly work with Healthcare providers in the US need to be HIPAA compliant. However, following the benchmarks set by HIPAA doesn’t guarantee that your systems will not be vulnerable to a targeted or ransomware attack. We have explored this at length in our blog, ‘Can a HIPAA-compliant Healthcare provider be attacked using Ransomware?’(Easwari-hyperlink to the blog)
Stay tuned for ways to Mitigate the Risk of Ransomware in Healthcare.
How databrackets can help you create a secure IT infrastructure
Experts at databrackets have extensive experience working with Healthcare Providers, Cyber Liability Insurance Providers, Managed Service Providers (MSPs), Business Associates & Subcontractors of Healthcare Providers, and Pharmaceutical and other FDA Regulated industries. Our services range from Security Risk Analysis, Pen Testing & Vulnerability Scans, Implementation of Cyber Security Technology, Managed Security Services, HIPAA compliance, and Security Risk Analysis for MIPS, among others.
Our team has supported organizations across a variety of other industries to align their processes with security frameworks like HIPAA, ISO 27001, SOC 2, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC, 21 CFR Part 11, etc.
We constantly expand our library of assessments and services to serve organizations across industries. If you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements, do not hesitate to Schedule a Consultation.
Related Links
Can a HIPAA compliant Healthcare provider be attacked using Ransomware
Protect your DICOM from Cyber Attacks
Security Tech Investments for Top 10 trends in 2023
How to Select a Security Vendor
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.

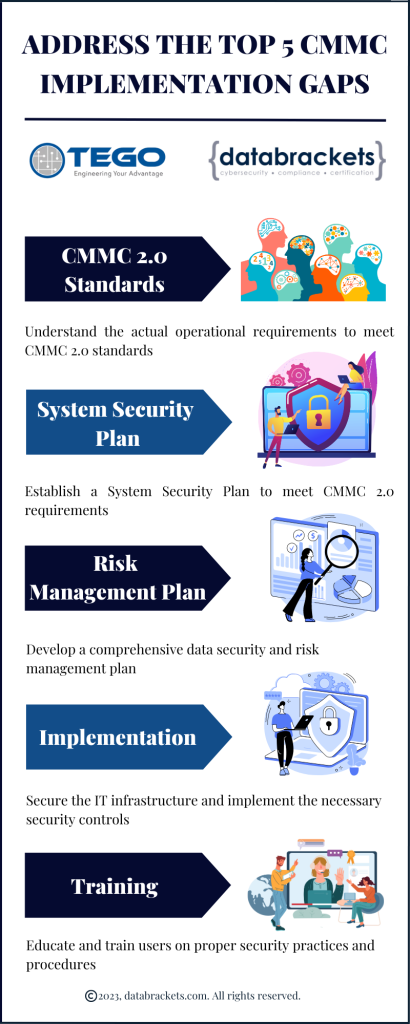 CMMC is a security framework that is mandatory for contractors who want to work with the Department of Defense (DoD). It is based on the US National Institute of Standards and Technology (NIST) family of standards, specifically on NIST SP 800-171. It was first introduced as a 5-tiered framework in 2020. The next version of the framework,
CMMC is a security framework that is mandatory for contractors who want to work with the Department of Defense (DoD). It is based on the US National Institute of Standards and Technology (NIST) family of standards, specifically on NIST SP 800-171. It was first introduced as a 5-tiered framework in 2020. The next version of the framework,  How do you prevent cyberattacks from impacting your business operations? This is the big question organizations have been asking in the wake of growing cyberattacks across industries. A growing number of data breaches have led to loss of customer data, disruptions in services, significant financial losses in addition to penalties and fines by regulatory bodies, loss of brand reputation, along with a host of other damaging outcomes. As cybersecurity and compliance experts, we decided to take a preventative approach and help businesses learn about the ways they can avoid a cyberattack from paralyzing their operations and damaging their revenue.
How do you prevent cyberattacks from impacting your business operations? This is the big question organizations have been asking in the wake of growing cyberattacks across industries. A growing number of data breaches have led to loss of customer data, disruptions in services, significant financial losses in addition to penalties and fines by regulatory bodies, loss of brand reputation, along with a host of other damaging outcomes. As cybersecurity and compliance experts, we decided to take a preventative approach and help businesses learn about the ways they can avoid a cyberattack from paralyzing their operations and damaging their revenue.
 The healthcare industry has been the target of countless hacking attempts despite adopting security protocols outlined in the Health Insurance Portability and Accountability Act (
The healthcare industry has been the target of countless hacking attempts despite adopting security protocols outlined in the Health Insurance Portability and Accountability Act ( Keeping yourself protected from cybercrime isn’t just about having the latest security solutions. Good IT security practices, including regular training for employees, are essential components of every single security setup. Make sure you’re following these 9 best practices:
Keeping yourself protected from cybercrime isn’t just about having the latest security solutions. Good IT security practices, including regular training for employees, are essential components of every single security setup. Make sure you’re following these 9 best practices: Working on contracts for B2B, B2G, or B2C engagements can be daunting. The intense focus on proving the security and privacy of your systems is usually at the heart of the process. Your customers need to know if they can trust you.
Working on contracts for B2B, B2G, or B2C engagements can be daunting. The intense focus on proving the security and privacy of your systems is usually at the heart of the process. Your customers need to know if they can trust you.