SOC 2 Compliance Guide
As an organization would you like to prove your commitment to customer data security and meet regulatory requirements, at the same time? A SOC 2 Certification is intended to do just that, and the benefits far outweigh the effort. Clients have also been increasingly asking for proof of SOC 2 Compliance, while evaluating if they want to work with a vendor. Technically, SOC 2® is not a certification. It is a report on the organization’s system and management’s internal controls as they relate to the Trust Services Criteria and it includes the auditor’s opinion of control efficacies on protecting data, also known as a ‘SOC 2® Attestation’. This guide is designed to help you navigate the SOC 2 journey and help you find practical answers. We will help you to discover the insights you need to get SOC 2 Certified, impress new clients, investors and attract talent. Understand the timeline, process, cost and expertise that you need to Succeed at SOC 2!
There are several components of becoming SOC 2 Compliant, a SOC 2 gap assessment, implementation of identified controls, a SOC 2 audit and SOC 2 report that need to be understood before you begin this journey. Getting SOC 2 Compliant fast is a marketing gimmick. As you peruse the contents of this guide, we would like to share that the official term is ‘SOC 2 examination’ and we have use the term ‘SOC 2 compliance’ interchangeably. Similarly, the official term is ‘reporting’, while we have used the commonly used term ‘certification’ interchangeably to help put the content into the appropriate context.
What is SOC 2?
SOC 2 is a compliance standard for service organizations, developed by the American Institute of CPAs (AICPA). It specifies how organizations should manage customer data. The SOC 2 framework is applicable to all technology service providers or SaaS Product companies that store customer data. They are required to ensure that security controls and practices are designed and implemented effectively to safeguard the privacy and security of customer data.
The benefits of having SOC 2 Reports are:
- Oversight of the organization
- Leading security certification issued by an independent 3rd party
- Vendor management programs
- Internal corporate governance and risk management processes
- Regulatory oversight
This security framework does not provide a specific list of controls and tools. It merely cites the criteria required to maintain a high level of information security. It is up to each organization to establish the practices and processes relevant to their own objectives and operations. SOC 2 Certification is based on 5 Trust Services Criteria: security, availability, processing integrity, confidentiality and privacy of customer data.
What is SOC 2 Compliance versus SOC 2 Certification?
Being SOC 2 Compliant is essentially having a valid SOC 2 report by an independent third-party CPA firm. Technically, SOC 2 is not a certification – it is the auditor’s opinion of control efficacies on protecting data, also known as a ‘SOC 2 Attestation’. A SOC 2 attestation is based on the Trust Services Criteria and is provided by a registered CPA firm authorized by the AICPA. Usually, a SOC 2 report is valid for a year and the organization is required to engage the same or a different CPA firm to conduct the next SOC 2 audit.
Which SOC 2 report do you need – Type I or Type II?
A SOC 2 report meets the unique needs of each organization. You can design controls that follow the SOC 2 framework, depending on your industry and business practices. These internal reports provide the company, their regulators, business partners, and suppliers, with critical information about how you manage data. There are 2 types of SOC 2 reports.
A SOC 2 Type 1 report describes the company’s systems and whether the system design adheres to the trust principles for an organization managing sensitive data, at a point in time. These trust service principles have several controls which are tested as part of the SOC 2 audit. A type 1 audit usually takes 1-2 months.
A SOC 2 Type 2 report explains the design and operational efficiency of the company’s system and controls, throughout a period of time. A type 2 report also includes a detailed description of the service auditor’s tests of controls and the results of those tests. A SOC 2 Type 2 audit is conducted over 3-12 months. The duration depends on the organization’s preference and the needs of the users (readers) of the report. During the audit, the system design and performance of controls are tested. Most of your customers and business partners usually require a SOC 2 Type 2 audit conducted in the last 3-12 months to get assurance on how an organization is managing customer data over a period of time. The subsequent reporting periods are typically 12 months, after the first SOC 2® Type 2 Report.
What is a SOC 2 Audit?
A SOC 2 audit is conducted by a registered CPA firm authorized by the AICPA. It assesses the design and performance of the internal controls implemented by an organization at a point in time or over a defined number of months. The assessment includes identifying all the controls that were in place during the period and taking a sample to test the end-to-end performance of these controls. The results of the audit and the effectiveness of the controls are outlined in the SOC 2 audit report. This provides third-party assurance to clients and business partners.
What is evaluated in a SOC 2 audit?
Compliance with the SOC 2 framework is evaluated in a SOC 2 audit. This framework is based on AICPA’s Trust Services Criteria: security, availability, processing integrity, confidentiality and privacy of customer data.
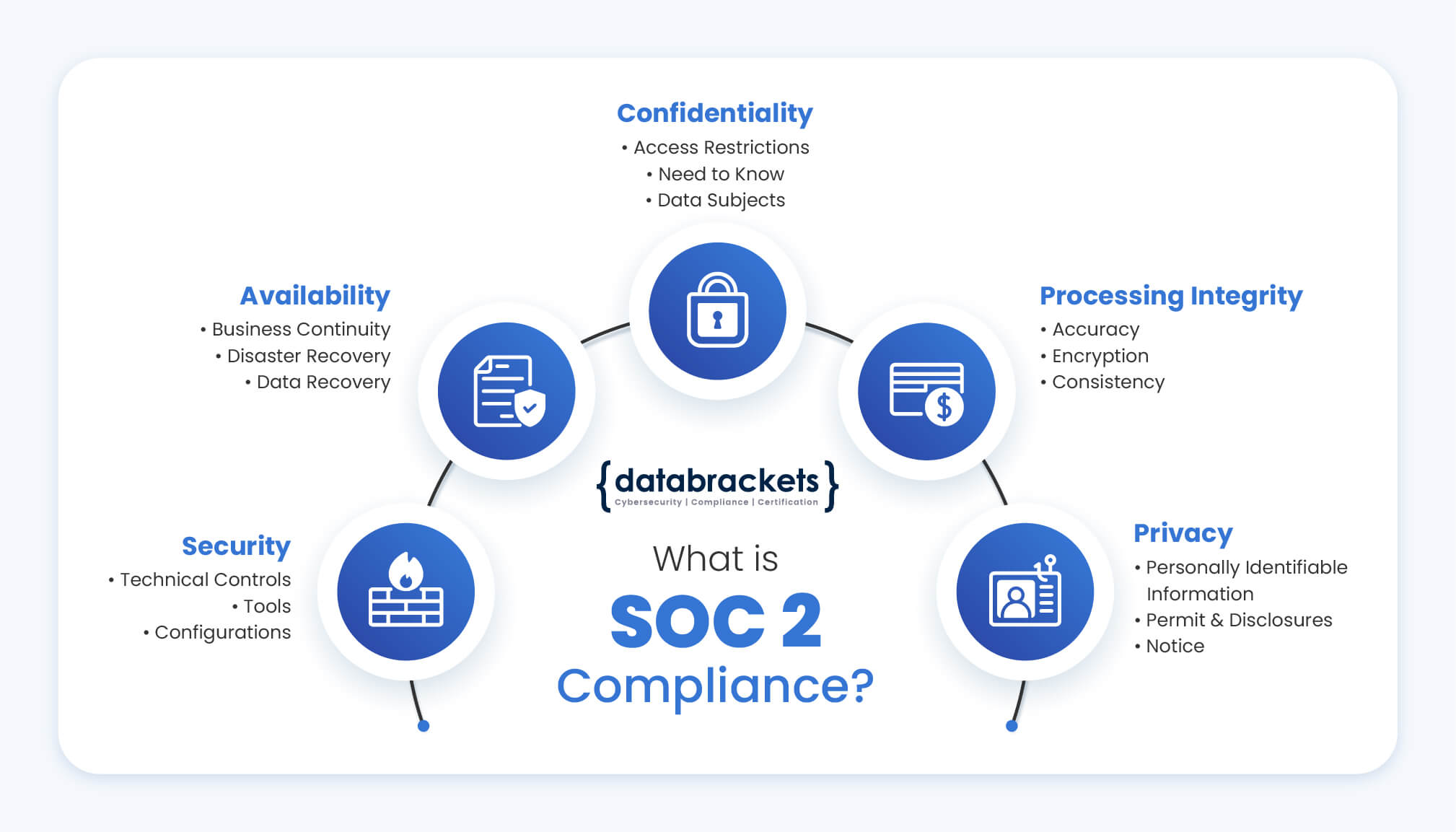
- Security focuses on the protection of information and systems from unauthorized access. Organizations are expected to ensure that all aspects of access control – authorization, authentication, accessing, management and auditing are mapped and they prevent the possibility of theft, system abuse, unauthorized disclosure, modification or removal of data and misuse of software. This can be achieved by employing security tools, technologies and processes that are focused on protecting the network, systems, applications and other assets. Web application firewalls (WAFs), two-factor authentication, intrusion detection, restricted access via VPN are some of the additional technical security controls required to be implemented.
- Availability focuses on the resiliency of infrastructure, software and information. This includes operational controls and continuous monitoring to improve the availability of the systems for its users. It checks the level of accessibility of the services, as promised in the Service Level Agreement (SLA) by the company and contracts. A company’s minimal acceptable network performance levels are also assessed to ensure they are sufficient to mitigate potential external threats. While it does not verify usability and system functionality, it primarily focuses on all aspects of security which affect availability – network performance, backup, disaster recovery, business continuity, site failover and security incident handling, among others.
- Processing integrity verifies if the systems achieve their purpose – delivery of the accurate and complete data, within the correct timeframe and level of access. This includes assessing if the systems are error-free and protected from manipulation and unauthorized access. This section requires the organization to implement encryption of data during transit, at-rest and during processing.
- Confidentiality refers to the ability of the company to restrict access and allow disclosure of data only to authorized personnel or organizations. Common examples of confidential data include business plans, pricing decisions and internal price lists, intellectual property, contracts, sensitive financial and legal information. This information is only intended for select personnel. Organizations can use encryption to protect the confidentiality of data during transmission. To protect data that is stored or being processed on computer systems, they can use stringent access controls along with network and application firewalls.
- Privacy addresses the ability of the organization to protect Personally Identifiable Information (PII) which can identify an individual. Details like the name, address, Social Security number, credit card information, health information, race, ethnicity etc. form an integral part of the PII which must be protected from unauthorized access. The controls used by the organization are assessed under this principle including the collection, use, disclosure, retention and disposal of such information in accordance with their Privacy Policy and the criteria set forth in the AICPA’s generally accepted privacy principles (GAPP). The security incident response system is also evaluated in the case of a data breach.
These Trust Services Criteria are typically organized into 7 categories with controls under each category. They are:
| Sr. No. | Category | No. of Controls |
| 1 | Organization and management | 4 |
| 2 | Communications | 6 |
| 3 | Risk management and design and Implementation of controls | 3 |
| 4 | Monitoring of controls | 1 |
| 5 | Logical and physical access controls | 8 |
| 6 | System operations | 2 |
| 7 | Change management | 4 |
There are also some additional criteria under the following Trust Services Principles:
| Sr. No. | Trust Services Principles | Additional Criteria |
| 1 | Availability | 3 |
| 2 | Processing Integrity* | 6 |
| 3 | Confidentiality | 6 |
*5 out of 6 additional criteria under Processing Integrity are also common for Security, Availability, and Confidentiality.
Organizations that are SOC 2 compliant adhere to strict information security policies and procedures, which ensure these criteria are met.
How to Succeed at SOC 2
Any successful SOC 2 audit consists of the following steps :
- Planning: Planning consists of identifying the overall objectives, the reason why the company wants a SOC 2 certificate – whether it is the customer driven requirement, or they want to adhere to some security standard/framework, or is it driven by internal requirements.
Then they need to identify the scope for the SOC 2 Audit. This begins with identifying the sensitive data, whether it is customer data, financial data, proprietary data and what systems need to be included as part of the audit. Organizations need to know what they want to protect and identify the system boundaries. This will determine the scope for the auditor and guide the way for the rest of the exercise.
- Gap Assessment: We use our proprietary platform to go over individual controls, that the company is required to adhere to. Although these individual controls are generic in nature, depending on scope and on technology – whether the company is using technology on cloud, on-premise, or a hybrid model, some of the control applications will change. Understanding this part is key when we’re doing the gap assessment.
As the organization goes through the entire gap assessment based on the trust services criteria and the criteria that the company wants to comply, we identify the controls that need to be assessed. When we’re done with the gap assessment, we provide a very specific list of things that the company needs to do to become SOC 2 compliant. This is not done by auditors; it is done by the databrackets team to determine the gaps within the process. This gives them very specific recommendations of controls they need to design and implement.
- Implementation: Implementation of controls resides with the company. They decide internally who will implement the controls. databrackets also provides certain recommendations with options for them to implement. Example, if they speak about encryption or end-point-protection, we give them very specific recommendations in terms of what kind of technologies they need to use based on how their systems are designed and the kind of risks they are exposed to. The timeline for this could be a few weeks to a few months depending on how the resources and budget is allocated for the project.
- Re-Testing of Controls: After implementation, we re-test the controls to check if they’ve been implemented in an efficient and effective way, so that we can officially start the audit period. As we do the testing, we ensure that the Information Security policies are implemented properly – they are defined at the organization level, the management is involved in defining these policies and information has been disseminated properly wherever the procedures are required to be implemented by staff including the IT, Admin and employees/end users. This is a critical part of SOC 2 Readiness. This helps the company to succeed in their SOC 2 audit.
We also complete a Security Risk Assessment and we make sure their staff is trained with respect to the policies and procedures that are applicable for them. We also conduct Vulnerability Assessment and Penetration Testing if it is defined in the policy.
- During the SOC 2 Audit period: The audit period only begins when all the controls are in place and all aspects of information security are performing as designed. The company finalizes the CPA firm or independent auditors and in collaboration, they decide the start date and the duration of the audit period. The first SOC 2 examination period is usually 3-6 months. The company cannot modify any process during the audit period. The start date of a SOC 2 audit is in the future and it is shared with the CPA firm. Evaluating performance outside of the audit or examination period is not part of the audit.
As the audit period is in progress, experts at databrackets make use of the time to do random testing of the controls to make sure everything is working. We also develop the other required information that will be part of the audit – the overall management objectives for security and compliance and writing the description of the system so that it meets the description criteria. These are shared with the CPA firm.
- Providing Evidence: The audit or testing of the controls, starts immediately after the period of time ends. It begins with the auditors collecting evidence for all the controls and for some controls with populations, selecting a random sample from a population of data, based on scientific sampling principles. The purpose of the SOC 2 audit is to allow auditors to observe security controls in action as they relate to the random sample. The company is expected to showcase evidence and confirm that all the controls have been designed and implemented per intent. Design and implementation efficacies of the controls are validated with the evidence and the results are documented. Once the SOC 2 audit period is over, experts at databrackets work with the CPA firm to the collect the evidence items on the request list and share the required evidence. For example, if access level controls are being tested, we furnish details about access that was created to the core system in the last 6-month period. The auditors pick a few samples from that user access list and then they audit if the company is following appropriate access policies and procedures.
Succeeding at SOC 2 implies a consistent dedication to internal controls and AICPA’s Trust Services Criteria. We recommend that organizations understand the controls and ensure compliance at all times. Regular testing of controls helps organizations to stay compliant and seamlessly renew their SOC 2 Certificate. This also helps them to enjoy an uninterrupted status as an organization that provides assurance through SOC 2. To understand how our security experts can assist your organization, schedule a free consultation.
How long does it take to get SOC 2 compliant?
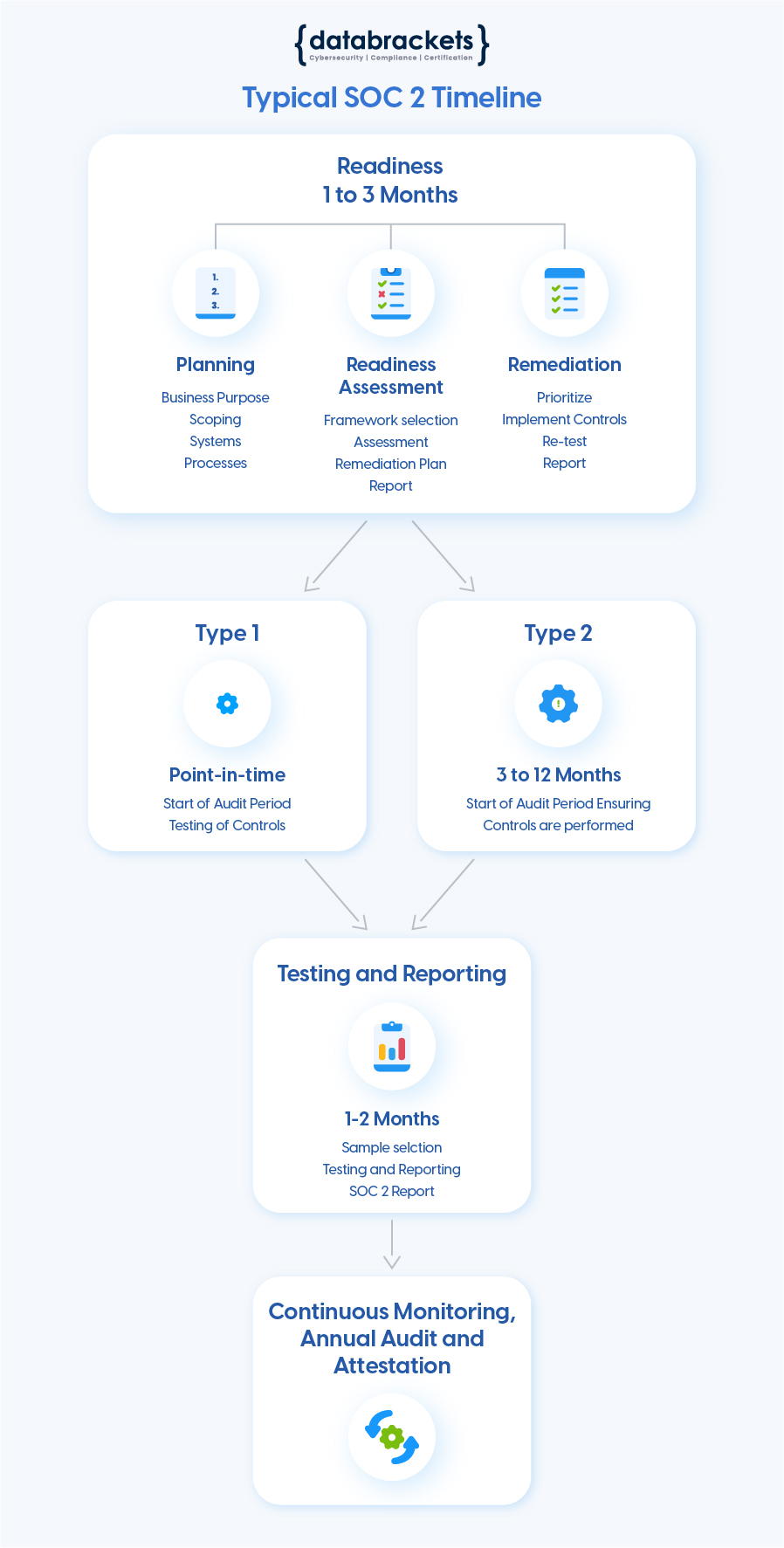
The duration varies for a Type 1 and Type 2 report. Organizations usually require 1-2 months to complete a SOC 2 Type 1 audit and receive their report. A SOC 2 Type 2 audit, takes about 3-12 months. Though some organizations promise SOC 2 audit reports within weeks, we generally recommend that organizations plan a minimum of 6 months for a SOC 2 Type 2 report. Renewals are annual.
How regularly are you required to perform a SOC 2 audit?
SOC 2 audits are conducted every 12 -18 months and the SOC 2 report is valid for 12 months.
What does SOC 2 Certification cost?
A typical SOC 2 engagement for readiness could cost anywhere from USD 10,000 – 50,000. The readiness engagement could be very involved in designing/implementing new controls, implementing policies and procedures and training. A SOC 2 attestation by a CPA firm could cost anywhere from USD 15,000 to 30,000 depending on the trust service criteria selected by the customer.
How databrackets prepares you to Succeed at SOC 2
For organizations who plan to get SOC 2 Certified and undergo a SOC 2 audit for the first time, it is common to seek the services of security and compliance experts who can assess their readiness, help find loopholes in their processes and support them in plugging the gaps. databrackets works in conjunction with certified CPA firms to prepare our customers to get ready for SOC 2 and obtain SOC 2 report. Our security experts have helped several reputed organizations prepare for and get SOC 2 Certified.
The databrackets team helps you with:
- Readiness Assessment & Recommendations
We begin with understanding your objective for SOC 2 Certification and the criteria you want to be audited for. Our security experts assess your existing processes, Information Security Policy (Infosec Policy), Privacy Policy and security awareness training. We identify gaps in your processes based on the criteria you want to be audited for. In the next stage, we recommend modifications and additions to your Infosec policy, data privacy protocols, IT infrastructure technology and help you plug the gaps. Our experts have worked closely with SOC 2 auditors and base their recommendations on the controls that are expected from a SOC 2 compliant organization. This greatly reduces the time spent on getting ready for a SOC 2 Audit and helps organizations to achieve their SOC 2 objectives.
- Testing of Controls, Vulnerability Assessment and Security Risk Assessment
This is the litmus test of a secure architecture and security controls. Once your processes and system design are SOC 2 compliant, we begin testing your controls and conduct Vulnerability Assessments, Penetration Testing and a Security Risk Assessment, as required. You have the opportunity to remedy any processes during this time and opt for re-testing before approaching your SOC 2 auditor. When you are assured that all the controls, policies and training are SOC 2 compliant, you can approach an authorized CPA firm to begin your SOC 2 audit. We also support your organization by randomly testing controls during the SOC 2 audit, to help you identify any deviations from security protocols.
- Content for SOC 2
During the SOC 2 Audit, we develop the other required content that will be part of the reporting – the overall management objectives for security and compliance and the description criteria. These are shared with the CPA firm.
Connect with one of our security experts to explore the approach that would be best for your organization.
*SOC 2 is a registered trademark.
Explore our SOC 2 FAQ’s
Technology service providers, SaaS providers and any organization that stores and processes customer data.
- Regulatory oversight: Once you are SOC 2 Compliant, you are aligned with AICPA’s regulatory controls. A SOC 2 certificate is proof of that.
- Supervision of the organization: SOC 2 compliance mandates supervising all aspects of information security across all processes internally along with setting the benchmarks for vendors who manage customer data. In order to accomplish this, a robust process is designed, and its effectiveness is verified once an organization is SOC 2 Certified.
- New Clients: You can sign more deals and increase the number of clients once you prove your ability to effectively manage customer data with a SOC 2 Certificate
- Existing Customers: You can prove to your existing customers that your company not only manages their customer data with the highest level of information security, but that this has also been verified by an authorized CPA firm after a rigorous SOC 2 audit.
- Vendor Management programs: You can set the benchmarks for vendors and ensure compliance with the highest level of information security.
- Internal corporate governance and risk management processes: You can design and monitor risk management processes and internal corporate governance in accordance with the SOC 2 framework.
A SOC 2 report is given by the auditor after a SOC 2 audit. It meets the unique needs of each organization. You can design controls that follow the SOC 2 framework, depending on your industry and business practices. These internal reports provide the company, their regulators, business partners, and suppliers, with critical information about how you manage data. There are 2 types of SOC 2 reports.
A SOC 2 Type 1 report describes the company’s systems and whether the system design adheres to the trust principles for an organization managing sensitive data, at a point in time. These trust service principles have several controls which are tested as part of the SOC 2 audit. A type 1 audit usually takes 1-2 months.
A SOC 2 Type 2 report explains the design and operational efficiency of the company’s system and controls, throughout a period of time. A type 2 report also includes a detailed description of the service auditor’s tests of controls and the results of those tests. A SOC 2 Type 2 audit is conducted over 3-12 months. The duration depends on the organization’s preference and the needs of the users (readers) of the report. During the audit, the system design and performance of controls are tested. Most of your customers and business partners usually require a SOC 2 Type 2 audit conducted in the last 3-12 months to get assurance on how an organization is managing customer data over a period of time. The subsequent reporting periods are typically 12 months, after the first SOC 2® Type 2 Report.
If an organization claims that they are SOC 2 Compliant, it demonstrates their ability to meet the requirements of AICPA’s Trust Service Criteria. However, a SOC 2 report also called a SOC 2 certificate, is the opinion of the auditor about the controls followed by an organization. During the audit period, the performance of the controls are tested and documented. A thorough review of a SOC 2 report would in general provide assurance to anyone who wants to conduct business with a SOC 2 recipient. Unlike other certifications, SOC 2 report is not reviewed or approved by the AICPA.
SOC 1 focuses on internal controls over financial reporting especially conducted by public organizations or organizations being acquired by other organizations. Whereas a SOC 2 audit focuses on trust services principles for any organization managing sensitive data. These trust service principles have several controls which are tested as part of the SOC 2 audit. However, SOC 3 reports are prepared for more generic public use, and it is not very popular in the industry. All SOC reports are to be issued by licensed independent CPAs or CPA (Certified Public Accountant) firms that specialize in the organization’s specific industry.
A SOC 2 Type 1 report describes the company’s systems and whether the system design adheres to the trust principles for an organization managing sensitive data, at a point in time. These trust service principles have several controls which are tested as part of the SOC 2 audit. A type 1 audit usually takes 1-2 months.
A SOC 2 Type 2 report explains the design and operational efficiency of the company’s system and controls, throughout a period of time. A type 2 report also includes a detailed description of the service auditor’s tests of controls and the results of those tests. A SOC 2 Type 2 audit is conducted over 3-12 months. The duration depends on the organization’s preference and the needs of the users (readers) of the report. During the audit, the system design and performance of controls are tested. Most of your customers and business partners usually require a SOC 2 Type 2 audit conducted in the last 3-12 months to get assurance on how an organization is managing customer data over a period of time. The subsequent reporting periods are typically 12 months, after the first SOC 2® Type 2 Report.
The SOC 2 framework is the SOC 2 certification criteria. These are also called SOC 2 requirements. This framework is based on AICPA’s Trust Services Criteria: security, availability, processing integrity, confidentiality and privacy of customer data. They are:
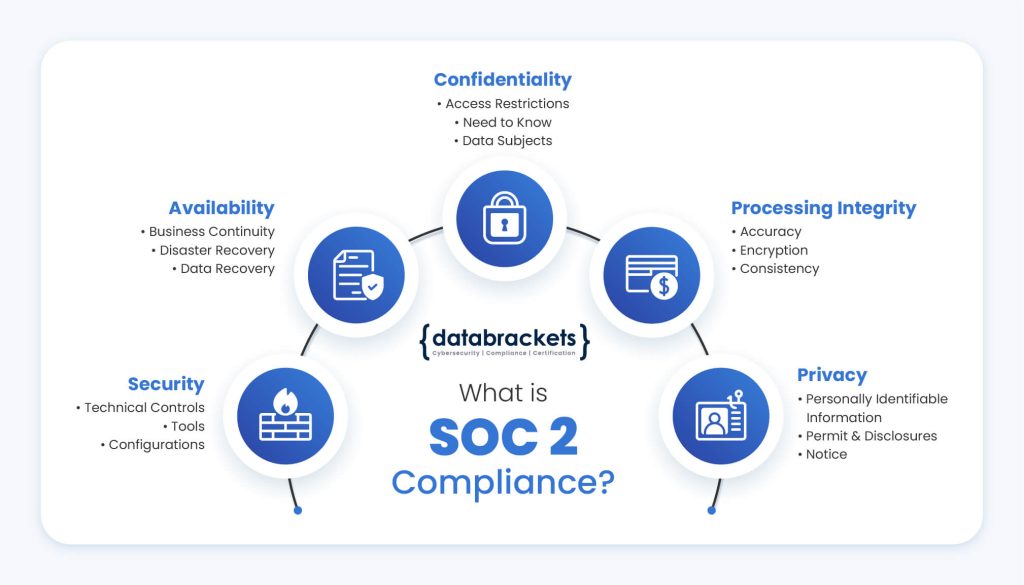
- Security focuses on the protection of information and systems from unauthorized access. Organizations are expected to ensure that all aspects of access control – authorization, authentication, accessing, management and auditing are mapped and they prevent the possibility of theft, system abuse, unauthorized disclosure, modification or removal of data and misuse of software. This can be achieved by employing security tools, technologies and processes that are focused on protecting the network, systems, applications and other assets. Web application firewalls (WAFs), two-factor authentication, intrusion detection, restricted access via VPN are some of the additional technical security controls required to be implemented.
- Availability focuses on the resiliency of infrastructure, software and information. This includes operational controls and continuous monitoring to improve the availability of the systems for its users. It checks the level of accessibility of the services, as promised in the Service Level Agreement (SLA) by the company and contracts. A company’s minimal acceptable network performance levels are also assessed to ensure they are sufficient to mitigate potential external threats. While it does not verify usability and system functionality, it primarily focuses on all aspects of security which affect availability – network performance, backup, disaster recovery, business continuity, site failover and security incident handling, among others.
- Processing integrity verifies if the systems achieve their purpose – delivery of the accurate and complete data, within the correct timeframe and level of access. This includes assessing if the systems are error-free and protected from manipulation and unauthorized access. This section requires the organization to implement encryption of data during transit, at-rest and in processing.
- Confidentiality refers to the ability of the company to restrict access and allow disclosure of data only to authorized personnel or organizations. Common examples include business plans, pricing decisions and internal price lists, intellectual property, contracts, sensitive financial and legal information. This information is only intended for select personnel. Organizations can use encryption to protect the confidentiality of data during transmission. To protect data that is stored or being processed on computer systems, they can use stringent access controls along with network and application firewalls.
- Privacy addresses the ability of the organization to protect Personally Identifiable Information (PII) which can identify an individual. Details like the name, address, Social Security number, credit card information, health information, race, ethnicity etc. form an integral part of the PII which must be protected from unauthorized access. The controls used by the organization are assessed under this principle including the collection, use, disclosure, retention and disposal of such information in accordance with their Privacy Policy and the criteria set forth in the AICPA’s generally accepted privacy principles (GAPP). The security incident response system is also evaluated in the case of a data breach.
Organizations that are SOC 2 compliant adhere to strict information security policies and procedures, which ensure these criteria are met.
The SOC 2 framework is the SOC 2 certification criteria. These are also called SOC 2 requirements.
Most organizations host their infrastructure platform on popular Cloud Solution Providers (CSP) like AWS, Microsoft Azure or Google Cloud Platform. Most of the services offered by these CSPs go through vigorous third-party independent audits and CSPs share their SOC 2 Type 2 reports. However, SaaS organizations operate under the shared responsibility model where only the cloud infrastructure is covered by the CSP’s SOC 2 report. The responsibility of the SaaS vendor including software development, hosting, configuration and data management is based on SaaS vendors’ processes, tools and technologies. That’s why many in the industry require both the CSPs and SaaS vendors to obtain SOC 2 reports since security and privacy is only as good as the “weakest link” in the entire setup. It is safer to secure the entire ecosystem.
There is no Pass/Fail in a SOC 2 audit. It is the auditor’s opinion of the effectiveness of a company’s controls. A SOC 2 report is expected to capture the effective and ineffective controls and shared in a transparent way. An auditor’s opinion is based on in-depth observation during the audit period, and they have the authority to dive deeper into the evidence or ascertain from initial reports if the company’s controls are operating effectively.
The audit period only begins when all the controls are in place and all aspects of information security are performing as designed. The company finalizes the CPA firm or independent auditors and in collaboration, they decide the start date and the duration of the audit period. The first SOC 2 examination period is usually 3-6 months. The company cannot modify any process during the audit period. The start date of a SOC 2 audit is in the future and it is shared with the CPA firm. Evaluating performance outside of the audit or examination period is not part of the audit.
The audit, or testing of the controls, starts immediately after the period of time ends. It begins with the auditors collecting evidence for all the controls and for some controls with populations, selecting a random sample from a population of data, based on scientific sampling principles. The purpose of the SOC 2® audit is to allow auditors to observe security controls in action as they relate to the random sample. The company is expected to showcase evidence and confirm that all the controls have been designed and implemented per intent. If controls are implemented correctly and the company is SOC 2 ready, customer data is protected, and no violation is observed. The absence of activity during the audit is a sign of success since it implies that all aspects of data protection are in place.
As the audit period is in progress, experts at databrackets make use of the time to do random testing of the controls to make sure everything is working. We also develop the other required information that will be part of the audit – the overall management objectives for security and compliance and the description criteria. These are shared with the CPA firm.