Security Tech Consulting
Safeguard Your Organization's Digital Assets with Cutting-Edge Security Tech to Meet Your Specific Requirements
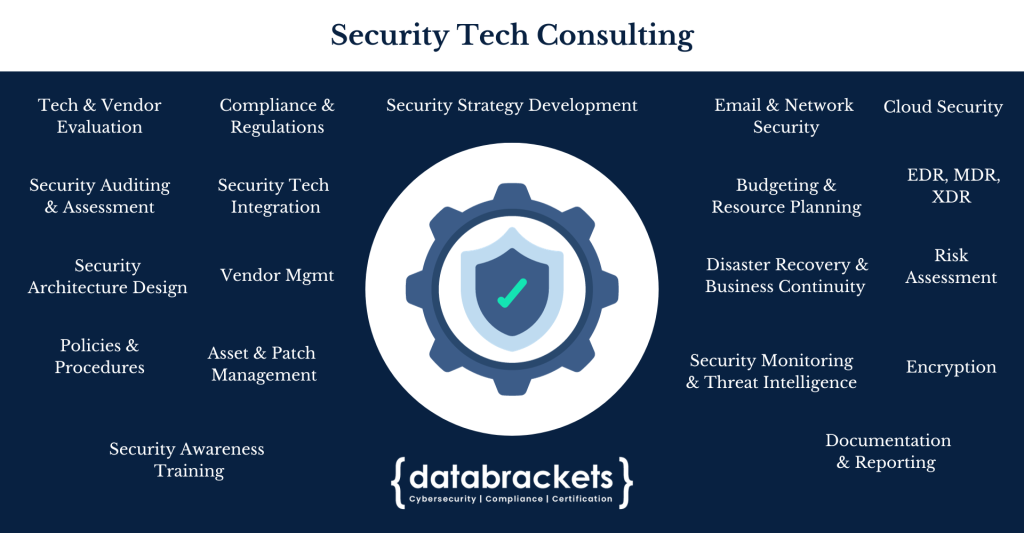
Security Tech Consulting
Security technology plays a pivotal role in thwarting evolving cyber threats by employing advanced mechanisms and strategies to safeguard digital assets and information. With the constantly evolving landscape of cyberattacks, technologies such as next-generation firewalls, intrusion detection systems, and artificial intelligence-driven threat detection have become indispensable. These tools help organizations to proactively identify and respond to sophisticated threats, including malware, phishing attacks, and zero-day vulnerabilities. In today’s digital era, cyber threats continue to grow in complexity and frequency, and the integration of cutting-edge security technology remains essential in fortifying our digital defenses and preserving the integrity of critical data and infrastructure.
Our certified security experts have over a decade of experience working with leading security vendors. Our team uses a comprehensive approach to implement security technology and protect your digital assets. This involves tailored solutions, ongoing support, and a proactive stance against security threats.
Security Tech Consulting Process
Implementing Security Tech Solutions is part of Remediation. Remediation is the third aspect of a 3-part process with Identification and Assessment being the first two aspects. Given below are the steps we follow for Security Tech Consulting.
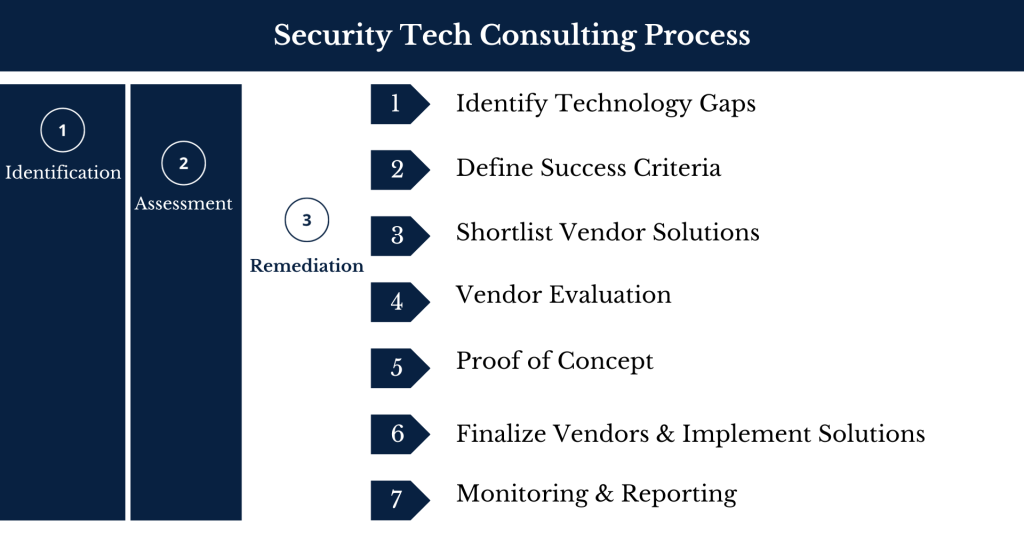
1. Identify Technology Gaps: We begin by creating a comprehensive list of security measures, technologies, or strategies that need to be implemented within your organization to enhance security.
2. Define Success Criteria: Define clear and measurable success criteria for each security implementation, specifying what you expect to achieve in terms of improved security, compliance, or risk reduction.
3. Shortlist Vendor Solutions: Research and narrow down potential security vendors or solutions that align with your security needs and budget constraints.
4. Vendor Evaluation: Evaluate shortlisted vendors based on factors like their reputation, capabilities, pricing, support, and compatibility with your existing systems.
5. Proof Of Concept: Before committing to a vendor, conduct a proof of concept (PoC) to test the selected security solution in a real-world scenario to ensure it meets your requirements.
6. Finalize Vendors And Implement Solutions: After successful PoC, finalize vendor contracts and proceed with the implementation of the selected security solutions, ensuring they are integrated seamlessly into your existing infrastructure.
7. Monitoring and Reporting: Establish ongoing monitoring and reporting mechanisms to continuously assess the effectiveness of the implemented security measures based on the defines success criteria, detect and respond to threats, and provide regular updates to stakeholders on the security posture of the organization.




























