In today’s competitive landscape, demonstrating robust security practices is no longer a nicety; it’s a necessity. Achieving SOC 2 certification by an independent third-party auditor is a powerful way to showcase your commitment to data security and gain a strategic edge. However, navigating the complexities of the SOC 2 journey can feel daunting. Here’s where a SOC 2 compliance readiness partner steps in. A SOC 2 readiness partner acts as your trusted guide, providing the expertise and support you need to achieve compliance efficiently and effectively.
Working with a SOC 2 Compliance Readiness Partner not only provides reasonable assurance to achieve your SOC 2 compliance but also prepares your organization for a SOC 2 Audit. The SOC 2 Audit is part of a SOC 2 Examination, which results in a SOC 2 Report. While this is not technically a certification process, it is often referred to as one because of the impartiality of the SOC 2 auditor, the thoroughness of their evaluation, and the details in their SOC 2 Report. A favorable SOC 2 Report proves your compliance with AICPA‘s Trust Services Criteria and helps you unlock the doors to new business, check many of the RFP (Request For Proposal) requirements, strengthen client trust and, ultimately, accelerate your revenue growth.
Security experts at databrackets have supported various clients as their SOC 2 Compliance Readiness Partner. We have worked with SaaS Providers, MSPs, Start-ups, Healthcare Providers, Radiology Organizations, Pharmaceutical Companies, Financial Services & Accounting Firms, Law Firms, Insurance Firms, etc. Our experience across industries has been possible because of our customized approach and focus on evidence collection and documentation, which CPAs need during a SOC 2 Audit. We have worked closely with various CPA partner firms and ensure they receive documentation in a systematic manner through dbACE, our GRC Platform. Additionally, clients have the option to engage their own CPA firm for their SOC 2 Examination, with databrackets serving as their readiness partner.
Benefits of working with a SOC 2 Compliance Readiness Partner
Engaging a readiness partner before undergoing a SOC 2 audit can be highly beneficial for organizations. Here are several reasons why:

1. Expert Guidance
A readiness partner brings expertise in SOC 2 compliance and understands the intricacies of the audit process. They can provide invaluable guidance on interpreting SOC 2 Trust Service Criteria (TSC), implementing required controls, and preparing documentation to meet audit requirements.
2. Efficiency
By working with a readiness partner, organizations can streamline their SOC 2 compliance efforts. The partner helps identify gaps and weaknesses in controls early on, allowing the organization to address them proactively before the audit. This can save time and resources during the audit process.
3. Risk Mitigation
SOC 2 compliance is about ensuring the security, availability, processing integrity, confidentiality, and privacy of data. A readiness partner helps organizations identify and mitigate risks in these areas, reducing the likelihood of audit findings and non-compliance issues.
4. Tailored Approach
Every organization is unique, with different business processes, systems, and risk profiles. A readiness partner tailors their approach to the specific needs and circumstances of the organization, ensuring that compliance efforts are aligned with its objectives and operational realities.
5. Preparation for Audit Success
Engaging a readiness partner increases the likelihood of a successful SOC 2 audit outcome. By thoroughly assessing readiness, addressing deficiencies, and providing ongoing support, the partner helps the organization demonstrate its commitment to compliance and readiness to auditors.
SOC 2 compliance is increasingly becoming a prerequisite for business, especially in industries dealing with sensitive data. By achieving SOC 2 compliance with the help of a readiness partner, organizations enhance their reputation and instill confidence among customers, partners, and stakeholders.
Having a readiness partner before undergoing a SOC 2 audit can significantly improve the organization’s readiness, efficiency, and overall success in achieving compliance. By leveraging their expertise and support, organizations can navigate the complexities of SOC 2 compliance more effectively and position themselves for long-term security and regulatory compliance.
Role of a SOC 2 Compliance Readiness Partner
A SOC 2 Readiness Partner plays a crucial role in assisting organizations in preparing for a System and Organization Controls (SOC) 2 audit. SOC 2 audits are performed to assess the effectiveness of controls related to security, availability, processing integrity, confidentiality, and privacy of data within service organizations. Here are the tasks typically performed by a SOC 2 Readiness Partner:

1. Initial Consultation and Scoping
The Readiness Partner begins by understanding the organization’s business objectives, services provided, and the scope of the audit. They then work closely with the organization’s stakeholders to identify critical systems, processes, and data flows that need to be evaluated for SOC 2 compliance.
The Readiness Partner educates the client on the requirements and expectations of SOC 2 compliance and provides guidance on interpreting SOC 2 Trust Services Criteria (TSC)and standards applicable to the organization’s industry and specific circumstances.
A comprehensive gap analysis evaluates the organization’s current controls against SOC 2 requirements. The Readiness Partner identifies areas where controls are lacking, weak, or not adequately documented to meet SOC 2 standards.
4. Control Mapping
After identifying gaps, the Readiness Partner helps the organization map existing controls to SOC 2 criteria. They ensure that controls are aligned with the Trust Service Criteria (TSC) defined by the American Institute of CPAs (AICPA).
5. Documentation Review and Development
The Readiness Partner assists in creating or updating policies, procedures, and documentation to meet SOC 2 requirements. They help draft control narratives, risk assessments, and other necessary documentation to support SOC 2 compliance efforts.
6. Remediation Planning
Based on the gap analysis, the Readiness Partner develops a remediation plan outlining steps to address identified deficiencies. They prioritize remediation efforts based on risk and criticality to ensure efficient use of resources.
7. Implementation Support
A SOC 2 Compliance Readiness Partner provides ongoing support during the implementation of remediation measures. They assist in configuring systems, implementing security controls, and training staff to ensure compliance with SOC 2 requirements.
8. Internal Audit
Conducting an internal audit helps the organization simulate the actual SOC 2 audit process. The Readiness Partner assists in preparing for the SOC 2 Audit by conducting test procedures, reviewing documentation, and identifying areas for improvement.
9. Readiness Assessment Report
After completing the readiness assessment process, the Readiness Partner prepares a comprehensive report detailing findings, recommendations, and the organization’s readiness for the SOC 2 audit. This report serves as a roadmap for the organization’s SOC 2 compliance journey and helps demonstrate readiness to stakeholders and auditors.
10. Ongoing Support and Monitoring
Once the organization is prepared for the audit, the readiness partner will facilitate communication with SOC 2 audit firm, ensuring that all necessary information is provided. This includes assistance with the description criteria, furnishing evidence for controls, aiding in the collection of sample evidence, conducting walkthroughs, participating in interviews with the audit firm, and addressing any unresolved inquiries or issues raised by the audit firm.
A SOC 2 Readiness Partner plays a critical role in guiding organizations through the process of preparing for a SOC 2 audit. From initial scoping to ongoing support, they help organizations understand, implement, and maintain the necessary controls to achieve SOC 2 compliance. During your journey to SOC 2 Compliance, we recommend you consider undergoing Vulnerability Assessment and Pen Testing.Vulnerability Assessment and Pen Testing for SOC 2 Compliance
Your SOC 2 Readiness Partner may also offer vulnerability assessment and penetration testing services to help you prepare for your SOC 2 Audit and to ensure your controls are SOC 2 compliant. Here’s how vulnerability assessment and penetration testing can be integrated into the preparation for SOC 2 compliance:
1. Identify Security Weaknesses
Vulnerability assessment involves scanning systems, networks, and applications to identify security weaknesses such as misconfigurations, outdated software, and known vulnerabilities. Penetration testing takes this a step further by simulating real-world attacks to exploit identified vulnerabilities.
2. Mitigate Risks
By conducting vulnerability assessments and penetration tests, your Readiness Partner helps your organization identify and mitigate risks to data security, availability, processing integrity, confidentiality, and privacy—key areas of concern for SOC 2 compliance.
3. Align with SOC 2 Criteria
SOC 2 requires organizations to have effective controls in place to protect sensitive data and ensure the integrity and availability of systems. Vulnerability assessments and penetration tests help identify weaknesses in these controls, allowing the organization to address them before the audit.
4. Demonstrate Due Diligence
By proactively conducting vulnerability assessments and penetration tests, the organization demonstrates due diligence in safeguarding sensitive information and meeting SOC 2 requirements. This can enhance confidence among customers, partners, and auditors in the organization’s commitment to security and compliance.
5. Commit to Continuous Improvement
SOC 2 compliance is not a one-time effort but requires continuous monitoring and improvement of security controls. Vulnerability assessments and penetration tests provide valuable insights into evolving threats and vulnerabilities, enabling the organization to adapt its security measures accordingly.
While vulnerability assessment and penetration testing are not explicitly required for SOC 2 compliance, they are highly recommended practices to strengthen an organization’s security posture and readiness for the audit. By helping identify and address security vulnerabilities, these services contribute to building a robust control environment aligned with SOC 2 criteria. Therefore, a SOC 2 Readiness Partner may offer these services as part of their comprehensive approach to preparing organizations for SOC 2 compliance.
How databrackets can help you achieve SOC 2 Compliance
databrackets works in conjunction with certified CPA firms to prepare our customers to get ready for a SOC 2 Examination and obtain a SOC 2 report. Some of the services by our security experts are:
- Readiness Assessment & Recommendations
- Testing of Controls, Vulnerability Assessment and Security Risk Assessment
- Support to draft the Management Assertion for your SOC 2 Report
SOC 2 Examination by a certified CPA includes
- Determining the Trust Services Criteria
- Finalizing the SOC 2 Audit Period
- Scoping of the systems and applications
- Sampling & reviewing the evidence and policies & procedures
- Interviewing process owners
- Walkthrough of the systems/processes
- Testing the controls
- Documenting and reporting
The CPA that you chose to work with can access all your evidence in a streamlined manner on dbACE – our GRC Platform.
databrackets overview
Our team of security experts has supported organizations across a wide variety of industries to align their processes with security frameworks like HIPAA, 21 CFR Part 11, ISO 27001:2022, SOC 2, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Related Links:
SOC 2 Type 2 Audit for SaaS Companies
Can you submit a SOC 2 Report instead of a Vendor Security Questionnaire?
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.
Cybersecurity and Compliance Best Practices for Radiology
In the rapidly evolving landscape of healthcare, the integration of technology has become indispensable, particularly in the field of radiology where digital systems are fundamental to diagnosis and treatment. However, as the reliance on digital platforms increases, so does the vulnerability to cyber threats. Hence, ensuring robust cybersecurity measures alongside strict compliance protocols has become imperative for the radiology sector.
The convergence of sensitive patient data, advanced imaging technologies, and interconnected networks underscores the critical need for tailored cybersecurity and compliance best practices. Not only do these practices safeguard patient confidentiality and data integrity, but they also uphold the reliability and trustworthiness of diagnostic procedures, ultimately contributing to the delivery of high-quality patient care in radiology.
With over a decade of experience in supporting radiology organizations to meet compliance and cybersecurity requirements, our certified experts have identified security tech, policies, training, and testing to enhance your cybersecurity posture. These are in keeping with industry best practices. The price point of implementing these industry best practices varies depending on your set-up. One way to ensure you are making the right choices for your organization is to undergo a Security Risk Analysis to detect areas of improvement and design a comprehensive cybersecurity strategy to integrate the best practices ideal for your organization.

1. Compliance & Customer Contracts for Radiology
1. HIPAA Compliance
Ensure adherence to the Health Insurance Portability and Accountability Act (HIPAA) federal regulations, which govern the security and privacy of patient health information.
If applicable, comply with the General Data Protection Regulation (GDPR) standards, particularly when dealing with patient data of European Union residents.
Conduct regular third-party independent cyber security audits and assessments to ensure compliance with relevant data protection regulations and standards and insurance cybersecurity requirements.
4. Customer Contracts
Most customers, including hospitals and other entities that share sensitive data, mandate that their vendors perform regular cybersecurity audits and tests.
2. Cybersecurity Best Practices for Radiology
1. Firewalls
Install and maintain robust firewalls to monitor and control incoming and outgoing network traffic, protecting against unauthorized access. Firewalls safeguard radiology systems by controlling incoming and outgoing network traffic, ensuring data integrity and patient confidentiality. They act as a crucial barrier, shielding radiology networks from unauthorized access and potential cyber threats.
Utilize encryption technologies to secure patient data both at rest and in transit, ensuring that even if data is intercepted, it remains unreadable. Encryption in radiology ensures patient data remains secure, safeguarding sensitive medical information from unauthorized access. Through advanced cryptographic techniques, patient confidentiality is maintained, fostering trust in the healthcare system.
Deploy IDS and IPS solutions to detect and prevent unauthorized access, malware, and other security threats. In radiology, Intrusion Detection Systems (IDS) monitor network traffic for potential threats, alerting administrators to suspicious activities such as unauthorized access to patient data. Meanwhile, Intrusion Prevention Systems (IPS) in radiology actively intervene to block or mitigate cyberattacks, safeguarding sensitive medical information and ensuring the integrity of diagnostic processes.
4. Regular Security Updates
Stay current with security patches and updates for all software, hardware, and systems to address vulnerabilities and enhance overall security posture. Regular security updates for radiology software ensure continuous protection against evolving cyber threats, safeguarding sensitive patient data and maintaining the integrity of medical imaging systems, prioritizing patient confidentiality and operational stability in healthcare environments.
5. Endpoint Protection
Implement endpoint protection solutions to secure devices such as computers, mobile devices, and medical equipment from malware and other cybersecurity threats. Endpoint Protection for radiology ensures robust security measures, shielding critical medical imaging devices from cyber threats, preserving patient data integrity and confidentiality. With real-time monitoring and advanced encryption, it fortifies the digital perimeter of radiological systems, safeguarding against unauthorized access and potential breaches.
6. Security Information and Event Management (SIEM)
Utilize SIEM tools to collect, analyze, and correlate security event data, enabling proactive threat detection and incident response. Utilizing Security Information and Event Management (SIEM) in radiology ensures robust monitoring and detection of potential threats, safeguarding sensitive patient data and maintaining regulatory compliance. SIEM solutions offer real-time analysis of security events within radiology systems, enabling prompt response to breaches or anomalies, thereby enhancing overall cybersecurity posture in healthcare environments.
7. Identity and Access Management (IAM)
Implement IAM solutions to manage user identities, control access to systems and data, and enforce least privilege principles. Identity and Access Management (IAM) in radiology ensures that only authorized healthcare professionals can access sensitive patient data, safeguarding patient privacy and maintaining compliance. IAM systems in radiology streamline user authentication, facilitating seamless access to critical imaging resources while bolstering security against unauthorized entry or data breaches
8. Data Loss Prevention (DLP)
Deploy DLP solutions to monitor, detect, and prevent unauthorized access or transmission of sensitive patient data, both within the organization and externally. Data Loss Prevention (DLP) in radiology ensures secure handling of sensitive patient information, safeguarding against unauthorized access or inadvertent disclosure, preserving patient confidentiality and regulatory compliance. By implementing DLP measures, radiology facilities mitigate risks of data breaches, maintaining integrity and privacy of medical records essential for patient care.
9. Other security best practices
Based on your environment & architecture, the security technology, policies and procedures need to be appropriately chosen and implemented.
3. Policies and Procedures for Radiology
1. Data Classification
Establish a data classification policy to categorize patient data based on sensitivity and define appropriate handling and protection measures for each category. Data classification in radiology involves organizing medical images and patient information into categories based on factors like pathology, anatomy, and imaging technique, aiding in efficient retrieval and analysis for accurate diagnoses and treatment planning. By categorizing radiological data, healthcare professionals can streamline interpretation processes, enhance data security measures, and facilitate research endeavors aimed at improving patient outcomes.
2. Access Control Policies
Implement access control policies and procedures to ensure that only authorized individuals have access to patient data, based on the principle of least privilege. Access control policies for radiology ensure only authorized personnel access sensitive patient images and records, safeguarding patient privacy and medical data integrity with strict authentication measures and role-based permissions. Implementation involves meticulous regulation of user privileges, encryption protocols, and audit trails to maintain confidentiality and compliance with healthcare regulations.
3.Incident Response Plans and Procedures
Develop a comprehensive incident response plan outlining procedures for detecting, responding to, and mitigating data breaches or security incidents promptly. In radiology, an incident response plan ensures swift and coordinated action in the event of equipment failure or data breach, safeguarding patient information and maintaining operational continuity. By delineating roles, protocols, and communication channels, the radiology incident response plan mitigates risks, minimizes downtime, and upholds quality standards in diagnostic imaging services.
4. Documented Procedures
Document all security-related procedures, including data handling, storage, transmission, and disposal, and ensure that employees are trained on and adhere to these procedures consistently. Documented procedures in radiology ensure precision, guiding technicians through each step with clarity and consistency. These protocols safeguard accuracy and streamline diagnostic processes, enhancing patient care.
5. Business Continuity Planning
Effective business continuity planning for radiology ensures uninterrupted patient care amidst emergencies, safeguarding critical imaging services. Proactive measures, including redundancy protocols and remote access solutions, mitigate risks and uphold operational resilience in radiology practices.
6. Business Associate Contracts
A business associate is a person or company that performs certain functions or activities that involve the use or disclosure of protected health information (PHI) on behalf of the healthcare provider, or provides services to a Radiology firm (i.e. the covered entity). It is important to include all key elements in your business contract.
Key elements of a Business Associate Contract include:
- The nature of the services being provided by the business associate and the use of PHI involved.
- Safeguards that the business associate must implement to protect PHI.
- The business associate’s obligation to report any unauthorized use or disclosure of PHI, including breaches of unsecured PHI, to the covered entity.
- Requirements for the business associate to ensure that any subcontractors that create, receive, maintain, or transmit PHI on behalf of the business associate agree to the same restrictions and conditions.
- The radiology firm’s right to terminate the contract if the business associate violates a material term of the agreement.
4. Staff Training for Radiology
1. Phishing Training
Radiology employees undergo phishing training to enhance their awareness, recognizing and thwarting potential cyber threats lurking in deceptive emails. Through simulated exercises, they learn to identify red flags and safeguard sensitive medical information from phishing attacks.
2. Security Awareness Training
Security awareness training for radiology employees ensures vigilant protection of sensitive patient data, fostering a culture of confidentiality and compliance within the healthcare environment. Empowering staff with the knowledge to identify and mitigate cybersecurity risks strengthens the overall security posture, safeguarding both patient privacy and organizational integrity.
3.Compliance Training
Compliance-oriented training for radiology employees ensures adherence to rigorous safety protocols and regulatory standards, minimizing risks associated with medical imaging procedures. By emphasizing compliance with industry guidelines and best practices, radiology staff are equipped to deliver quality patient care while maintaining ethical and legal integrity.
4. Policy and procedures training based on roles
Policy and Procedures training tailored to radiology roles ensures precise adherence to safety protocols and regulatory standards, enhancing patient care and operational efficiency within the radiology department. By aligning training with specific job functions, radiology employees gain the expertise needed to navigate complex imaging processes with accuracy and confidence.
5. Automated and Manual Security Testing for Radiology
1. Vulnerability Assessment & Pen Testing
Automated and Manual Vulnerability Assessment & Pen Testing for Radiology involves evaluating and fortifying digital systems to protect sensitive medical data from cyber threats. While there are differences between these 2 types of security testing methods, there are several benefits of conducting both to test different aspects of your cybersecurity strategy.
2. Areas of Pen Testing for Radiology
While there are several Benefits of Pen Testing for Radiology, there are specific areas which Pen Testers focus on for Radiology organizations. They are:
ii. Application Testing: In radiology application testing, precision and accuracy are paramount to ensure reliable diagnostic outcomes. Rigorous testing protocols validate the software’s ability to interpret medical images with utmost clarity and clinical relevance.
iii. Mobile App Testing: Ensuring precision in diagnostic accuracy, mobile app testing for radiology rigorously evaluates image resolution and data transfer reliability. Each pixel scrutinized, every feature vetted, mobile app testing for radiology ensures seamless integration into clinical workflows.
iv. IoT Testing: In IoT testing for radiology, meticulous verification of data accuracy and real-time transmission integrity is imperative to ensure seamless integration with diagnostic imaging systems. Rigorous validation protocols are essential to guarantee the reliability and security of IoT devices, safeguarding the confidentiality and integrity of sensitive patient information in radiological settings.
Static code testing for radiology involves analyzing the source code without executing it, aiming to detect potential issues and vulnerabilities in the software used for medical imaging processes. Dynamic code testing, on the other hand, involves running the software and examining its behavior in real-time to ensure its functionality and reliability in radiology workflows.
6. AI in Radiology
AI in radiology has revolutionized medical imaging, enhancing diagnostic accuracy and efficiency. Through advanced algorithms, AI assists radiologists in detecting anomalies and expedites patient care. Its integration promises to streamline workflows and improve patient outcomes in diagnostic processes.
Radiologists need to exercise caution with AI, and ensure that it is used to complement rather than replace their expertise, preserving human judgment and empathy in patient care. They need to remain vigilant in validating AI outputs, recognizing its limitations and potential biases to maintain diagnostic accuracy and patient trust.
How databrackets can help you with Security Best Practices for Radiology
The rapid progression of radiology digitization brings forth an expanding realm of risks. Weakly secured systems offer hackers straightforward avenues to exploit vulnerabilities, posing considerable threats to business continuity. With radiology infrastructure often accessible externally, it’s crucial for organizations in this field to continuously bolster their security measures and verify their efficacy. Proactive enhancements in security are imperative to mitigate risks and safeguard the integrity of radiological operations amidst the dynamic digital environment.
The security experts at databrackets bring years of extensive Radiology industry experience to the table, along with a deep understanding of industry-standard security practices. Our Vulnerability Assessment & Pen Testing capabilities have been accredited by the A2LA for ISO 17020 Conformity assessment for inspection bodies. We possess comprehensive knowledge of common pitfalls in system configurations, recognizing factors such as outdated software in medical devices, inadequately configured firewalls, and unpatched systems that often lead to security vulnerabilities. Through meticulous scoping and testing using a variety of tools, we meticulously uncover all potential vulnerabilities visible to attackers, ensuring thorough detection and protection for our clients’ systems and data.
Our client engagement starts with your business objective in mind. Vulnerability Assessment & Pen Testing is requested for several reasons:
- To secure your environment
- To meet certain regulatory compliance or certification requirements
- To fulfill a request made by your customer
- A combination of the reasons mentioned above
Once we understand what you require, our exercise focuses primarily on scoping of the engagement and setting expectations. We use a variety of tools depending on the type of test and systems in which we need to identify vulnerabilities & conduct pen testing. Our process includes:
- Discovery
- Identifying and finalizing assets
- Identifying vulnerabilities
- Exploitation of the vulnerabilities (Pen Testing)
- Validation of the issues identified
- Remediation/Recommendations
- Re-testing
Apart from using the tools best in the industry, we also focus on remediation and retesting of the environment. We just don’t give hundreds of pages of reports without any help to eliminate the risks. We help our clients prioritize the risks based on the context, patch the systems and select security tech, policies and procedures that are considered best practices in their industry. We also set up continuous monitoring after our tests to track any changes to your environment & send you timely alerts.
As we continue to work with our clients, we sharpen our understanding of your specific environment and system. This helps us to design cadence for continuous protection and monitoring using the right tools to ensure continual improvement and proactive identification of issues for the future. You can contact us for a customized quote or schedule a consultation.
You can also meet us in-person at RSNA 2024, at South Hall Level 3 – Booth No. 3174.
databrackets overview
Our team of security experts has supported organizations across a wide variety of industries to align their processes with security frameworks like ISO 27001:2022, SOC 2, HIPAA, 21 CFR Part 11, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC 2.0 etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Related Links:
Technologies To Detect And Prevent Ransomware Attacks
Sources of Ransomware Attacks on Healthcare Systems
What are the new controls added to ISO 27001 in 2022?
How to Select a Security Vendor
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.
Benefits of Pen Testing for Radiology
Radiology organizations handle sensitive medical information and rely heavily on secure digital systems to store and transmit patient data. With the increasing prevalence of cyber threats, ranging from ransomware attacks to data breaches, the need for robust cybersecurity measures is paramount. Penetration testing, or pen testing, is essential for radiology organizations to proactively identify vulnerabilities within their network infrastructure, software systems, and protocols. By simulating real-world cyberattacks, pen testing allows the organization to uncover potential weaknesses in specific areas and in DICOM Images before malicious actors exploit them.
Given the highly sensitive nature of medical data, including imaging scans and patient records, ensuring the integrity, confidentiality, and availability of this information is critical. Pen testing enables radiology organizations to fortify their defenses, mitigate risks, and uphold regulatory compliance, ultimately safeguarding patient privacy and the integrity of healthcare services.
Benefits of Pen Testing for Radiology Organizations
1. Identify Vulnerabilities
Penetration testing helps discover vulnerabilities and weaknesses in radiology systems, such as outdated software, misconfigurations, unpatched systems, or inadequate security controls. This is specifically relevant for Picture Archiving and Communication Systems (PACS), Radiology Information Systems (RIS) and Radiology devices. This information is crucial for Radiology organizations to remediate potential risks before they are exploited by malicious actors.
2. Data Protection
Radiology systems contain sensitive patient data, including medical images and protected health information (PHI). Penetration testing helps ensure the confidentiality, integrity, and availability of this data by identifying and addressing security gaps that could lead to data breaches or unauthorized access.
3. Compliance and Regulation
The healthcare industry, including radiology, is subject to various regulations, such as the Health Insurance Portability and Accountability Act (HIPAA) and FDA Cybersecurity and CFR Part 11 requirements. Penetration testing assists radiology facilities in complying with these regulations by demonstrating a proactive approach to safeguarding patient information and avoiding costly fines associated with data breaches.
By uncovering vulnerabilities and assessing the effectiveness of security controls, regular penetration testing allows radiology departments to strengthen their overall security posture. This includes enhancing network security, access controls, and incident response procedures.
5. Risk Mitigation
Penetration testing provides a valuable tool for risk assessment and management since it highlights actionable insights into potential security risks, allowing healthcare organizations to prioritize and address them accordingly. This risk-based approach helps allocate resources efficiently to reduce the likelihood of security incidents.
6. Realistic Simulation
Penetration tests simulate real-world cyberattacks, helping radiology staff and IT teams understand how attackers may exploit vulnerabilities in their systems. This knowledge is invaluable for proactive threat mitigation and incident response planning.
7. Continuous Improvement
Security is an ongoing process, and penetration testing is a vital part of a healthcare organization’s security lifecycle. Regular testing ensures that security measures are continually evaluated and adjusted to adapt to evolving threats and technology.
8. Trust and Reputation
Maintaining a strong cybersecurity posture in radiology enhances the trust and reputation of healthcare organizations. Patients and partners are more likely to entrust their sensitive information to facilities with a demonstrated commitment to security.
9. Cost Savings
Detecting and proactively addressing vulnerabilities through penetration testing can be more cost-effective than dealing with the aftermath of a successful cyberattack. It can prevent the financial and reputational damage that comes with data breach remediation, legal liabilities, and regulatory fines.
10. Enhanced Patient Care
Ultimately, penetration testing contributes to the overall safety and quality of patient care by minimizing the risks associated with security breaches. Ensuring the integrity and availability of medical imaging systems is crucial for accurate diagnoses and timely treatments.
11. Business Continuity
Radiology plays a critical role in patient care, and any disruption to its operations can have serious consequences. Penetration testing helps ensure the continuity of radiology services by identifying and mitigating potential threats that could lead to downtime or system failures.
12. Detection of Insider Threats
Penetration tests can help detect and address potential insider threats within healthcare organizations. These tests simulate both external and internal threats, allowing organizations to identify any vulnerabilities that could be exploited by malicious employees or contractors.
13. Security Awareness
Penetration testing raises awareness about cybersecurity among radiology IT admin and other healthcare professionals. It emphasizes the importance of adhering to security policies, following best practices, and staying vigilant against potential threats.
Penetration testing for radiology is a proactive security assessment method that provides multiple benefits, including identifying vulnerabilities, protecting patient data, ensuring compliance, and improving the overall security posture of healthcare organizations, ultimately contributing to better patient care and organizational resilience.
How databrackets can help you with Pen Testing for Radiology
The digitization of radiology is advancing rapidly, presenting a growing risk landscape. Systems lacking robust hardening and configuration create ample opportunities for hackers to exploit vulnerabilities using straightforward techniques, potentially causing significant disruptions to business operations. Given the external-facing nature of radiology infrastructure, it is imperative for radiology organizations to consistently invest in fortifying their security posture and validating its effectiveness. Proactive measures in security enhancement are essential to mitigate risks and uphold the integrity of radiological operations amidst the evolving digital landscape.
Security Experts at databrackets
Our Vulnerability Assessment & Pen Testing capabilities have been accredited by the A2LA for ISO 17020 Conformity assessment for inspection bodies. The security experts at databrackets bring years of extensive Radiology industry experience to the table, along with a deep understanding of industry-standard security practices. We possess comprehensive knowledge of common pitfalls in system configurations, recognizing factors such as outdated software in medical devices, inadequately configured firewalls, and unpatched systems that often lead to security vulnerabilities. Through meticulous scoping and testing using a variety of tools, we meticulously uncover all potential vulnerabilities visible to attackers, ensuring thorough detection and protection for our clients’ systems and data.
Our client engagement starts with your business objective in mind. Vulnerability Assessment & Pen Testing is requested for several reasons:
- To secure your environment
- To meet certain regulatory compliance or certification requirements
- To fulfill a request made by your customer
- A combination of the reasons mentioned above
Once we understand what you require, our exercise focuses primarily on scoping of the engagement and setting expectations. We use a variety of tools depending on the type of test and systems in which we need to identify vulnerabilities & conduct pen testing. Our process includes:
- Discovery
- Identifying and finalizing assets
- Identifying vulnerabilities
- Exploitation of the vulnerabilities (Pen Testing)
- Validation of the issues identified
- Remediation/Recommendations
- Re-testing
Apart from using the tools best in the industry, we also focus on remediation and retesting of the environment. We just don’t give hundreds of pages of reports without any help to eliminate the risks. We help our clients prioritize the risks based on the context, patch the systems and select security tech, policies and procedures that are considered best practices in their industry. We also set up continuous monitoring after our tests to track any changes to your environment & send you timely alerts.
As we continue to work with our clients, we sharpen our understanding of your specific environment and system. This helps us to design cadence for continuous protection and monitoring using the right tools to ensure continual improvement and proactive identification of issues for the future. You can contact us for a customized quote or schedule a consultation.
You can also meet us in-person at RSNA 2024, at South Hall Level 3 – Booth No. 3174.
databrackets overview
Our team of security experts has supported organizations across a wide variety of industries to align their processes with security frameworks like ISO 27001:2022, SOC 2, HIPAA, 21 CFR Part 11, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC 2.0 etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Related Links:
Technologies To Detect And Prevent Ransomware Attacks
Sources of Ransomware Attacks on Healthcare Systems
What are the new controls added to ISO 27001 in 2022?
How to Select a Security Vendor
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.
Pen Testing for Radiology
Penetration testing, often referred to as “pen testing” or “ethical hacking,” is a proactive security assessment approach used to identify vulnerabilities and weaknesses within a computer system, network, or application. In the context of radiology, penetration testing is specifically designed to evaluate the security of medical imaging systems, including Picture Archiving and Communication Systems (PACS), Radiology Information Systems (RIS), medical devices and associated network and application infrastructure. The primary goal of penetration testing in radiology is to simulate real-world cyberattacks and assess the system’s ability to withstand and defend against these threats as the Radiology industry increasingly handles sensitive electronic patient data with many partners, vendors and customers.
Areas of Pen Testing for Radiology
There are 4 specific areas of pen testing that are of relevance to organizations that work with medical imaging and radiology. They are:
- Network Testing
- Application Testing
- Mobile App Testing
- IoT Testing

1. Network Testing for Radiology
Radiology organizations operate various external-facing infrastructures essential for engaging with hospitals, referring physicians, and other collaborators. However, the existence of these interfaces poses significant risks to the organization’s security if not adequately fortified. Ensuring the robustness of network security protocols becomes paramount in safeguarding sensitive data and maintaining the integrity of operations. Proactive measures, including comprehensive vulnerability assessment and penetration testing of network systems, are imperative to identify vulnerabilities and implement necessary defenses, thereby mitigating potential breaches and protecting the confidentiality of patient information.
2. Application Testing
Radiology organizations must also prioritize application testing, particularly for Picture Archiving and Communication Systems (PACS), which store vast patient records accessed by numerous radiologists. As part of Vulnerability Assessment and Penetration Testing (VAPT), rigorous evaluation of PACS system infrastructure and applications is essential to verify correct configuration and fortify against potential vulnerabilities. Additionally, given the interconnected nature of many external-facing applications in the radiology domain, comprehensive testing within this context becomes imperative. This includes ensuring the secure implementation of DICOM (Digital Imaging and Communications in Medicine) protocols, which facilitate the exchange of medical images and related information. We conduct a DICOM vulnerability assessment (DVA) to meet this objective. Such assessments serve to identify weaknesses in the system’s architecture and application interfaces, enabling the implementation of robust security measures to safeguard patient data and uphold operational integrity.
3. Mobile App Testing
Mobile applications utilized by radiologists frequently establish connections to backend systems to process and display medical images. However, vulnerabilities within these mobile apps pose a significant risk, potentially compromising the integrity of the backend infrastructure if left unidentified and unaddressed. Therefore, it is crucial to conduct thorough testing of mobile applications to uncover any vulnerabilities promptly and implement necessary fixes. This proactive approach ensures the security and stability of the entire system, safeguarding sensitive medical data and maintaining seamless functionality for healthcare professionals.
In radiology, numerous devices such as CT, MRI, and X-ray machines are connected to the hospital networks or provider systems. Unfortunately, many of these devices run on outdated software and lack regular patches for identified vulnerabilities. Vulnerability Assessment and Penetration Testing (VAPT) play a crucial role in uncovering these issues, providing a structured framework for prioritizing and addressing them. By identifying vulnerabilities in connected radiology devices, VAPT ensures a proactive approach to cybersecurity, mitigating potential risks and enhancing the overall safety and reliability of diagnostic equipment within healthcare settings.
How databrackets can help you with Pen Testing for Radiology
The digitization of radiology is advancing rapidly, presenting a growing risk landscape. Systems lacking robust hardening and configuration create ample opportunities for hackers to exploit vulnerabilities using straightforward techniques, potentially causing significant disruptions to business operations. Given the external-facing nature of radiology infrastructure, it is imperative for radiology organizations to consistently invest in fortifying their security posture and validating its effectiveness. Proactive measures in security enhancement are essential to mitigate risks and uphold the integrity of radiological operations amidst the evolving digital landscape.
Security Experts at databrackets
Our Vulnerability Assessment & Pen Testing capabilities have been accredited by the A2LA for ISO 17020 Conformity assessment for inspection bodies. The security experts at databrackets bring years of extensive Radiology industry experience to the table, along with a deep understanding of industry-standard security practices. We possess comprehensive knowledge of common pitfalls in system configurations, recognizing factors such as outdated software in medical devices, inadequately configured firewalls, and unpatched systems that often lead to security vulnerabilities. Through meticulous scoping and testing using a variety of tools, we meticulously uncover all potential vulnerabilities visible to attackers, ensuring thorough detection and protection for our clients’ systems and data.
Our client engagement starts with your business objective in mind. Vulnerability Assessment & Pen Testing is requested for several reasons:
- To secure your environment
- To meet certain regulatory compliance or certification requirements
- To fulfill a request made by your customer
- A combination of the reasons mentioned above
Once we understand what you require, our exercise focuses primarily on scoping of the engagement and setting expectations. We use a variety of tools depending on the type of test and systems in which we need to identify vulnerabilities & conduct pen testing. Our process includes:
- Discovery
- Identifying and finalizing assets
- Identifying vulnerabilities
- Exploitation of the vulnerabilities (Pen Testing)
- Validation of the issues identified
- Remediation/Recommendations
- Re-testing
Apart from using the tools best in the industry, we also focus on remediation and retesting of the environment. We just don’t give hundreds of pages of reports without any help to eliminate the risks. We help our clients prioritize the risks based on the context, patch the systems and select security tech, policies and procedures that are considered best practices in their industry. We also set up continuous monitoring after our tests to track any changes to your environment & send you timely alerts.
As we continue to work with our clients, we sharpen our understanding of your specific environment and system. This helps us to design cadence for continuous protection and monitoring using the right tools to ensure continual improvement and proactive identification of issues for the future. You can contact us for a customized quote or schedule a consultation.
You can also meet us in-person at RSNA 2024, at South Hall Level 3 – Booth No. 3174.
databrackets overview
Our team of security experts has supported organizations across a wide variety of industries to align their processes with security frameworks like ISO 27001:2022, SOC 2, HIPAA, 21 CFR Part 11, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC 2.0 etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Related Links:
Technologies To Detect And Prevent Ransomware Attacks
Sources of Ransomware Attacks on Healthcare Systems
What are the new controls added to ISO 27001 in 2022?
How to Select a Security Vendor
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.
Pen Testing versus Vulnerability Assessment
Feeling confused about security assessments? Are you unsure if a Vulnerability Assessment or Penetration Test is the right assessment for your organization? While both aim to test your defenses and security postures, they take very different approaches. This blog will untangle the mysteries of Vulnerability Assessments and Penetration Testing, helping you choose the ideal champion to evaluate your security posture.
Vulnerability Assessments (VAs) leverage automated tools to scan for known vulnerabilities in your software and systems. They provide a high-level view of potential issues based on documented weaknesses. This approach is cost-effective and efficient, making it ideal for regular checkups.
Penetration Testing (PT) simulates real-world attacker behavior, actively exploiting existing vulnerabilities to measure their impact. This in-depth assessment reveals how attackers might gain access and cause damage. However, Penetration Tests are more complex, requiring specialized skills and manual effort, leading to higher costs.
Organizations look for these security assessments usually for legal, contractual or regulatory purposes. Once you understand the business objective(s) for your assessment, you can select the right option or probably conduct both tests. However, in our experience as cybersecurity professionals for over 12 years, leveraging the strengths of both VA and PT at different times is ideal for your cybersecurity strategy.
Comparing Pen Testing and Vulnerability Assessment
Vulnerability Assessment and Penetration Testing (Pen Testing) are both critical components of a comprehensive cybersecurity strategy, but they serve different purposes and have distinct methodologies. Here’s a comparison of the two:

1. Purpose
Vulnerability Assessment: The primary goal of a vulnerability assessment is to identify, assess, and categorize vulnerabilities in an organization’s systems, networks, and applications. It focuses on finding weaknesses in the security posture without exploiting them. It aims to provide a snapshot of potential weaknesses that could be exploited by attackers.
Pen Testing: Pen Testing, on the other hand, involves actively simulating real-world cyberattacks to exploit vulnerabilities and determine the extent to which an attacker can gain unauthorized access or compromise systems. The primary purpose is to evaluate an organization’s security posture and measure its ability to withstand attacks if they are attacked.
2. Scope & Frequency of Testing
Vulnerability Assessment: It usually has a broader scope, focusing on identifying as many vulnerabilities as possible, including low-risk ones. It provides a comprehensive list of potential weaknesses.
Pen Testing: Pen testing has a narrower scope and typically focuses on a specific target or set of targets. It aims to demonstrate the impact of exploited vulnerabilities and assess the overall security posture.
3. Methodology
Vulnerability Assessment: It typically involves automated or manual scans of systems and networks to identify known vulnerabilities. The assessment can include vulnerability scanning tools, configuration reviews, and system analysis.
Pen Testing: Pen testing involves ethical hackers (penetration testers) actively trying to exploit vulnerabilities to understand their potential impact and determine if unauthorized access or data breaches are possible. This may include attempting to gain unauthorized access, privilege escalation, social engineering, network probing, data exfiltration, or other attack scenarios.
4. Reporting
Vulnerability Assessment: The output of a vulnerability assessment is a list of identified vulnerabilities, their severity ratings, and recommendations for remediation. It provides a roadmap for improving security but doesn’t include detailed exploitation scenarios.
Pen Testing: Pen testing reports include information on the vulnerabilities exploited, the impact of successful attacks, the techniques used, and recommendations for mitigating the risks. These reports are more in-depth and provide actionable insights based on actual attack simulations.
5. Regulatory Compliance
Vulnerability Assessment: Vulnerability assessments are often almost required to comply with various regulations and standards, such as PCI DSS, ISO 27001, SOC 2, HIPAA, NIST Cybersecurity Framework, NIST 800-171, CMMC 2.0, etc. This is considered as the minimum required security program for several organizations.
Pen Testing: Penetration testing is also required, at times, by regulations and security standards, and it is more focused in the areas where customer data is stored. Organizations in the finance industry, product/cloud companies and the healthcare sector are required to conduct the pen testing as the cost of breaches is too high if the services/products are not secured properly. Pen testing is required in any certification audit including SOC 2 & ISO 27001, apart from several compliance standards including PCI DSS, HIPAA, NIST Cybersecurity Framework, NIST 800-171, CMMC 2.0, etc.
6. Cost & Time
Vulnerability Assessment: Typically carried out through automated processes, this operation can take anywhere from a few hours to several hours to complete. The process, which includes identifying vulnerabilities and validating the results, is generally completed within a few days. The cost for this engagement usually begins at around USD 2,500.
Pen Testing: A considerable amount of work goes into collecting public information, conducting analysis, identifying vulnerabilities, and executing exploitation, including privilege escalation. Depending on the type of penetration testing – whether it’s network, application, or other asset types – the engagement typically spans 2 to 6 weeks. The cost for these services starts at approximately USD 15,000.
7. Benefit to your Cybersecurity Strategy
Vulnerability Assessment: The assessment tells you how your systems are configured and which policies & procedures you need to be changed to enhance security.
Pen Testing: It tells you how secure your systems are and which security controls are not implemented. After a Pen Test, you need to review your security tech & industry-specific best practices.
Do you need Pen Testing and Vulnerability Assessment or just one?
Vulnerability assessments are focused on identifying vulnerabilities, while penetration testing involves actively exploiting these vulnerabilities to assess their real-world impact. Both approaches are valuable in a comprehensive cybersecurity strategy, with vulnerability assessments providing continuous monitoring and early detection of weaknesses and penetration testing helping organizations understand their readiness to defend against sophisticated attacks. Both are valuable tools in a cybersecurity program, and organizations often use a combination of both to strengthen their overall security posture.
Compliance Driven Decisions: If legal, contractual, or regulatory requirements demand specific assessments, you need to follow the mandated standards or clauses.
Understanding Your Needs: If the decision isn’t dictated by external factors, consider your specific needs. Vulnerability Assessments are excellent for regular scanning and identifying broad areas for improvement. They are cost effective and help you categorize vulnerabilities. Pen Testing is invaluable for uncovering deeper vulnerabilities and understanding their real-world consequences.
How databrackets can help you with Vulnerability Assessment & Pen Testing
Our Vulnerability Assessment & Pen Testing capabilities have been accredited by the A2LA for ISO 17020 Conformity assessment for inspection bodies. Our cybersecurity experts have several years of experience helping organizations across industries to meet regulatory and customer requirements.
Our client engagement starts with your business objective in mind. Vulnerability Assessment & Pen Testing is requested for several reasons:
- To secure your environment
- To meet certain regulatory compliance or certification requirements
- To fulfill a request made by your customer
- A combination of the reasons mentioned above
Once we understand what you require, our exercise focuses primarily on scoping of the engagement and setting expectations. We use a variety of tools depending on the type of test and systems in which we need to identify vulnerabilities & conduct pen testing. Our process includes:
- Discovery
- Identifying and finalizing assets
- Identifying vulnerabilities
- Exploitation of the vulnerabilities (Pen Testing)
- Validation of the issues identified
- Remediation/Recommendations
- Re-testing
We conduct a wide variety of Penetration Tests for our clients to evaluate the level of security in the following:
- Internal Network
- External Network
- Web Application
- Mobile Apps
- Cloud Infrastructure
- IoT Devices
Apart from using the tools best in the industry, we also focus on remediation and retesting of the environment. We just don’t give hundreds of pages of reports without any help to eliminate the risks. We help our clients prioritize the risks based on the context, patch the systems and select security tech, policies and procedures that are considered best practices in their industry. We also set up continuous monitoring after our tests to track any changes to your environment & send you timely alerts.
As we continue to work with our clients, we sharpen our understanding of your specific environment and system. This helps us to design cadence for continuous protection and monitoring using the right tools to ensure continual improvement and proactive identification of issues for the future. You can contact us for a customized quote or schedule a consultation.
databrackets overview
Our team of security experts has supported organizations across a wide variety of industries to align their processes with security frameworks like ISO 27001:2022, SOC 2, HIPAA, 21 CFR Part 11, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC 2.0 etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Related Links:
Technologies To Detect And Prevent Ransomware Attacks
Sources of Ransomware Attacks on Healthcare Systems
What are the new controls added to ISO 27001 in 2022?
How to Select a Security Vendor
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.
Transition to ISO 27001:2022
The ISO 27001:2022 certification standard was released in October 2022. It has replaced the ISO 27001:2013 edition via a three-year transition period, which ends on October 31, 2025. Companies with an ISO 27001:2013 certification are required to transition to ISO 27001:2022 by October 31, 2025. All ISO 27001:2013 certifications will expire or be withdrawn at the end of the transition period.
It is imperative for companies to connect with their ISO 27001 Certifying Body to undergo a transition audit and confirm that they comply with the new security requirements applicable to the ISO 27001 standard.
By May 1, 2024, all new certifications must be issued against the ISO 27001:2022 edition by the certifying bodies. After this date, all recertification audits must also utilize the ISO 27001:2022 edition. While there are changes to the list of controls, ISO 27002:2022 also defines a purpose for individual controls to better explain each control’s intent. The options for the existing and new customers are given below.
If you are a current ISO 27001-certified organization:
a) If your full recertification audit is due before May 1, 2024:
-
-
-
- You could continue with the 2013 version
- You could transition to the 2022 version
-
-
b) If your full recertification audit is due after May 1, 2024, you can only be certified against ISO 27001:2022
c) If your surveillance audit is due before Oct 31, 2025
-
-
-
- You have the choice to continue with your 2013 version
- You also have the option to transition to 2022 and get your transition to 2022 audit completed along with your surveillance audit
-
-
d) However, all transition audits to 27001:2022 need to be completed by Oct 31, 2025 from the ISO 27001:2013 version.
If you are considering getting ISO 27001 certified:
-
-
-
- You can get the 2013 version certified until May 1, 2024
- After May 1, 2024 you can get certified only against the 2022 version
-
-
Changes to ISO 27001:2022
A summary of the changes to the ISO 27001 standard are:
Changes have been made to the following requirements:
-
-
-
- 4.2 Understanding the needs and expectations of interested parties
- 4.4 Information Security Management System
- 6.2 Information security objectives and planning to achieve them
- 6.3 Planning of changes
- 8.1 Operational planning and control
- 9.1 Monitoring, measurement, analysis and evaluation
- 9.3.2 Management review inputs
- 10 Improvement
-
-
Annex A controls
-
-
-
- The overall number of controls within Annex A is now 93 compared to the 114 controls in the previous edition.
- They have been regrouped from 14 control objectives to 4 broad themes: Organizational, People, Physical, and Technological Controls.
- Several previous controls have been consolidated into broader new controls, and 11 new controls have been added, including:
-
-
-
-
-
- Threat Intelligence
- Information Security for the use of Cloud Services
- Physical Security Monitoring
- Configuration Management
- Information Deletion
- Data Masking
- Data Leakage Prevention
- Web Filtering
- Secure Coding
-
-
In ISO 27002:2022, there are five control attributes that include:
-
-
-
- Control Type
- Information Security Properties
- Cybersecurity Concepts
- Operational Capabilities
- Security Domains
-
-
Transition Audit Timelines
As per the guidelines of the IAF, certifying bodies are required to ensure their clients are made aware of the Transition Audit timelines as outlined below:
-
-
-
- Minimum of 0.5 auditor days for the transition audit when it is carried out in conjunction with a recertification audit
- Minimum of 1.0 auditor day for the transition audit when it is carried out in conjunction with a surveillance audit or as a separate audit
- When the certification document is updated because the client successfully completes only the transition audit, the expiration of their current certification cycle will not be changed.
- All certifications based on ISO/IEC 27001:2013 shall expire or be withdrawn at the end of the transition period.
-
-
Prepare for your ISO 27001 Transition Audit
B2B contracts that are based on the ISO 27001 standard require clients to maintain the validity of their certification. As per the IAF guidelines, certified organizations have the option to undergo their transition audit while their ISO 27001:2013 certification cycle is valid. When they apply for recertification, they must undergo their certification audit per ISO 27001:2022 edition.
To ensure that you comply with the new controls and documentation requirements, your organization needs to prepare for the transition audit and ensure that your ISMS complies with ISO 27001:2022 controls and processes.
To ensure you are ready for your transition audit, you need to conduct an internal audit for a thorough gap analysis. This can be done with an organization that offers consulting services and is aware of the protocols of the ISO 27001:2022 edition. Organizations that provide consulting services are not authorized to offer certification services.
It is advisable to prepare for your annual surveillance audit along with your transition audit since the IAF guidelines highlight the importance of completing them together before your ISO 27001:2013 certification expires. Preparing for both will also ensure that you are poised to succeed in your recertification audit and maintain your certification status. This will ensure you are compliant with the security requirements of your B2B contracts that rely on it.
Undergo your Transition Audit and ISO 27001:2022 Certification with databrackets
databrackets holds the distinction of being recognized as an authorized certifying body for ISO 27001:2022 by IAS Online. Our certification is consistently renewed as per IAF Guidelines, and it is a testament to our commitment to excellence in information security management.
This prestigious certification signifies that our team of ISO Auditors possesses the expertise, rigor, and credibility to assess and confirm your organization’s compliance with the latest ISO 27001 standards.
Our certification services not only validate that you have implemented robust security measures to protect sensitive data but also provide assurance to stakeholders, clients, and partners that their information assets are in trustworthy hands. Our role as an authorized certifying body highlights our dedication to promoting best practices in data security and helping businesses navigate the complex landscape of information security management.
Contact us to book your transition audit from ISO 27001:2013 to ISO 27001:2022 today!
Related Links:
Technologies To Detect And Prevent Ransomware Attacks
Sources of Ransomware Attacks on Healthcare Systems
What are the new controls added to ISO 27001 in 2022?
How to Select a Security Vendor
Author: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.
Cybersecurity Checklist for 2024
Cybersecurity is a critical concern for organizations in 2024 as the digital landscape continues to evolve and cyber threats become more sophisticated. Though organizations across industries have regulatory requirements related to data privacy and cyber security, attackers have found innovative and manipulative ways around them. As a result, the threat of losing reputation and revenue looms over all organizations.
Cybersecurity Checklist For Organizations in 2024
With over a decade of experience in supporting organizations to meet compliance and cybersecurity requirements, our certified experts have identified critical cybersecurity tips and best practices that organizations should consider protecting their data, systems, and reputation in 2024.

1.Zero Trust Architecture:
Zero Trust is a security framework that assumes no one can be trusted by default, whether inside or outside the organization. It requires verifying identity and continuously monitoring for threats. Adopting Zero Trust principles can help prevent unauthorized access and data breaches.
2. Strong Authentication:
Enforce multi-factor authentication (MFA) for admin accounts, accessing critical systems and data. MFA adds an extra layer of security by requiring users to provide multiple forms of verification, such as a password and a biometric scan or a token.
3. Regular Software Updates and Patches:
Vulnerabilities in outdated software can be exploited by attackers. Ensure that all software, including operating systems, applications, and security solutions, are updated with the latest security patches and updates.
4. Security Awareness Training:
Train your employees on cybersecurity best practices, including recognizing phishing emails, using strong passwords, and reporting suspicious activity. Make them aware of their role in maintaining security.
5. Cloud Security:
If your organization uses cloud services, implement robust security configurations and access controls. Monitor and audit cloud environments for any unusual activity.
6. Network Security:
Employ firewalls, intrusion detection and prevention systems, and robust network segmentation to protect your network from unauthorized access and attacks.
7. Endpoint Security:
Use endpoint protection solutions, such as antivirus software and endpoint detection and response (EDR) tools, to secure endpoint devices like computers and mobile devices.
8. Regular Vulnerability Assessments:
Conduct regular vulnerability assessments and penetration testing to proactively identify and address weaknesses in your systems and applications.
9. Data Encryption:
Encrypt sensitive data at rest and in transit. This provides an additional layer of protection, making it challenging for unauthorized parties to access and read your data, even if they gain access to it.
10. Incident Response Plan:
Develop and regularly update an incident response plan that outlines the steps to take in the event of a cyberattack. Test this plan through simulated exercises to ensure your team knows how to respond effectively.
11. Third-Party Risk Management:
Assess the cybersecurity practices of third-party vendors and service providers with access to your data or systems. Ensure they meet your security standards and have strong cybersecurity measures in place.
12. Continuous Monitoring:
Implement continuous monitoring solutions to detect and respond to threats in real-time. This can include Intrusion Detection Systems (IDS), Security Information and Event Management (SIEM) tools, and Endpoint Detection and Response (EDR) solutions.
13. Backup and Disaster Recovery:
Regularly back up critical data and systems and establish a robust disaster recovery plan. Ensure that backups are stored securely and can be quickly restored in case of data loss or ransomware attacks.
14. Business Continuity Plan:Implement and test your business continuity plan in case of a ransomware attack or data loss.
15. Regulatory Compliance:
Stay current with your industry and region’s cybersecurity regulations and compliance requirements. Ensure your organization complies with these standards to avoid legal and financial penalties.
16. Culture of Cybersecurity:
Foster a culture of cybersecurity within your organization. Encourage employees to be vigilant and report security incidents promptly. Make cybersecurity a shared responsibility across all departments.
17. Threat Intelligence:
Stay informed about emerging cyber threats and trends by subscribing to threat intelligence services. This can help you anticipate and prepare for potential threats.
18. Secure Remote Work:
Ensure that remote access solutions are safe and employees’ home networks are protected. Use VPNs, secure video conferencing tools, and encrypted communication channels.
19. Mobile Device Management (MDM):
If employees use mobile devices, implement MDM solutions to enforce security policies, remote wipe capabilities, and application whitelisting.
20. Employee Offboarding Procedures:
Have clear procedures for revoking access and collecting company assets when employees leave the organization. Ensure all cloud-based application access is revoked properly.
21. Supply Chain Security:
Assess and secure your supply chain, as vulnerabilities in your suppliers’ systems can indirectly affect your organization.
22. Board and Executive Involvement:
Ensure that cybersecurity is a priority at the board and executive levels, with regular reporting on security posture and risks.
23. Secure Access Service Edge (SASE):
SASE simplifies and enhances cybersecurity by integrating network and security functions, providing a unified and cloud-native approach to protect data and users across a distributed network.
24. Single Sign-On (SSO):
SSO enhances cybersecurity by enabling users to access multiple systems and applications with a single set of credentials, reducing the risk of password-related vulnerabilities.
Cybersecurity is an ongoing process, and adapting to evolving threats and technologies is crucial. You need to regularly assess and update your cybersecurity strategy to stay ahead of cybercriminals and protect your organization’s assets. One way to ensure you are making the right choices for your organization is to undergo a Security Risk Analysis to detect areas of improvement and work with a CISO or vCISO to design a comprehensive cybersecurity strategy.
How databrackets can help you with Security Hardening Initiatives
Experts at databrackets have extensive experience working with clients across a variety of industries. We have customized services to help you detect and prevent Ransomware. They include:
- Security Tech Consulting: Our certified experts understand your risk exposure and recommend best-in-class tools to mitigate the risks.
- Customized Policies and Procedures: Based on our assessment and after understanding your processes and procedures, we leverage our extensive policy templates and customize them for your organization.
- Customized Training: We customize our training content based on the roles in your organization and your existing procedures.
- Regular Compliance Audits: We conduct regular audits to support your business requirements for periodic regulatory and customer-contract based evaluation.
- Regular Vulnerability Scans and Pen Testing: We conduct Vulnerability Scans and Third party Pen Testing periodically.
- Managed Security Services: We offer managed compliance and security services to continuously monitor and update your security team about your security posture.
- Backups & Disaster recovery: We help you design a plan & implement solutions for Business Continuity.
Our team has supported organizations across a wide variety of industries to align their processes with security frameworks like HIPAA, 21 CFR Part 11, ISO 27001:2022, SOC 2, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Related Links:
Technologies To Detect And Prevent Ransomware Attacks
Sources of Ransomware Attacks on Healthcare Systems
What are the new controls added to ISO 27001 in 2022?
How to Select a Security Vendor
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.
How to Prevent the Impact of Ransomware
Verizon’s Data Breach Investigations Report found that 74% of all breaches were a result of human error due to social engineering. This statistic is based on the analysis of 16,312 security incidents and 5,199 breaches. This report puts Ransomware as the cause of 24% of all breaches. It also puts the cost of 95% of all security incidents at $1 million – $2.25 million dollars. Apart from Ransomware, the report states that a variety of different techniques were used to gain entry to an organization, such as exploiting vulnerabilities (5%), phishing (12%), and using stolen credentials (49%).
With over a decade of experience in supporting organizations to meet compliance and cybersecurity requirements, our certified experts have recommended a 2 pronged approach to preventing the devastating impact of Ransomware. It involves using Security Tech with Security Policies and Procedures. This approach is useful against all cyber attacks and data breaches and is in keeping with industry best practices. Before you select Security Tech for your organization, we recommend undergoing a Security Risk Analysis to detect areas of improvement and work with a CISO or vCISO to design a comprehensive cybersecurity strategy.
Preventing the devastating impact of Ransomware has 2 essential elements
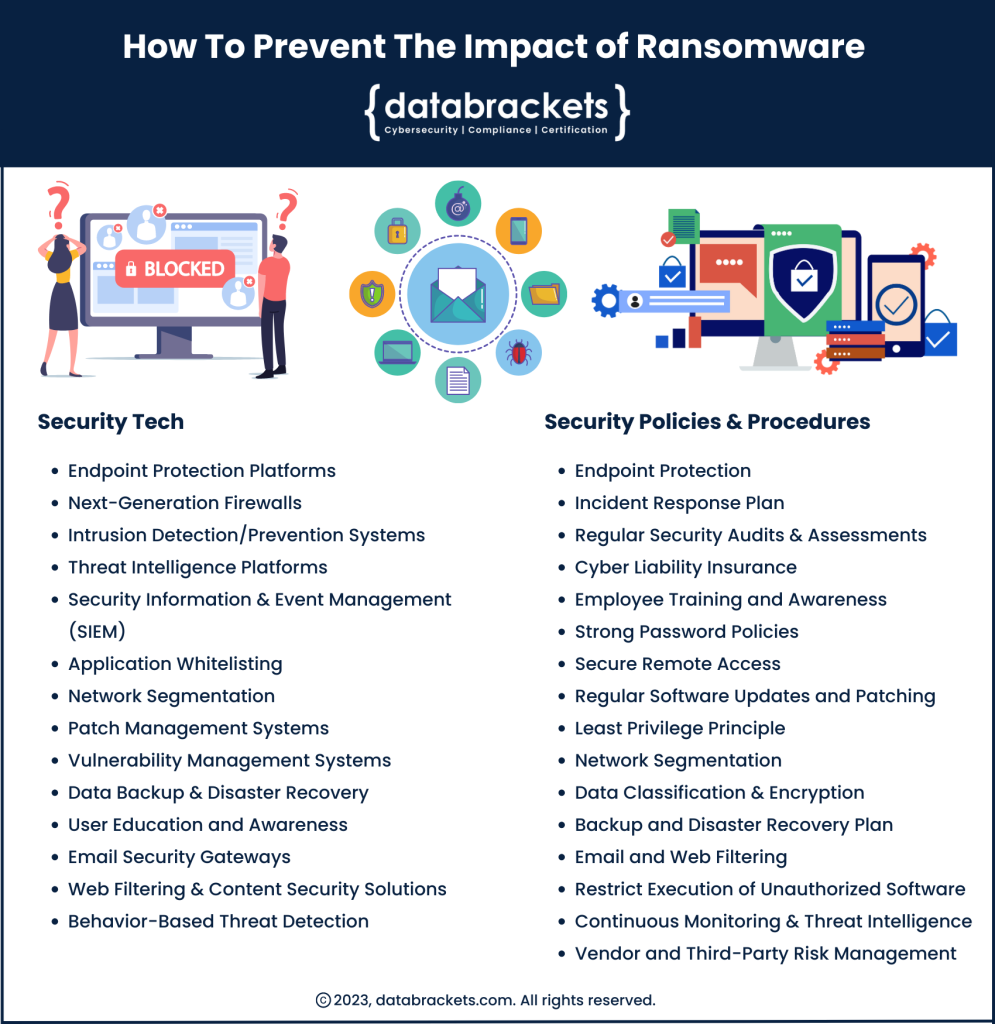
1. Security Tech
2. Security Policies and Procedures
To prevent the impact of ransomware, you need to ensure your cyber security strategy has a perfect sync between these elements. In the infographic above, you will notice several duplications. Organizations need to implement security tech and embed their usage into their security policies and procedures to complete the cycle. By training employees, personnel on contract and vendors who work with sensitive information, you can ensure that potential loopholes are plugged before they can be exploited by hackers.
Explore details of security tech and vendors whom we trust in our previous blog – Technologies To Detect And Prevent Ransomware Attacks. In this blog, we will focus on the second element.
Security Policies and Procedures to Prevent Ransomware
Here are several ways organizations can prevent ransomware through their policies and procedures:
1. Endpoint Protection:
Most ransomware attacks stem from end devices such as laptops, desktops, and mobile devices linked to the organization’s network Implement robust endpoint security solutions, including antivirus and anti-malware software, host-based intrusion detection systems (HIDS), and endpoint detection and response (EDR) tools on all devices connected to the network. These tools can detect and block malicious activities and provide real-time threat intelligence. Regularly update and monitor these solutions to detect and block ransomware threats.
2. Incident Response Plan:
If you fail to plan, you plan to fail. Develop a comprehensive incident response plan that outlines the steps to be taken in case of a ransomware attack. The plan should include roles and responsibilities, communication procedures, and steps for isolating and containing the infection. It should also include backup restoration processes, contact information for relevant stakeholders, notifying appropriate personnel, and engaging with law enforcement, if necessary.
3. Regular Security Audits and Assessments:
Conduct periodic security audits and assessments, including vulnerability scans and penetration tests, to identify and address potential weaknesses in the organization’s security infrastructure. This is critical since the security posture of modern day organizations changes very fast. This helps identify vulnerabilities that could be exploited by the most recent ransomware attackers. It also helps organizations design initiatives for proactive remediation and continuous improvement of security controls.
4. Cyber Liability Insurance:
Consider obtaining Cyber Liability Insurance coverage to help mitigate the financial impact of a ransomware attack. Review the policy terms and conditions carefully to understand what is covered and ensure it aligns with the organization’s specific needs.
5. Employee Training and Awareness:
Educate employees about the risks of ransomware and provide regular training on best practices for email and internet usage. This includes recognizing suspicious links and attachments, following safe browsing practices, avoiding clicking on unknown links, being cautious about downloading files from untrusted sources, practicing good password hygiene and how to identify and respond to potential ransomware threats. This helps create a security-conscious culture within the organization.
6. Strong Password Policies:
Enforce strong password policies that require employees to use complex, unique passwords and change them regularly. Multi-factor authentication (MFA) should also be implemented to add an extra layer of security. Encourage the use of password managers to ensure unique and secure passwords for each account.
7. Secure Remote Access:
Establish strict policies for remote access to organizational systems and data. This may include the use of virtual private networks (VPNs), multi-factor authentication (MFA) to authenticate remote users and other secure remote desktop protocols. Remote access should only be granted to authorized personnel and with appropriate security measures in place. This prevents attackers from exploiting weak or unsecured remote connections.
8. Regular Software Updates and Patching:
Maintain an up-to-date inventory of software and systems. Develop a policy that mandates the timely installation of security patches and updates for operating systems, software applications, and network devices. Many ransomware attacks exploit known vulnerabilities that can be mitigated by keeping software up to date.
9. Least Privilege Principle:
Implement the principle of least privilege, where employees are only given the access rights necessary to perform their job functions. Restricting access limits the impact of a ransomware attack by minimizing the number of systems and data that can be compromised.
10. Network Segmentation:
Ensure that your IT Team or your MSP divides the network into separate zones based on user roles, functions, and levels of sensitivity. Implement firewalls and access controls to restrict unauthorized access. This helps contain the spread of ransomware within the network and minimizes the potential damage caused by an attack.
11. Data Classification and Encryption:
Develop a data classification policy to categorize data based on its sensitivity and importance. Encrypt sensitive data at rest and in transit to protect it from unauthorized access, even if a ransomware attack occurs.
12. Backup and Disaster Recovery Plan:
Implement a robust backup strategy that includes regular and automated backups of critical data and systems. Store backups offline or in a separate, secure network at an isolated location to prevent ransomware from encrypting them. Develop a comprehensive disaster recovery plan to restore systems and data in the event of a ransomware attack. Test the backups periodically to ensure their integrity and reliability.
13. Email and Web Filtering:
Implement email and web filtering solutions that can identify and block malicious content, including phishing emails, attachments and websites distributing ransomware. These solutions can help prevent employees from inadvertently accessing malicious links or downloading infected files. Regularly update and configure these filters to enhance their effectiveness.
14. Restrict Execution of Unauthorized Software: Implement strict policies that restrict the execution of unauthorized or unknown software. This can be achieved through application whitelisting or using secure application sandboxing techniques.
15. Continuous Monitoring and Threat Intelligence:
Deploy robust monitoring systems to detect and respond to potential ransomware threats in real-time. Stay updated with the latest threat intelligence and information sharing initiatives to proactively defend against emerging threats. One solution that merges this with compliance and regulatory requirements is to use continuous compliance-based monitoring. This practice is subscription based and it monitors how well your security controls are functioning in real-time with regard to regulatory and compliance benchmarks.
16. Vendor and Third-Party Risk Management:
Implement a robust vendor and third-party risk management program to ensure that external partners and suppliers maintain adequate security measures. Ensure that they adhere to proper security standards to minimize the risk of ransomware infiltrating the organization through external connections This includes assessing their security practices, contractual obligations, and conducting regular audits.
By implementing these best practices, organizations can significantly reduce the risk of ransomware attacks and minimize the potential impact of any successful attempts. However, it’s important to note that cybersecurity is an ongoing process, prevention measures alone may not guarantee 100% security, and organizations should continuously adapt and improve their defenses to keep up with evolving threats.
How databrackets can help you prevent Ransomware
Experts at databrackets have extensive experience working with clients across a variety of industries. We have customized services to help you detect and prevent Ransomware. They include:
- Security Tech Consulting: Our certified experts understand your risk exposure and recommend best-in-class tools to mitigate the risks.
- Customized Policies and Procedures: Based on our assessment and after understanding your processes and procedures, we leverage our extensive policy templates and customize them for your organization.
- Customized Training: We customize our training content based on the roles in your organization and your existing procedures.
- Regular Compliance Audits: We conduct regular audits to support your business requirements for periodic regulatory and customer-contract based evaluation.
- Regular Vulnerability Scans and Pen Testing: We conduct Vulnerability Scans and Third party Pen Testing periodically.
- Managed Security Services: We offer managed compliance and security services to continuously monitor and update your security team about your security posture.
- Backups & Disaster recovery: We help you design a plan & implement solutions for Business Continuity.
Our team has supported organizations across a wide variety of industries to align their processes with security frameworks like HIPAA, 21 CFR Part 11, ISO 27001:2022, SOC 2, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Related Links:
Technologies To Detect And Prevent Ransomware Attacks
Sources of Ransomware Attacks on Healthcare Systems
What are the new controls added to ISO 27001 in 2022?
How to Select a Security Vendor
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.
Technologies To Detect And Prevent Ransomware Attacks
Verizon’s Data Breach Investigations Report puts the cost of 95% of security incidents at $1 million – $2.25 million dollars. The report is based on the analysis of 16,312 security incidents and 5,199 breaches. They found 74% of all breaches to be a result of human error due to social engineering. In terms of cyberattack methods, Ransomware constitutes 24% of all breaches and its popularity has been growing rapidly over the last few years. The report states that a variety of different techniques were used to gain entry to an organization, such as exploiting vulnerabilities (5%), phishing (12%), and using stolen credentials (49%). Following industry best practices and protocols is recommended by the analysts to safeguard organizations against breaches.
With over a decade of experience in supporting organizations to meet compliance and cybersecurity requirements, our certified experts have identified various technologies to prevent ransomware attacks and enhance your cybersecurity posture. These are in keeping with industry best practices. We have also identified vendors with a successful track record and shared the list in the table below. The price point of implementing these technologies varies depending on your set-up. One way to ensure you are making the right choices for your organization is to undergo a Security Risk Analysis to detect areas of improvement and work with a CISO or vCISO to design a comprehensive cybersecurity strategy.
It’s important to note that while technology plays a significant role in preventing ransomware attacks, a comprehensive cybersecurity strategy should also include regular software updates, strong access controls, robust security policies, incident response plans, penetration testing and ongoing monitoring and assessment of security measures.
Security Tech To Prevent Ransomware Attacks And Enhance Your Cybersecurity Posture

1. Endpoint Protection Platforms (EPP):
Most ransomware attacks stem from end devices such as laptops, desktops, and mobile devices linked to the organization’s network. EPP solutions are designed to secure individual endpoints such as laptops, desktops, and mobile devices. They provide antivirus, anti-malware, host-based intrusion detection/prevention systems and behavioral analysis capabilities using artificial intelligence to detect and block ransomware threats. EPPs often include features like real-time scanning, heuristic analysis, and threat detection and prevention. They scan files and processes in real-time, identify known threats, and block or quarantine infected files.
2. Next-Generation Firewalls (NGFW):
NGFWs combine traditional firewall capabilities with advanced security features. They use deep packet data inspection, application awareness, and intrusion prevention systems (IPS) to identify and block malicious traffic that may carry ransomware payloads. They often integrate threat intelligence feeds to stay updated on the latest ransomware signatures and indicators of compromise. NGFWs can also enforce policies for network segmentation and user access control.
3. Intrusion Detection/Prevention Systems (IDS/IPS):
IDS and IPS solutions monitor network traffic for potential security breaches and malicious activities. They can detect and block ransomware-related network communications, such as command-and-control (C2) traffic or attempts to exploit vulnerabilities. IDS provides real-time alerts for suspicious network events, while IPS actively blocks or mitigates potential threats. They can help detect and prevent ransomware attacks from spreading across the network.
4. Threat Intelligence Platforms:
Threat intelligence platforms collect and analyze data from various sources to identify emerging threats, including new variants of ransomware. By leveraging threat intelligence, organizations can proactively update their security measures and stay ahead of evolving ransomware threats.
5. Security Information and Event Management (SIEM):
SIEM tools collect and analyze security event logs from various sources, such as firewalls, network devices, endpoints, and servers. By correlating and analyzing this data, SIEM solutions can detect and alert organizations about potential ransomware attacks. They can identify patterns indicative of ransomware attacks and trigger real-time alerts for immediate action. They provide centralized visibility into security events, facilitate incident response, and enable proactive threat hunting.
6. Application Whitelisting:
Application whitelisting involves allowing only authorized applications to run on systems, blocking any unauthorized or malicious software, including ransomware. This approach prevents the execution of unknown or suspicious programs and restricts the ability of ransomware to infiltrate the network.
7. Network Segmentation:
Network segmentation involves dividing a network into smaller multiple isolated subnetworks, typically based on user roles. By segregating critical assets and limiting lateral movement, implementing firewalls and access controls to restrict unauthorized access, even if one segment gets compromised by ransomware, it won’t easily spread to other parts of the network. This strategy helps contain and mitigate the impact of ransomware attacks.
8. Patch Management Systems:
Regularly updating software and operating systems is crucial for preventing ransomware attacks. Patch management systems automate the process of identifying, deploying and verifying patches security patches. This ensures that systems are up to date and protected against known vulnerabilities. Automating this process reduces the chances of exploitation by ransomware or other malware that target known weaknesses.
9. Vulnerability Management Systems:
Regularly scanning and patching systems and software is essential to prevent ransomware attacks that exploit known vulnerabilities. Vulnerability management systems help identify vulnerabilities, prioritize their remediation, and ensure systems are up to date with the latest patches.
10. Data Backup and Disaster Recovery:
While they do not directly prevent a ransomware attack, having robust backup and disaster recovery solutions are essential for recovering from ransomware attacks. Regularly backing up critical data and ensuring its integrity allows organizations to restore their systems to a clean state in the event of a ransomware attack, without paying the ransom. Offline or off-site backups (isolating backups from the main network), using reliable backup solutions that enable fast recovery are particularly important to prevent ransomware from encrypting backup data, restoring their data quickly and minimizing downtime.
11. User Education and Awareness:
Educating employees about ransomware threats, best security practices, and how to identify and report suspicious emails or websites through regular security awareness programs can significantly reduce the risk of successful attacks. This is a critical investment in protecting your organization from security incidents and ensuring that your security tech is used appropriately.
12. Email Security Gateways:
Ransomware is commonly delivered through phishing emails or malicious attachments. Email security gateways employ advanced filtering techniques, including content analysis, spam detection, and URL reputation checks, to block malicious emails before they reach users’ inboxes.
13. Web Filtering and Content Security Solutions:
Web filtering technologies and content security solutions can filter internet traffic and prevent users from accessing malicious websites or downloading infected files. By leveraging URL filtering, reputation checks, and content analysis, these solutions can block known ransomware distribution channels, prevent accidental downloads and reduce the risk of employees inadvertently falling victim to phishing attacks.
14. Behavior-Based Threat Detection:
Advanced security solutions employ behavior-based analytics to detect ransomware attacks based on abnormal system or user behavior. By analyzing patterns, file access permissions, and file modifications, these solutions can identify ransomware activity that might not be caught by traditional signature-based detection methods.
Security Tech Vendors
Sr. No. | Security Tech | Vendors |
|---|---|---|
1 | Endpoint Protection Platforms (EPP) | Crowdstrike, Sentinel One |
2 | Next-Generation Firewalls (NGFW) | Palo Alto Networks, Fortinet |
3 | Intrusion Detection/Prevention Systems (IDS/IPS) | Cisco, Fortinet |
4 | Threat Intelligence Platforms | Crowdstrike, Palo Alto Networks, Cisco Talos |
5 | Security Information and Event Management (SIEM) | Securonix, Splunk, MS Azure Sentinel |
6 | Application Whitelisting | (Included in NGFW) |
7 | Patch Management Systems | MS SCCM, Managengine, N-Able |
8 | Vulnerability Management Systems | Qualys, Nessus |
9 | Data Backup | Arcserve, Veeam, Carbonite |
10 | User Education and Awareness | KnowB4 |
11 | Email Security Gateways | Proofpoint |
12
| Web Filtering and Content Security Solutions | Checkpoint, Cisco |
13 | Behavior-Based Threat Detection | Crowdstrike, Cisco |
Disclaimer: We have recommended these vendors based on years of consulting experience. No other parameters have been considered for this list.
It’s important to note that while these technologies can significantly enhance an organization’s security posture, a holistic approach that includes user education, security policies, and incident response planning is necessary to effectively combat ransomware threats.
How databrackets can help you prevent Ransomware
Experts at databrackets have extensive experience working with clients across a variety of industries. We have customized services to help you detect and prevent Ransomware. They include:
- Security Tech Consulting: Our certified experts understand your risk exposure and recommend best-in-class tools to mitigate the risks.
- Customized Policies and Procedures: Based on our assessment and after understanding your processes and procedures, we leverage our extensive policy templates and customize them for your organization.
- Customized Training: We customize our training content based on the roles in your organization and your existing procedures.
- Regular Compliance Audits: We conduct regular audits to support your business requirements for periodic regulatory and customer-contract based evaluation.
- Regular Vulnerability Scans and Pen Testing: We conduct Vulnerability Scans and Third party Pen Testing periodically.
- Managed Security Services: We offer managed compliance and security services to continuously monitor and update your security team about your security posture.
- Backups & Disaster recovery: We help you design a plan & implement solutions for Business Continuity.
Our team has supported organizations across a wide variety of industries to align their processes with security frameworks like HIPAA, 21 CFR Part 11, ISO 27001:2022, SOC 2, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Related Links:
What are the new controls added to ISO 27001 in 2022?
How to Select a Security Vendor
Sources of Ransomware Attacks on Healthcare Systems
Can you have a Ransomware attack if you are HIPAA-compliant?
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.
Can you have a Ransomware attack if you are HIPAA-compliant?
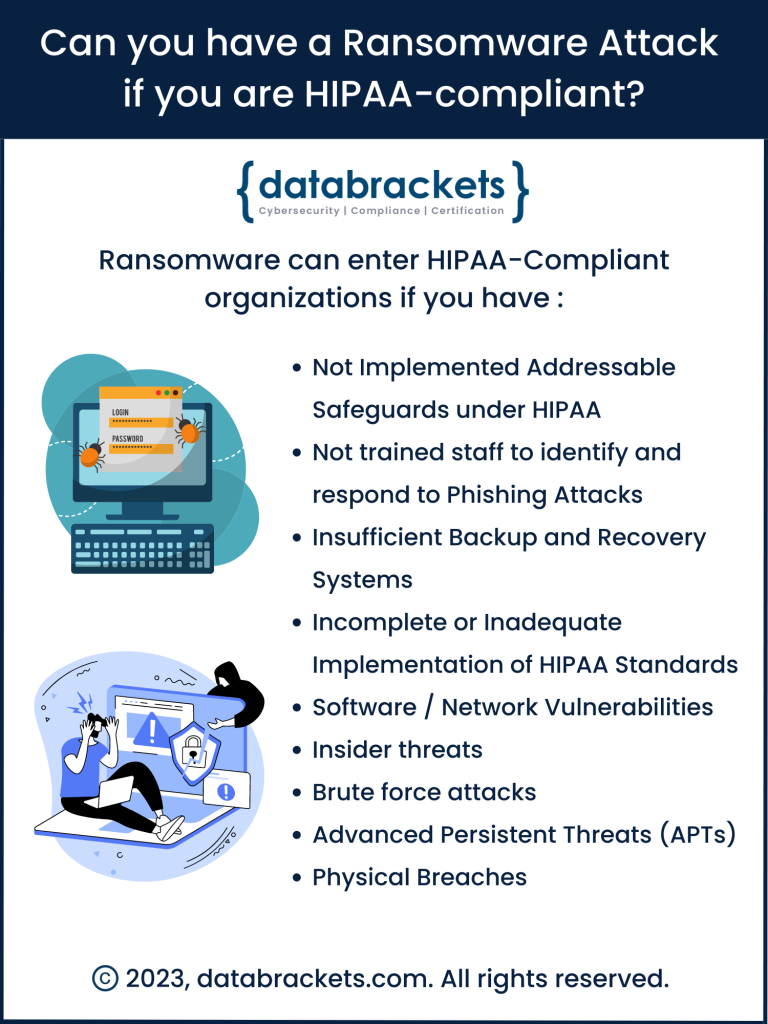 The short answer: Yes
The short answer: Yes
The in-depth answer: The Health Insurance Portability and Accountability Act (HIPAA) sets the minimum standards for protecting sensitive patient health information (PHI). The Department of Health and Human Services (HHS) regulates HIPAA compliance, while the Office for Civil Rights (OCR) enforces it. The OCR regularly publishes recommendations on new issues affecting healthcare and investigates common HIPAA violations on a regular basis. However, a HIPAA-compliant organization can still be a target for a ransomware attack. Despite having advanced cybersecurity measures in place to comply with HIPAA, no organization is fully impervious to all cyber threats.
Ransomware Attacks in a HIPAA-compliant Organization
HIPAA regulations mandate that healthcare providers protect the privacy and security of patient’s health information. This involves implementing safeguards such as access controls, audit controls, integrity controls, and transmission security. However, these measures primarily focus on ensuring data privacy and security, and although they can help reduce the risk of ransomware attacks, they do not eliminate it completely.
Ransomware is malicious software that encrypts the victim’s data. Hackers demands a ransom to restore access to the data once they are paid. They also have the ability to modify the data and sell it, even if they are paid the ransom amount. This leads to serious complications in the Healthcare Industry since their data is targeted due to its critical importance for its high value. Even with HIPAA-compliant measures in place, organizations can fall victim to ransomware attacks via various methods:
-
Not implementing addressable safeguards:
Organizations tend to overlook implementing addressable safeguards outlined in the HIPAA Security Rule. These safeguards focus on Authorization / Supervision, Workforce Clearance Procedures, Termination Procedures, Access Authorization, Security Reminders, Log-in Monitoring, Password Management, Protection from Malicious Software, Testing Contingency Plans, etc. Due to this oversight, their systems have vulnerabilities that can be exploited through a targeted cyber attack.
-
Phishing attacks:
One of the most common ways attackers can breach security defenses is through phishing emails. These emails trick employees into clicking on malicious links or attachments that install ransomware on the network.
-
Insufficient Backup and Recovery Systems:
HIPAA requires that covered entities have backup and disaster recovery measures in place. However, if these measures are not adequately and continuously maintained, tested, and updated, ransomware can infect not only the primary data systems but also backup systems, making data recovery impossible without paying the ransom.
-
Incomplete or Inadequate Implementation of HIPAA Standards:
Compliance doesn’t always mean complete protection. Organizations may meet the letter of the law without effectively securing all possible points of vulnerability. For instance, they might overlook the security of medical devices, partner networks, or other systems that connect to their main network.
-
Exploiting software vulnerabilities:
Cybercriminals often exploit known vulnerabilities in software applications that are not patched or updated regularly. Through these vulnerabilities, they gain unauthorized access and deploy ransomware.
-
Insider threats:
Employees, vendors, or other insiders with malicious intent or those who are simply careless may inadvertently expose the organization to ransomware attacks deliberately.
-
Brute force attacks:
In this method, attackers try numerous combinations to guess passwords and gain access to systems or networks. Once they are in, they install ransomware and infiltrate the entire network.
-
Advanced Persistent Threats (APTs):
These are long-term targeted attacks where cybercriminals infiltrate networks to mine data or disrupt services. They can plant ransomware and activate it at the most opportune moment. For example, zero-day exploits take advantage of security vulnerabilities that are unknown to the organization and the public. Such vulnerabilities are thus unpatched, making them a lucrative target for attackers.
-
Network vulnerabilities:
Weaknesses in network security, such as unsecured Wi-Fi networks or inadequate firewall protection, can create entry points for ransomware.
-
Physical breaches:
Access to physical machines (like a stolen laptop that has not been encrypted) can also lead to a breach. HIPAA requires physical safeguards, but like all security measures, they’re not 100% foolproof.
This list is not exhaustive, and HIPAA compliance can help mitigate these risks through required security measures like regular risk assessments, encryption of electronic protected health information (ePHI), maintaining updated and patched systems, and conducting regular staff training on cybersecurity best practices.
However, the cyber security challenges that organizations face are dynamic. They need a comprehensive approach to cybersecurity that goes beyond just HIPAA compliance. This might involve extensive and customized employee training to recognize phishing attempts, regular audits, and penetration tests to identify and patch vulnerabilities, the use of advanced threat detection and response systems, and robust, isolated backup systems to ensure data can be restored in the event of a ransomware attack. In addition, establishing an incident response plan can help minimize damage if an attack occurs.
Despite all these measures, it’s important to remember that no organization can be completely immune to ransomware attacks. Therefore, continuous improvement of your security posture and preparedness for potential attacks is critical.
In the event of a ransomware attack, HIPAA mandates specific steps and reporting procedures, including notifying affected individuals, the Department of Health and Human Services, and potentially the media depending on the scale of the breach. Therefore, compliance does not guarantee the prevention of attacks, but it does establish a strong foundation for preventing, detecting, and responding to such cyber threats, thereby reducing the possibility of risks in the long run.
How databrackets can help you create a secure IT infrastructure
Experts at databrackets have extensive experience working with Healthcare Providers, Cyber Liability Insurance Providers, Managed Service Providers (MSPs), FDA Regulated industries etc. Our services range from Security Risk Analysis, HIPAA compliance, Pen Testing & Vulnerability Scans, Implementation of Cyber Security Technology, Managed Security Services, and Security Risk Analysis for MIPS, among others.
Our team has supported organizations across a wide variety of industries to align their processes with security frameworks like HIPAA, 21 CFR Part 11, ISO 27001, SOC 2, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Related Links
Sources of Ransomware Attacks on Healthcare Systems
Protect your DICOM from Cyber Attacks
Security Tech Investments for Top 10 trends in 2023
How to Select a Security Vendor
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.
Experts at databrackets have extensive experience working with Healthcare Providers, Cyber Liability Insurance Providers, Managed Service Providers (MSPs), FDA Regulated industries etc. Our services range from Security Risk Analysis, HIPAA compliance, Pen Testing & Vulnerability Scans, Implementation of Cyber Security Technology, Managed Security Services, and Security Risk Analysis for MIPS, among others.
Our team has supported organizations across a wide variety of industries to align their processes with security frameworks like HIPAA, 21 CFR Part 11, ISO 27001, SOC 2, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.