In today’s competitive landscape, demonstrating robust security practices is no longer a nicety; it’s a necessity. Achieving SOC 2 certification by an independent third-party auditor is a powerful way to showcase your commitment to data security and gain a strategic edge. However, navigating the complexities of the SOC 2 journey can feel daunting. Here’s where a SOC 2 compliance readiness partner steps in. A SOC 2 readiness partner acts as your trusted guide, providing the expertise and support you need to achieve compliance efficiently and effectively.
Working with a SOC 2 Compliance Readiness Partner not only provides reasonable assurance to achieve your SOC 2 compliance but also prepares your organization for a SOC 2 Audit. The SOC 2 Audit is part of a SOC 2 Examination, which results in a SOC 2 Report. While this is not technically a certification process, it is often referred to as one because of the impartiality of the SOC 2 auditor, the thoroughness of their evaluation, and the details in their SOC 2 Report. A favorable SOC 2 Report proves your compliance with AICPA‘s Trust Services Criteria and helps you unlock the doors to new business, check many of the RFP (Request For Proposal) requirements, strengthen client trust and, ultimately, accelerate your revenue growth.
Security experts at databrackets have supported various clients as their SOC 2 Compliance Readiness Partner. We have worked with SaaS Providers, MSPs, Start-ups, Healthcare Providers, Radiology Organizations, Pharmaceutical Companies, Financial Services & Accounting Firms, Law Firms, Insurance Firms, etc. Our experience across industries has been possible because of our customized approach and focus on evidence collection and documentation, which CPAs need during a SOC 2 Audit. We have worked closely with various CPA partner firms and ensure they receive documentation in a systematic manner through dbACE, our GRC Platform. Additionally, clients have the option to engage their own CPA firm for their SOC 2 Examination, with databrackets serving as their readiness partner.
Benefits of working with a SOC 2 Compliance Readiness Partner
Engaging a readiness partner before undergoing a SOC 2 audit can be highly beneficial for organizations. Here are several reasons why:

1. Expert Guidance
A readiness partner brings expertise in SOC 2 compliance and understands the intricacies of the audit process. They can provide invaluable guidance on interpreting SOC 2 Trust Service Criteria (TSC), implementing required controls, and preparing documentation to meet audit requirements.
2. Efficiency
By working with a readiness partner, organizations can streamline their SOC 2 compliance efforts. The partner helps identify gaps and weaknesses in controls early on, allowing the organization to address them proactively before the audit. This can save time and resources during the audit process.
3. Risk Mitigation
SOC 2 compliance is about ensuring the security, availability, processing integrity, confidentiality, and privacy of data. A readiness partner helps organizations identify and mitigate risks in these areas, reducing the likelihood of audit findings and non-compliance issues.
4. Tailored Approach
Every organization is unique, with different business processes, systems, and risk profiles. A readiness partner tailors their approach to the specific needs and circumstances of the organization, ensuring that compliance efforts are aligned with its objectives and operational realities.
5. Preparation for Audit Success
Engaging a readiness partner increases the likelihood of a successful SOC 2 audit outcome. By thoroughly assessing readiness, addressing deficiencies, and providing ongoing support, the partner helps the organization demonstrate its commitment to compliance and readiness to auditors.
SOC 2 compliance is increasingly becoming a prerequisite for business, especially in industries dealing with sensitive data. By achieving SOC 2 compliance with the help of a readiness partner, organizations enhance their reputation and instill confidence among customers, partners, and stakeholders.
Having a readiness partner before undergoing a SOC 2 audit can significantly improve the organization’s readiness, efficiency, and overall success in achieving compliance. By leveraging their expertise and support, organizations can navigate the complexities of SOC 2 compliance more effectively and position themselves for long-term security and regulatory compliance.
Role of a SOC 2 Compliance Readiness Partner
A SOC 2 Readiness Partner plays a crucial role in assisting organizations in preparing for a System and Organization Controls (SOC) 2 audit. SOC 2 audits are performed to assess the effectiveness of controls related to security, availability, processing integrity, confidentiality, and privacy of data within service organizations. Here are the tasks typically performed by a SOC 2 Readiness Partner:

1. Initial Consultation and Scoping
The Readiness Partner begins by understanding the organization’s business objectives, services provided, and the scope of the audit. They then work closely with the organization’s stakeholders to identify critical systems, processes, and data flows that need to be evaluated for SOC 2 compliance.
The Readiness Partner educates the client on the requirements and expectations of SOC 2 compliance and provides guidance on interpreting SOC 2 Trust Services Criteria (TSC)and standards applicable to the organization’s industry and specific circumstances.
A comprehensive gap analysis evaluates the organization’s current controls against SOC 2 requirements. The Readiness Partner identifies areas where controls are lacking, weak, or not adequately documented to meet SOC 2 standards.
4. Control Mapping
After identifying gaps, the Readiness Partner helps the organization map existing controls to SOC 2 criteria. They ensure that controls are aligned with the Trust Service Criteria (TSC) defined by the American Institute of CPAs (AICPA).
5. Documentation Review and Development
The Readiness Partner assists in creating or updating policies, procedures, and documentation to meet SOC 2 requirements. They help draft control narratives, risk assessments, and other necessary documentation to support SOC 2 compliance efforts.
6. Remediation Planning
Based on the gap analysis, the Readiness Partner develops a remediation plan outlining steps to address identified deficiencies. They prioritize remediation efforts based on risk and criticality to ensure efficient use of resources.
7. Implementation Support
A SOC 2 Compliance Readiness Partner provides ongoing support during the implementation of remediation measures. They assist in configuring systems, implementing security controls, and training staff to ensure compliance with SOC 2 requirements.
8. Internal Audit
Conducting an internal audit helps the organization simulate the actual SOC 2 audit process. The Readiness Partner assists in preparing for the SOC 2 Audit by conducting test procedures, reviewing documentation, and identifying areas for improvement.
9. Readiness Assessment Report
After completing the readiness assessment process, the Readiness Partner prepares a comprehensive report detailing findings, recommendations, and the organization’s readiness for the SOC 2 audit. This report serves as a roadmap for the organization’s SOC 2 compliance journey and helps demonstrate readiness to stakeholders and auditors.
10. Ongoing Support and Monitoring
Once the organization is prepared for the audit, the readiness partner will facilitate communication with SOC 2 audit firm, ensuring that all necessary information is provided. This includes assistance with the description criteria, furnishing evidence for controls, aiding in the collection of sample evidence, conducting walkthroughs, participating in interviews with the audit firm, and addressing any unresolved inquiries or issues raised by the audit firm.
A SOC 2 Readiness Partner plays a critical role in guiding organizations through the process of preparing for a SOC 2 audit. From initial scoping to ongoing support, they help organizations understand, implement, and maintain the necessary controls to achieve SOC 2 compliance. During your journey to SOC 2 Compliance, we recommend you consider undergoing Vulnerability Assessment and Pen Testing.Vulnerability Assessment and Pen Testing for SOC 2 Compliance
Your SOC 2 Readiness Partner may also offer vulnerability assessment and penetration testing services to help you prepare for your SOC 2 Audit and to ensure your controls are SOC 2 compliant. Here’s how vulnerability assessment and penetration testing can be integrated into the preparation for SOC 2 compliance:
1. Identify Security Weaknesses
Vulnerability assessment involves scanning systems, networks, and applications to identify security weaknesses such as misconfigurations, outdated software, and known vulnerabilities. Penetration testing takes this a step further by simulating real-world attacks to exploit identified vulnerabilities.
2. Mitigate Risks
By conducting vulnerability assessments and penetration tests, your Readiness Partner helps your organization identify and mitigate risks to data security, availability, processing integrity, confidentiality, and privacy—key areas of concern for SOC 2 compliance.
3. Align with SOC 2 Criteria
SOC 2 requires organizations to have effective controls in place to protect sensitive data and ensure the integrity and availability of systems. Vulnerability assessments and penetration tests help identify weaknesses in these controls, allowing the organization to address them before the audit.
4. Demonstrate Due Diligence
By proactively conducting vulnerability assessments and penetration tests, the organization demonstrates due diligence in safeguarding sensitive information and meeting SOC 2 requirements. This can enhance confidence among customers, partners, and auditors in the organization’s commitment to security and compliance.
5. Commit to Continuous Improvement
SOC 2 compliance is not a one-time effort but requires continuous monitoring and improvement of security controls. Vulnerability assessments and penetration tests provide valuable insights into evolving threats and vulnerabilities, enabling the organization to adapt its security measures accordingly.
While vulnerability assessment and penetration testing are not explicitly required for SOC 2 compliance, they are highly recommended practices to strengthen an organization’s security posture and readiness for the audit. By helping identify and address security vulnerabilities, these services contribute to building a robust control environment aligned with SOC 2 criteria. Therefore, a SOC 2 Readiness Partner may offer these services as part of their comprehensive approach to preparing organizations for SOC 2 compliance.
How databrackets can help you achieve SOC 2 Compliance
databrackets works in conjunction with certified CPA firms to prepare our customers to get ready for a SOC 2 Examination and obtain a SOC 2 report. Some of the services by our security experts are:
- Readiness Assessment & Recommendations
- Testing of Controls, Vulnerability Assessment and Security Risk Assessment
- Support to draft the Management Assertion for your SOC 2 Report
SOC 2 Examination by a certified CPA includes
- Determining the Trust Services Criteria
- Finalizing the SOC 2 Audit Period
- Scoping of the systems and applications
- Sampling & reviewing the evidence and policies & procedures
- Interviewing process owners
- Walkthrough of the systems/processes
- Testing the controls
- Documenting and reporting
The CPA that you chose to work with can access all your evidence in a streamlined manner on dbACE – our GRC Platform.
databrackets overview
Our team of security experts has supported organizations across a wide variety of industries to align their processes with security frameworks like HIPAA, 21 CFR Part 11, ISO 27001:2022, SOC 2, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Related Links:
SOC 2 Type 2 Audit for SaaS Companies
Can you submit a SOC 2 Report instead of a Vendor Security Questionnaire?
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.
Pen Testing versus Vulnerability Assessment
Feeling confused about security assessments? Are you unsure if a Vulnerability Assessment or Penetration Test is the right assessment for your organization? While both aim to test your defenses and security postures, they take very different approaches. This blog will untangle the mysteries of Vulnerability Assessments and Penetration Testing, helping you choose the ideal champion to evaluate your security posture.
Vulnerability Assessments (VAs) leverage automated tools to scan for known vulnerabilities in your software and systems. They provide a high-level view of potential issues based on documented weaknesses. This approach is cost-effective and efficient, making it ideal for regular checkups.
Penetration Testing (PT) simulates real-world attacker behavior, actively exploiting existing vulnerabilities to measure their impact. This in-depth assessment reveals how attackers might gain access and cause damage. However, Penetration Tests are more complex, requiring specialized skills and manual effort, leading to higher costs.
Organizations look for these security assessments usually for legal, contractual or regulatory purposes. Once you understand the business objective(s) for your assessment, you can select the right option or probably conduct both tests. However, in our experience as cybersecurity professionals for over 12 years, leveraging the strengths of both VA and PT at different times is ideal for your cybersecurity strategy.
Comparing Pen Testing and Vulnerability Assessment
Vulnerability Assessment and Penetration Testing (Pen Testing) are both critical components of a comprehensive cybersecurity strategy, but they serve different purposes and have distinct methodologies. Here’s a comparison of the two:

1. Purpose
Vulnerability Assessment: The primary goal of a vulnerability assessment is to identify, assess, and categorize vulnerabilities in an organization’s systems, networks, and applications. It focuses on finding weaknesses in the security posture without exploiting them. It aims to provide a snapshot of potential weaknesses that could be exploited by attackers.
Pen Testing: Pen Testing, on the other hand, involves actively simulating real-world cyberattacks to exploit vulnerabilities and determine the extent to which an attacker can gain unauthorized access or compromise systems. The primary purpose is to evaluate an organization’s security posture and measure its ability to withstand attacks if they are attacked.
2. Scope & Frequency of Testing
Vulnerability Assessment: It usually has a broader scope, focusing on identifying as many vulnerabilities as possible, including low-risk ones. It provides a comprehensive list of potential weaknesses.
Pen Testing: Pen testing has a narrower scope and typically focuses on a specific target or set of targets. It aims to demonstrate the impact of exploited vulnerabilities and assess the overall security posture.
3. Methodology
Vulnerability Assessment: It typically involves automated or manual scans of systems and networks to identify known vulnerabilities. The assessment can include vulnerability scanning tools, configuration reviews, and system analysis.
Pen Testing: Pen testing involves ethical hackers (penetration testers) actively trying to exploit vulnerabilities to understand their potential impact and determine if unauthorized access or data breaches are possible. This may include attempting to gain unauthorized access, privilege escalation, social engineering, network probing, data exfiltration, or other attack scenarios.
4. Reporting
Vulnerability Assessment: The output of a vulnerability assessment is a list of identified vulnerabilities, their severity ratings, and recommendations for remediation. It provides a roadmap for improving security but doesn’t include detailed exploitation scenarios.
Pen Testing: Pen testing reports include information on the vulnerabilities exploited, the impact of successful attacks, the techniques used, and recommendations for mitigating the risks. These reports are more in-depth and provide actionable insights based on actual attack simulations.
5. Regulatory Compliance
Vulnerability Assessment: Vulnerability assessments are often almost required to comply with various regulations and standards, such as PCI DSS, ISO 27001, SOC 2, HIPAA, NIST Cybersecurity Framework, NIST 800-171, CMMC 2.0, etc. This is considered as the minimum required security program for several organizations.
Pen Testing: Penetration testing is also required, at times, by regulations and security standards, and it is more focused in the areas where customer data is stored. Organizations in the finance industry, product/cloud companies and the healthcare sector are required to conduct the pen testing as the cost of breaches is too high if the services/products are not secured properly. Pen testing is required in any certification audit including SOC 2 & ISO 27001, apart from several compliance standards including PCI DSS, HIPAA, NIST Cybersecurity Framework, NIST 800-171, CMMC 2.0, etc.
6. Cost & Time
Vulnerability Assessment: Typically carried out through automated processes, this operation can take anywhere from a few hours to several hours to complete. The process, which includes identifying vulnerabilities and validating the results, is generally completed within a few days. The cost for this engagement usually begins at around USD 2,500.
Pen Testing: A considerable amount of work goes into collecting public information, conducting analysis, identifying vulnerabilities, and executing exploitation, including privilege escalation. Depending on the type of penetration testing – whether it’s network, application, or other asset types – the engagement typically spans 2 to 6 weeks. The cost for these services starts at approximately USD 15,000.
7. Benefit to your Cybersecurity Strategy
Vulnerability Assessment: The assessment tells you how your systems are configured and which policies & procedures you need to be changed to enhance security.
Pen Testing: It tells you how secure your systems are and which security controls are not implemented. After a Pen Test, you need to review your security tech & industry-specific best practices.
Do you need Pen Testing and Vulnerability Assessment or just one?
Vulnerability assessments are focused on identifying vulnerabilities, while penetration testing involves actively exploiting these vulnerabilities to assess their real-world impact. Both approaches are valuable in a comprehensive cybersecurity strategy, with vulnerability assessments providing continuous monitoring and early detection of weaknesses and penetration testing helping organizations understand their readiness to defend against sophisticated attacks. Both are valuable tools in a cybersecurity program, and organizations often use a combination of both to strengthen their overall security posture.
Compliance Driven Decisions: If legal, contractual, or regulatory requirements demand specific assessments, you need to follow the mandated standards or clauses.
Understanding Your Needs: If the decision isn’t dictated by external factors, consider your specific needs. Vulnerability Assessments are excellent for regular scanning and identifying broad areas for improvement. They are cost effective and help you categorize vulnerabilities. Pen Testing is invaluable for uncovering deeper vulnerabilities and understanding their real-world consequences.
How databrackets can help you with Vulnerability Assessment & Pen Testing
Our Vulnerability Assessment & Pen Testing capabilities have been accredited by the A2LA for ISO 17020 Conformity assessment for inspection bodies. Our cybersecurity experts have several years of experience helping organizations across industries to meet regulatory and customer requirements.
Our client engagement starts with your business objective in mind. Vulnerability Assessment & Pen Testing is requested for several reasons:
- To secure your environment
- To meet certain regulatory compliance or certification requirements
- To fulfill a request made by your customer
- A combination of the reasons mentioned above
Once we understand what you require, our exercise focuses primarily on scoping of the engagement and setting expectations. We use a variety of tools depending on the type of test and systems in which we need to identify vulnerabilities & conduct pen testing. Our process includes:
- Discovery
- Identifying and finalizing assets
- Identifying vulnerabilities
- Exploitation of the vulnerabilities (Pen Testing)
- Validation of the issues identified
- Remediation/Recommendations
- Re-testing
We conduct a wide variety of Penetration Tests for our clients to evaluate the level of security in the following:
- Internal Network
- External Network
- Web Application
- Mobile Apps
- Cloud Infrastructure
- IoT Devices
Apart from using the tools best in the industry, we also focus on remediation and retesting of the environment. We just don’t give hundreds of pages of reports without any help to eliminate the risks. We help our clients prioritize the risks based on the context, patch the systems and select security tech, policies and procedures that are considered best practices in their industry. We also set up continuous monitoring after our tests to track any changes to your environment & send you timely alerts.
As we continue to work with our clients, we sharpen our understanding of your specific environment and system. This helps us to design cadence for continuous protection and monitoring using the right tools to ensure continual improvement and proactive identification of issues for the future. You can contact us for a customized quote or schedule a consultation.
databrackets overview
Our team of security experts has supported organizations across a wide variety of industries to align their processes with security frameworks like ISO 27001:2022, SOC 2, HIPAA, 21 CFR Part 11, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC 2.0 etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Related Links:
Technologies To Detect And Prevent Ransomware Attacks
Sources of Ransomware Attacks on Healthcare Systems
What are the new controls added to ISO 27001 in 2022?
How to Select a Security Vendor
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.
Can you submit a SOC 2 Report instead of a Vendor Security Questionnaire?
Over the last decade, service organizations have been asked to prove their level of cyber hygiene before they are awarded a contract. The RFQs and contracts of small-medium sized businesses, particularly SaaS providers typically include an annual Vendor Security Questionnaire, which is extensive and time-consuming. To save time, optimize costs and streamline resources, many SaaS providers have been opting to undergo a SOC 2 Examination and prove their compliance with industry-preferred Trust Services Criteria and security controls. This single report serves as proof since it is given by an independent and authorized CPA after their controls have been tested and it serves as an alternative to the Vendor Security Questionnaire. This blog is intended to help you compare a SOC 2 Report and a Vendor Security Questionnaire and decide which option works for you.
Comparing a SOC 2 Report and a Vendor Security Questionnaire
A SOC 2 (Service Organization Control 2) report and a Vendor Security Questionnaire have some overlaps in terms of the controls they refer to. However, for some customers, they are not interchangeable. Here’s a brief overview of each:
SOC 2 Report
- A SOC 2 report is an assessment of an organization’s controls related to security, availability, processing integrity, confidentiality, and privacy.
- SOC 2 reports are conducted by independent third-party auditors and are designed to provide assurance to customers and partners about the security and privacy practices of a service provider.
- SOC 2 reports provide detailed information about the controls and processes in place, along with an auditor’s opinion on their effectiveness.
- These reports are often requested by customers to assess a vendor’s security and compliance posture.
Vendor Security Assessment Questionnaire
- These are typically questions answered by vendors to their customers or partners. The number of questions can vary between 30 to 300, contingent upon the vendor’s risk profile.
- Vendor security questionnaires are used to gather information about a vendor’s security practices, policies, and controls.
- They may be customized by the customer to align with their specific security requirements and concerns.
- These documents help customers assess a vendor’s security readiness, but they are based on self-reported information provided by the vendor.
In most cases, a SOC 2 report provides more comprehensive and independent assurance about a vendor’s security practices compared to a vendor security questionnaire. However, some organizations may still require vendors to complete their own security questionnaires or submit a SOC 2 Report and provide additional documentation to address specific security concerns or requirements.
How a SOC 2 Report streamlines the Vendor Assessment Process
B2B Contracts & RFQs rely on a SOC 2 Report because it can streamline their vendor assessment process in several ways. Here’s how a SOC 2 report can achieve this:

1. Comprehensive Assessment: A SOC 2 audit involves a thorough examination of an organization’s controls and processes related to security, availability, processing integrity, confidentiality, and privacy. The resulting report provides a comprehensive overview of the vendor’s security posture and compliance with industry standards.
2. Third-Party Verification: SOC 2 audits are conducted by authorized and independent third-party auditors, which enhances the credibility and reliability of the assessment. The fact that an impartial auditor has validated the vendor’s controls can reduce the need for the requesting organization to conduct its own extensive assessments.
3. Standardized Reporting: SOC 2 reports follow a standardized format with fixed criteria established by the American Institute of Certified Public Accountants (AICPA). This consistency makes it easier for the requesting organization to review and compare different vendors’ assessments, as they are presented in a comparable format.
4. Reduced Documentation Requests: Having a SOC 2 report implies that the vendor has already provided detailed documentation and evidence of its controls to the auditor. When requesting a SOC 2 report, the requesting organization can typically access this documentation, reducing the need for additional, redundant requests for the same information.
5. Saves Time and Cost: Conducting a full-scale security assessment of a vendor can be time-consuming and costly for both the vendor and the requesting organization. A SOC 2 report can expedite the assessment process, saving time and resources for both parties.
6. Trust and Confidence: A SOC 2 examination builds trust and confidence among customers and partners. It demonstrates the vendor’s commitment to security and compliance, which can lead to more successful and long-lasting business relationships.
7. Competitive Advantage: Having a SOC 2 report can give vendors a competitive advantage. Many customers prioritize vendors with SOC 2 certification because it simplifies the assessment process and reduces their own compliance and security risks.
While a SOC 2 report can streamline the vendor assessment process, it’s important to note that it may not completely eliminate the need for additional assessments or specific requirements tailored to the requesting organization’s needs. The level of scrutiny and specific requirements can still vary based on the nature of the vendor relationship and the sensitivity of the data or services involved. However, having a SOC 2 report as a foundation can significantly simplify and expedite the assessment process.
Our Client Experience
We have numerous clients who have shared that they have had to dedicate considerable amounts of time to complete a range of vendor assessment questionnaires for their customers in regulated sectors. Their experienced security analysts or consultants from our team have dedicated 10-30 hours for each questionnaire and submitted an average of 10-20 questionnaires annually. However, strategic acquisition of third-party reports such as SOC 2 has allowed our clients to completely bypass this time-consuming process, thereby freeing up their schedule to focus on business-critical tasks. By being able to prove their commitment to security and privacy of data using a standardized format, they have been able to retain their customers and meet the requirement for documentation & evidence.
How databrackets can help you with a Vendor Security Questionnaire
Our team of security experts conducts a thorough security assessment of your environment to understand your security controls, tools, techniques, processes & procedures. After this analysis, our customers can outsource the entire exercise of filling up Vendor Security Questionnaires to our team, as and when required. This has resulted in saving them an average of 400 hours of effort or 3-4 months, on an annual basis. Our team also engages with their customers on a need by need basis, to ensure they are fully supported in this endeavor.
A SOC 2 Examination takes a much shorter amount of time compared to repetitive filling of Vendor Security Questionnaires. Based on our recommendation, several clients have undergone a SOC 2 Readiness Assessment with our experts followed by their SOC 2 Audit by an authorized CPA. Our SOC 2 package has helped them to present their evidence and company information in a streamlined manner through dbACE, our GRC Platform. Through this optimized process, they have saved precious time & money.
While we recommend a SOC 2 Examination compared to an annual average of 400 hours of effort and time spent in repetitive filling of Vendor Security Questionnaires, we would also like to share that all SOC 2 Reports are not the same. A SOC 2 report provides detailed information about your security controls and processes, along with your auditor’s opinion of their effectiveness. The clarity and depth of your SOC 2 report depends on the expertise and reputation of the organization that has helped you prepare for your SOC 2 Audit and properly presented the evidence of how effective your controls are. When your evidence is presented with depth and accuracy, your auditor is able to gain a better understanding and evaluate your documentation. This clarity and depth impacts their opinion and subsequently your SOC 2 Report.
Additionally, the quality of testing varies between SOC 2 Auditors. Some auditors go in-depth and this thorough evaluation discovers issues that you may not be aware of otherwise. This helps you to identify the risk and implement measures to help your organization.
Hence, to have a SOC 2 Report that truly reflects your commitment to security and privacy, and which you can submit instead of a Vendor Security Questionnaire, you need to invest time and resources in the readiness process & work with a SOC 2 auditor who prioritizes a thorough evaluation.
How databrackets can help you with SOC 2 Readiness & Examination
databrackets works in conjunction with certified CPA firms to prepare our customers to get ready for a SOC 2 Examination and obtain a SOC 2 report. Some of the services by our security experts are:
- Readiness Assessment & Recommendations
- Testing of Controls, Vulnerability Assessment and Security Risk Assessment
- Support to draft the Management Assertion for your SOC 2 Report
SOC 2 Examination by a certified CPA includes
- Selecting the Trust Services Criteria
- Finalizing the SOC 2 Audit Period
- Scoping of the systems and applications
- Sampling & reviewing the evidence and policies & procedures
- Interviewing process owners
- Analyzing the results
- Documenting & reporting
The CPA that you chose to work with can access all your evidence in a streamlined manner on dbACE – our GRC Platform.
databrackets overview
Our team of security experts has supported organizations across a wide variety of industries to align their processes with security frameworks like HIPAA, 21 CFR Part 11, ISO 27001:2022, SOC 2, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Related Links:
Technologies To Detect And Prevent Ransomware Attacks
Sources of Ransomware Attacks on Healthcare Systems
What are the new controls added to ISO 27001 in 2022?
How to Select a Security Vendor
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.
SOC 2 versus ISO 27001
Organizations frequently face a tough choice between SOC 2 and ISO 27001 certifications as a means to showcase their security maturity. Comparing the two security standards can be tough and the decision-making process can be complex, as each certification brings its own set of advantages and challenges. As certified security experts who regularly work with both frameworks, we will discuss details about each security standard to help you make an informed choice that aligns with your business objectives, industry standards, and the risk tolerance demanded by your customers.
What is SOC 2?
SOC 2 (System and Organization Controls 2) is a security standard for service organizations, developed by the American Institute of CPAs (AICPA). The SOC 2 framework is applicable to all technology service providers or SaaS Product companies that work with customer data. It specifies aspects of security that they need to follow while managing customer data.
SOC 2 Certification is based on 5 Trust Services Criteria: security, availability, processing integrity, confidentiality and privacy of customer data. The SOC 2 framework does not provide a specific list of controls and tools. It merely cites the criteria required to maintain a high level of information security. It is up to each organization to establish the practices and processes relevant to their own objectives and operations. A SOC 2 report provides detailed information about the controls and processes in place, along with an auditor’s opinion on their effectiveness.
What is ISO 27001?
ISO 27001 is a globally respected information security standard. It was designed, regulated and continues to be updated by the International Organization for Standardization. It is officially referred to as ‘ISO/IEC 27001’ and is part of the ISO/IEC 27000 family of standards.
Even though ISO 27001 isn’t a legal mandate, organizations around the world prefer to work with B2B partners and vendors who are ISO 27001 certified. Its popularity is attributed to the fact that ISO 27001 controls evaluate the strength of an organization’s Information Security Management System (ISMS) and the 2022 version is designed to prevent advanced persistent threats.
Comparing SOC 2 and ISO 27001

SOC 2 (System and Organization Controls 2) and ISO 27001 are two different frameworks B2B companies use for assessing the ISMS of potential vendors and partners. While they share some similarities, they also have distinct differences. Here’s a comparison of SOC 2 and ISO 27001 in terms of their similarities and differences.
Similarities between SOC 2 and ISO 27001
1. Information Security Focus:
Both SOC 2 and ISO 27001 are focused on information security management. They aim to ensure the confidentiality, integrity, and availability of sensitive data and systems.
2. Risk Management: Both frameworks emphasize the importance of identifying, assessing, and mitigating information security risks. They require organizations to have risk management processes in place.
3. Third-Party Audits:
Both SOC 2 and ISO 27001 certifications involve third-party audits conducted by independent auditors or certification bodies to verify compliance with their respective standards.
4. Control Objectives: Both frameworks provide a set of control objectives or requirements that organizations must meet to achieve certification. These control objectives address various aspects of information security.
5. Continuous Improvement:
Both SOC 2 and ISO 27001 promote a culture of continuous improvement by requiring organizations to regularly assess and update their security measures.
Differences between SOC 2 and ISO 27001
1. Scope
SOC 2: Primarily focuses on service organizations, particularly those that provide services to other businesses like SaaS providers. SOC 2 reports are often used by customers to evaluate the security of service providers.
ISO 27001: Can be applied to any type of organization, including service providers and manufacturing companies. It is not limited to service organizations.
2. Origin of the Framework
SOC 2: Developed by the American Institute of CPAs (AICPA) and is widely recognized in the United States.
ISO 27001: Developed by the International Organization for Standardization (ISO) and is an international standard recognized globally.
3. Certification versus Attestation
SOC 2: SOC 2 is not technically a certification; it is officially called a SOC 2 Examination. A SOC 2 Audit results in an attestation report, which provides information about the controls in place but does not result in certification. Organizations receive a SOC 2 Type 1 or Type 2 report.
ISO 27001: Results in certification, indicating that an organization’s Information Security Management System (ISMS) complies with the ISO 27001 standard. Organizations receive ISO 27001 certification.
4. Control Framework
SOC 2: It does not provide a specific control framework but relies on predefined trust service criteria (e.g., security, availability, processing integrity, confidentiality, and privacy) that organizations must address.
ISO 27001: Provides a comprehensive set of controls and control objectives which organizations have to implement.
5. Reporting Structure
SOC 2: Typically results in a Type 1 or Type 2 report that outlines the controls in place and their effectiveness during a specific period (Type 1 for a point in time, Type 2 for a period of time).
ISO 27001: Results in a certificate issued by a certification body indicating that an organization’s ISMS complies with ISO 27001. It does not provide specific details on individual control effectiveness.
6. Cost
SOC 2 : Readiness & Implementation Cost: Starting at $15,000 +
Certification Cost: Starting at $10,000 +
ISO 27001: Readiness & Implementation Cost: Starting at $20,000 +
Certification Cost: Starting at $10,000 +
7. Time
SOC 2: Readiness & Implementation: 3-4 months for SMBs, maybe longer for large enterprises
Certification: 3-6 months depending on the period of observation and 4-8 weeks subsequently for testing and reporting
ISO 27001: Readiness & Implementation: 3-4 months for SMBs, maybe longer for large enterprises
Certification: 3-6 weeks
In summary, both SOC 2 and ISO 27001 are valuable frameworks for managing information security, but they differ in terms of scope, origin, certification vs. attestation, control framework, and reporting structure. Organizations should choose the framework that aligns best with their specific needs, industry, and geographic considerations. Additionally, some organizations may choose to pursue both certifications to meet the needs of different stakeholders.
How databrackets can help you with SOC 2
databrackets works in conjunction with certified CPA firms to prepare our customers to get ready for a SOC 2 Examination and obtain a SOC 2 report. Some of the services by our security experts are:
- Readiness Assessment & Recommendations
- Testing of Controls, Vulnerability Assessment and Security Risk Assessment
- Support to draft the Management Assertion for your SOC 2 Report
SOC 2 Examination by a certified CPA includes
- Selecting the Trust Services Criteria
- Finalizing the SOC 2 Audit Period
- Scoping of the systems and applications
- Sampling & reviewing the evidence and policies & procedures
- Interviewing process owners
- Analyzing the results
- Documenting and reporting
The CPA that you chose to work with can access all your evidence in a streamlined manner on dbACE – our GRC Platform.
How databrackets can help you with ISO 27001
databrackets has a team of certified ISO Lead Auditors. We help organizations achieve their ISO goals by supporting them with:
- ISO 27001 Certification
- Do-It-Yourself ISO 27001 assessment toolkit
In our DIY (Do It Yourself) assessment toolkit all the clauses and controls stipulated by ISO 27001 standards are uploaded on our GRC Platform – dbACE. Customers need to upload their data along with evidence and mark the clause/controls’ ‘implementation’ status for Stage 1 and Stage 2 Assessments.
Our ISO Lead auditors conduct an impartial assessment based on the evidence provided and record their findings on dbACE. This helps them communicate the results and seek corrective measures wherever necessary – all in one location. The dbACE interface makes the turnaround quicker and saves time, effort and, thereby, costs. The documentation for the audit from start-to-finish takes place on this platform. This includes the final report that reflects the status of the customer’s adherence to ISO 27001 standards and guidelines.
databrackets overview
Our team of security experts has supported organizations across a wide variety of industries to align their processes with security frameworks like HIPAA, 21 CFR Part 11, ISO 27001:2022, SOC 2, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Related Links:
Technologies To Detect And Prevent Ransomware Attacks
Sources of Ransomware Attacks on Healthcare Systems
What are the new controls added to ISO 27001 in 2022?
How to Select a Security Vendor
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.
SOC 2 Type 2 Audit for SaaS Companies
 Getting a SOC 2 Type II Report can be a game-changer for a SaaS Company. It can transform how you respond to RFQs and how you assure potential leads that your systems are secure. Most SaaS companies view the cost of a SOC 2 Certification / Examination as an investment in their future revenue. They plan meticulously to succeed in their SOC 2 audit and stay certified.
Getting a SOC 2 Type II Report can be a game-changer for a SaaS Company. It can transform how you respond to RFQs and how you assure potential leads that your systems are secure. Most SaaS companies view the cost of a SOC 2 Certification / Examination as an investment in their future revenue. They plan meticulously to succeed in their SOC 2 audit and stay certified.
A SOC 2 audit is conducted by an authorized CPA firm or SOC 2 auditor that you select. During your SOC 2 audit, they assess the design and performance of your internal controls at a point in time or over a defined number of months. During the audit period they take a sample to test the end-to-end performance of these controls and report their findings. The results of the audit and the effectiveness of the controls are outlined in the SOC 2 audit report. This helps clients and business partners understand which Trust Services Criteria your systems adhere to. By staying SOC 2 certified, you can continue to assure stakeholders of the value of working with your company.
Preparing for your SOC 2 audit
SaaS companies begin preparing for their SOC 2 audit by implementing the internal controls that are important to their clients. They gather evidence and documentation and look for a SOC 2 auditor who understands their industry and customer requirements. One way to verify the authenticity of the CPA Firm / SOC 2 auditor is by checking the AICPA’s Public File Search.
As you prepare for your SOC 2 Type II audit or during the audit itself, you may face challenges with their SOC 2 auditor that can be avoided. One such confusion is with regards to the Trust Services Criteria.
Are you expected to follow all the Trust Services Criteria?
AICPA has outlined 5 Trust Services Criteria as part of the SOC 2 framework – Security, Availability, Confidentiality, Privacy and Processing Integrity. However, any organization that wants to get SOC 2 certified, is allowed to select the criteria they want and implement the respective internal controls. During the SOC 2 audit, your auditor is only expected to review the criteria that you have selected. They cannot ask you to comply with more criteria than the one(s) you have selected.
Typically, a SaaS company may choose to implement the follow Trust Services criteria:
- Security: This focuses on protecting information and all systems from unauthorized access.
- Availability: This focuses on the resiliency of the infrastructure, information and software.
- Confidentiality: This refers to the company’ ability to restrict access and ensure that data is disclosed only to authorized personnel or organizations.
They may also choose to implement certain controls under the remaining 2 criteria if their clients require it.
- Privacy: This addresses the organization’ ability to protect Personally Identifiable Information (PII) and ensure that it cannot be used to identify any individual. Privacy as a TSC, is primarily essential for Direct to Consumer engagement.
- Processing integrity: This verifies if the systems achieve their purpose – the delivery of complete and accurate data, within the correct timeframe and level of access.
What happens in a SOC 2 audit of a SaaS company?
A SOC 2 audit only begins when all the controls are in place and all aspects of information security are performing as designed. To check their level of preparedness, SaaS companies may opt for a SOC 2 Readiness Assessment. This can be a failsafe option since all the controls are tested and evidence is systematically organized and checked by a consultant. You get an opportunity to plug the gaps, complete your evidence collection and begin writing the ‘Management’ Assertion’. This section is submitted by the company to the SOC 2 auditor and included in your SOC 2 Report. During this time, you can also vet potential SOC 2 auditors and finalize the scope of your engagement.
Once you select your auditor, discuss your engagement and finalize your scope, the audit period begins on the date decided by the SOC 2 auditor. The first SOC 2 examination period is usually 3-6 months. The company cannot modify any process during the audit period. The start date of a SOC 2 audit is in the future, and it is shared with the CPA firm. Performance evaluated outside of the SOC 2 audit period cannot influence or be part of the SOC 2 report.
The audit period begins with the auditors collecting evidence for all the controls and for some controls with populations, selecting a random sample from a population of data, based on AICPA Guidelines and scientific sampling principles. During the SOC 2 audit, auditors observe security controls in action as they relate to the random sample. The company is expected to showcase evidence and confirm that all the controls have been designed and implemented per intent. If controls are implemented correctly and the company is SOC 2 ready, customer data is protected, and no violation is observed. The absence of activity during the audit is a sign of success since it implies that all aspects of data protection are in place. The testing of the controls starts immediately after the audit period ends. The sample’s test results are included in the SOC 2 report.
How is a SOC 2 Type II audit different for a SaaS Company?
Physical security controls may not be applicable for a SOC 2 certification / examination of a SaaS company because the tech infrastructure is hosted with a Cloud Service Provider. Since SaaS companies outsource it to a 3rd party, they are responsible for it. As a result, an on-site audit may also be optional for a SaaS company.
Your SOC 2 audit might also include reviewing the SOC 2 reports of your vendors and partners. Your SOC 2 auditor might verify and validate CUECs of your vendors as well.
How regularly are you required to perform a SOC 2 audit?
A SOC 2 report is valid for 12 months. SOC 2 audits are conducted every 12 -18 months to help you stay certified. You reserve the right to change your SOC 2 auditor after every engagement and modify the Trust Services Criteria during each SOC 2 audit. In our experience as SOC 2 Readiness Assessment consultants, we have observed that SaaS companies usually add additional controls and criteria while continuing to implement previous controls. They also tend to improve in the way they structure and gather evidence to reduce the amount of time and effort during each SOC 2 audit.
What is the cost of a SOC 2 Certification / Examination?
The cost of a SOC 2 certification can be divided into 2 sections:
Cost of SOC 2 Readiness Assessment: Consultants who specialize in preparing firms for SOC 2 can help you design /implement new controls, draft and implement policies and procedures, provide customized staff training, review your evidence documents and help you draft the ‘Management’ Assertion’. They can also help you streamline the Complementary User Entity Controls (CUECs) that your customers will need to have in place to use your services properly. Some examples of CUECs are password complexities, time out parameters and MFA. These have to be set up by the customer, not necessarily the SaaS company. The client and SaaS company have shared a responsibility to ensure security. The SaaS company is responsible for defining CUECs clearly and your customer is responsible for implementing them.
Working with a SOC 2 readiness partner who has previous experience in your industry can also help you streamline the Trust Services Criteria that will be important to your clients. This will help you plug any gaps and not only help you prepare for your SOC 2 audit but also for the RFQs where you will include your SOC 2 Report. A typical SOC 2 engagement for readiness could cost anywhere from USD 10,000 – 50,000.
Cost of SOC 2 Certification / Examination: A SOC 2 examination by a CPA firm could cost anywhere from USD 15,000 – 30,000 depending on the trust services criteria you select. However, the price should not be the predominant factor that influences your decision. A SOC 2 auditor who understands your industry will be able to clearly mention the Complementary User Entity Controls (CUECs) in the SOC 2 Report. These controls are intended for your customer – the actual consumer of the SOC 2 report. They inform your customer about the controls they need to implement in their systems to properly use your services. You also need to read the fine print that is part of the engagement contract and ensure that you are not legally obligated to work with the same SOC 2 auditor or authorized CPA firm for the next few years.
The ideal SOC 2 auditor is the one who respects your selection of the Trust Services Criteria, understands what your customer’s need to know and ensures that your scope is clearly mapped before the engagement begins. You can review some recommendations to help you avoid challenges you may face with a SOC 2 auditor.
How databrackets can support your SOC 2 Journey ?
Experts at databrackets have extensive experience in supporting organizations that align their processes with AICPA’s Trust Services Criteria and prepare for a SOC 2 Audit. If you would like to connect with an expert to better understand SOC 2 and plan your SOC 2 journey, do not hesitate to schedule a consultation.
Related Links:
Challenges you may face with a SOC 2 auditor
 A SOC 2 certification / examination is pursued by service organizations who want to prove to potential customers that they can manage their data effectively. Typically a SaaS provider, Managed Service Provider (MSP), Network service provider and other service providers select an authorized CPA firm and an authorized SOC 2 auditor in it, to audit their system. Usually, the process may be smooth if they go through a readiness prep assessment and then select a SOC 2 auditor who is familiar with their industry and customer requirements. However, sometimes, you may find yourself in a difficult situation during your SOC 2 audit and you may want to consider changing your SOC 2 auditor.
A SOC 2 certification / examination is pursued by service organizations who want to prove to potential customers that they can manage their data effectively. Typically a SaaS provider, Managed Service Provider (MSP), Network service provider and other service providers select an authorized CPA firm and an authorized SOC 2 auditor in it, to audit their system. Usually, the process may be smooth if they go through a readiness prep assessment and then select a SOC 2 auditor who is familiar with their industry and customer requirements. However, sometimes, you may find yourself in a difficult situation during your SOC 2 audit and you may want to consider changing your SOC 2 auditor.
A SOC 2 examination can be time consuming, and you can exceed your budget if it is not systematically planned. Sometimes, the challenges may arise from within the company and can lead to a blame game with the auditor. We highly recommend undergoing a SOC 2 readiness assessment, getting organized and vetting your SOC 2 auditor, to avoid such an occurrence.
Challenges you may face with a SOC 2 auditor:
1) Lack of engagement overview & scope analysis
Your SOC 2 audit can be a relatively seamless experience when your evidence matches the SOC 2 controls and the Trust Services Criteria you want audited. After you agree on the scope of the audit and your customer requirements, it is up to the SOC 2 auditor to discuss all the steps involved and the evidence that you will be required to submit. If the scoping is not clearly defined at the start, the auditor can go out of scope. This can be particularly confusing for companies who are new to SOC 2 and who need a proper orientation to the process. The process has to be matured and you need to gauge the process maturity of the CPA firm before finalizing your contract to work with them.
SOC 2 audits need to be conducted annually. As a result some CPA Firms also mandate the continuity of work for 3-5 years in their contracts. The SOC 2 framework and AICPA does not mandate continuing with the same SOC 2 auditor after you complete your engagement. This is yet another area of conflict that needs to be discussed at the outset, so you are well-informed before you sign your contract to work with the authorized CPA Firm.
There can be several pitfalls and unnecessary obstacles in your SOC 2 journey if your initial discussions are not thorough and if your auditor does not guide you properly. This is the root cause for most of the challenges you may face. We recommend that you review the rest of the challenges and draft a set of questions to vet the SOC 2 auditor before you finalize who will conduct your SOC 2 audit.
2) Time
The time spent with a SOC 2 auditor can seem excessive and hamper your ability to manage daily business operations. This can be challenging since the auditor might request a lot of information for the SOC 2 report, which you may not know is required. For example: documented proof of the management’s engagement on security issues. Proving this can involve going through several meeting documents. Audit time is not defined for a SOC 2 examination as it is for an ISO certification and this might result in unpleasant surprises for your team.
Additionally, some auditors share a spreadsheet and ask you to email evidence documents. This system can be chaotic since you need to see the correlation between the controls and the evidence / documents.
One solution we recommend is engaging the services of a SOC 2 readiness assessment partner, like databrackets, to help you get organized before your engagement with an auditor. At the outset we invite you to share your evidence on our platform as per the controls and corresponding Trust Services Criteria you have selected. This helps you to work systematically and share the evidence further with your chosen auditor. A SOC 2 readiness assessment not only helps you to save time and effort but also ensures that you have someone to check your evidence / documents and share feedback before the actual SOC 2 audit.
3) Lack of Industry Knowledge
The purpose of a SOC 2 examination / SOC 2 certification is to prove to your customers that your systems will effectively manage their data. However, at times, your SOC 2 auditor may not be familiar with your industry, day-to-day operations, SLAs and customer expectations. As a result, they may not be able to produce the kind of report that meets your customer’s expectations. This defeats the purpose of getting certified and could lead to frustration since the actual consumer of the SOC 2 report is your customer / stakeholder. If they do not get the impression that you are the right vendor for them after reading the report, the whole exercise will seem counterproductive.
Lack of industry knowledge also impacts a critical part of the report – Complementary User Entity Controls (CUECs). We have discussed this at length in the next section.
4) Unclear Complementary User Entity Controls (CUECs) in the SOC 2 Report
A customized SOC 2 report clearly outlines the Complementary User Entity Controls or CUECs in the description of the customer’s system. These controls are intended for your customer – the actual consumer of the SOC 2 report. They inform your customer about the controls they need to implement in their systems to properly use your services.
A SOC 2 auditor who is familiar with your industry can explain these CUECs in the SOC 2 Report. This is critical since the level of security, availability, privacy, confidentiality and processing integrity of your system can only be maintained when it is properly configured in the systems used by your customer. If your SOC 2 auditor does not understand your service requirements and which CUECs are critical in your industry, you may receive a SOC 2 report that does satisfy your customers and meet your objectives.
5) Selective examination of Trust Services Criteria
The SOC 2 framework permits clients to focus on the Trust Services Criteria which they want audited and exclude the rest. This flexibility exists since the SOC 2 Report outlines at the start which criteria and controls are being examined and then showcases if they function at optimal levels or not. SOC 2 allows you to select the Trust Services Criteria which you want to showcase. By using this method, the client’s customers are informed and empowered to take a decision to work with the client or not. While this is the ideal situation, if your SOC 2 auditor is unwilling to accept your decision, even when the rules permit, you may face a difficult situation. Your SOC 2 auditor may insist on an audit of all the Trust Services Criteria and not respect the flexibility accorded by the SOC 2 framework,
6) Hidden Costs and Additional Expenses
SOC 2 audits are done by authorized CPA firms who may have sister concerns or partners who offer other services which may be helpful to your company. Sometimes, your SOC 2 auditor may try to up-sell / cross sell these services aggressively, under the guise of good advice. This can lead to a conflict and unplanned expenses.
Before your SOC 2 audit, you may also be advised to undergo penetration testing to check the security of your systems. This can be yet another hidden cost, which you can predict with a SOC 2 readiness assessment.
Each of these challenges are severe and it is important to avoid the possibility of going through any of them. Through this blog, we hope that you have been empowered to foresee potential pitfalls and vet the SOC 2 auditor in the introductory meeting, ask for a sample report for your industry, review the terms of the contract you will sign and follow-up on their references before you begin your engagement.
How databrackets can support your SOC 2 Journey
Experts at databrackets have extensive experience in supporting organizations align their processes with AICPA’s Trust Services Criteria and prepare for a SOC 2 Audit. If you would like to connect with an expert to better understand SOC 2 and plan your SOC 2 journey, do not hesitate to schedule a consultation.
Related Links:
7 Benefits of SOC 2
A SOC 2 Report helps organizations to prove their commitment to customer data security and meet the eligibility criteria of a potential client’ RFQ. More and more clients have been asking for proof of SOC 2 Compliance while evaluating if they want to work with a vendor. This is particularly relevant for technology service providers, SaaS providers, and any organization that stores and processes customer data.
Technically, SOC 2® is not a certification. It is a report on the organization’s system and management’s internal controls relating to the Trust Services Criteria. It includes the auditor’s opinion of control efficacies on protecting data, also known as a ‘SOC 2® Attestation’.

As security partners who have worked with countless SaaS providers to prep their organization for a SOC 2 Audit, we at databrackets have observed the following 7 key benefits of SOC 2:
1. Meet regulatory requirements: Once you are SOC 2 Compliant, you are aligned with AICPA’s regulatory controls. A SOC 2 certificate is proof of that.
2. Supervise your organization: SOC 2 compliance mandates supervising all aspects of information security across all processes internally along with setting the benchmarks for vendors who manage customer data. In order to accomplish this, a robust process is designed, and its effectiveness is verified once an organization is SOC 2 Certified.
3. Get a leading security certification issued by an independent 3rd party: A SOC 2 Examination is conducted by an authorized and certified CPA. This gives credibility to the process and ensures it is conducted in an objective way. As a result, it is considered to be a highly valued certification.
4. Sign new deals: You can sign more deals and increase the number of clients once you prove your ability to effectively manage customer data with a SOC 2 Certificate.
5. Assure existing customers: You can prove to your existing customers that your company not only manages their customer data with the highest level of information security, but that this has also been verified by an authorized CPA firm after a rigorous SOC 2 audit.
6. Strengthen Vendor Management: You can set the benchmarks for vendors and ensure compliance with the highest level of information security.
7. Monitor internal corporate governance and risk management processes: You can design and monitor risk management processes and internal corporate governance in accordance with the SOC 2 framework.
Experts at databrackets have extensive experience in supporting organizations align their processes with AICPA’s Trust Services Criteria and prepare for a SOC 2 Audit. If you would like to connect with an expert to better understand SOC 2 and plan your SOC 2 journey, do not hesitate to schedule a consultation.
Related Links:
What is SOC 2?
SOC 2 is a compliance standard for service organizations, developed by the American Institute of CPAs (AICPA). It specifies how organizations should manage customer data. The SOC 2 framework is applicable to all technology service providers or SaaS Product companies that store customer data. They are required to ensure that security controls and practices are designed and implemented effectively to safeguard the privacy and security of customer data. There are several benefits of being SOC 2 Compliance.
This security framework does not provide a specific list of controls and tools. It merely cites the criteria required to maintain a high level of information security. It is up to each organization to establish the practices and processes relevant to their own objectives and operations. SOC 2 Certification is based on 5 Trust Services Criteria: security, availability, processing integrity, confidentiality and privacy of customer data.
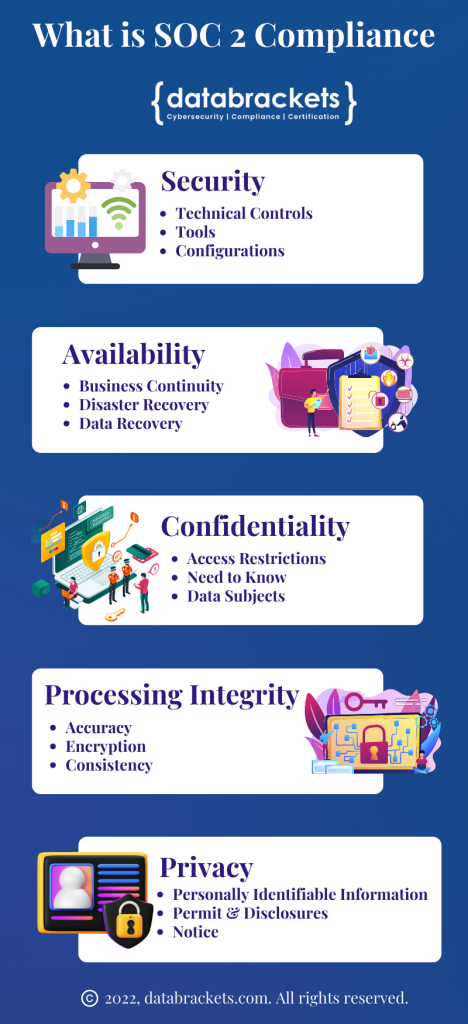
Basics of SOC 2 Compliance
There are several components of becoming SOC 2 Compliant, a SOC 2 gap assessment, implementation of identified gaps, a SOC 2 audit and SOC 2 report that needs to be understood before you begin this journey. Getting SOC 2 Compliant fast is a marketing gimmick.
SOC 2 Compliance versus SOC 2 Certification
Being SOC 2 Compliant is essentially having a valid SOC 2 report by an independent third-party CPA firm. Technically, SOC 2 is not a certification – it is the auditor’s opinion of control efficacies on protecting data, also known as a ‘SOC 2 Attestation’. A SOC 2 attestation is based on the Trust Services Criteria and is provided by a registered CPA firm authorized by the AICPA. Usually, a SOC 2 report is valid for a year and the organization is required to engage the same or a different CPA firm to conduct the next SOC 2 audit.
*We would like to share that the official term is ‘SOC 2 examination’. In the industry the term ‘SOC 2 compliance’ is used interchangeably. Similarly, the official term is ‘reporting’, while the commonly used term is ‘certification’ interchangeably to help put the content into the appropriate context.
Experts at databrackets have extensive experience in supporting organizations align their processes with AICPA’s Trust Services Criteria and prepare for a SOC 2 Audit. Our unique approach to SOC 2 readiness not only brings in experts from the industry but also leverages our assessment platform to identify controls, collect the required evidence and collaborate with auditors. If you would like to connect with an expert to better understand SOC 2 and plan your SOC 2 journey, do not hesitate to schedule a consultation.
Related Links:
SOC 2 Guide : Get answers to all your SOC 2 questions
Top 5 Things You Should know about SOC 2 Compliance
Introduction
SOC 2 provides valuable insights into your organization’s security posture at any given time. It is an auditing procedure and a crucial framework that applies to all technology, product, and cloud computing service providers that store customer data. It ensures that companies securely manage data to protect the interests of your organization and the privacy of its clients.
SOC 2 Compliance report not only provides valuable insights into your organization’s security posture but also provides you with a competitive edge.
Passing the SOC 2 audit process provides you the much-required peace of mind that your systems and networks are secure. But a SOC 2 readiness test helps you locate the gaps in your procedures, internal controls, and documentation even before the auditor finds them.
Check your readiness score here. Following are the top 5 things based on our years of experience in helping companies with SOC 2 readiness:
Is SOC 2 mandatory?
SOC 2 is neither a compliance law nor a regulation. But It is a complex set of requirements that must be carefully addressed. Compliance is the key driver for Customer assurance.
A SOC 2 report is designed to protect customer data from unauthorized access and compliance is a crucial measure to avoid costly security breaches.
Tenets of SOC 2 Compliance
SOC 2 does not prescribe standards but simply audits and confirms that the processes are actually being followed in practice. In other words, it covers five basic trust service “principles”: security, availability, processing integrity, confidentiality, and privacy.
Things to monitor for SOC 2 Compliance- Alerts, Triggers, Visibility
Alerts
SOC 2 requires you to set up alerts for:
- Exposure or modification of data, controls, configurations
- File transfer activities
- Privileged filesystem, account, or login access
Triggers
SOC 2 prescribes alerts whenever there is unauthorized access to customer data
Visibility
You must have visibility at the host level. User activity, processes, network connections, and threat-prone areas require visibility. You should seek compliance mechanisms to conduct behavior-based monitoring to detect suspicious events.
Can I fast-track SOC 2 Compliance?
The answer to this question really depends on many factors – the size of your organization, your readiness score, the resources available, and the type of audit –SOC 2 Type 1 or 2 you need. Depending on these elements, Type 1 may take up to a month, while Type 2 may take 3 to 12 months. So, fast-tracking SOC 2 compliance is possible only when all resources – controls, policies and your technical stack are readily available and securely configured. Most companies start the SOC 2 path only after a customer requests an audit report. But, getting to a realistic timeline requires an expert recommendation and a dedicated team. We work with clients to pre-assess, identify critical tasks, and offer expert advice on project management to get you the realistic timeline.
What pitfalls/ mistakes should I prevent?
- Not doing a pre-assessment: Not performing a readiness test, can lead to unexpected gaps and failures during the audit. It can also lead to a longer time to completion of the audit
- Limiting to core applications: Some companies believe in testing security controls only on the core applications. What they don’t know is that some controls are non-technical in nature that can trip their security posture.
- Not allowing ample time for the audit completion: Companies that need Type II reports need to be assessed for about 100 security controls which take time and in order to be compliant, they must put in ample time and effort.
How can we help you with SOC 2 Compliance?
Achieve your SOC 2 compliance attestation with our team of security experts of who can streamline the audit process, prep you for the journey, and help you succeed with SOC 2 compliance.
Read our SOC 2 Compliance Guide and engage with our team of security experts who can prep you for your SOC 2 journey, streamline the audit process and help you succeed at SOC 2.