Verizon’s Data Breach Investigations Report puts the cost of 95% of security incidents at $1 million – $2.25 million dollars. The report is based on the analysis of 16,312 security incidents and 5,199 breaches. They found 74% of all breaches to be a result of human error due to social engineering. In terms of cyberattack methods, Ransomware constitutes 24% of all breaches and its popularity has been growing rapidly over the last few years. The report states that a variety of different techniques were used to gain entry to an organization, such as exploiting vulnerabilities (5%), phishing (12%), and using stolen credentials (49%). Following industry best practices and protocols is recommended by the analysts to safeguard organizations against breaches.
With over a decade of experience in supporting organizations to meet compliance and cybersecurity requirements, our certified experts have identified various technologies to prevent ransomware attacks and enhance your cybersecurity posture. These are in keeping with industry best practices. We have also identified vendors with a successful track record and shared the list in the table below. The price point of implementing these technologies varies depending on your set-up. One way to ensure you are making the right choices for your organization is to undergo a Security Risk Analysis to detect areas of improvement and work with a CISO or vCISO to design a comprehensive cybersecurity strategy.
It’s important to note that while technology plays a significant role in preventing ransomware attacks, a comprehensive cybersecurity strategy should also include regular software updates, strong access controls, robust security policies, incident response plans, penetration testing and ongoing monitoring and assessment of security measures.
Security Tech To Prevent Ransomware Attacks And Enhance Your Cybersecurity Posture

1. Endpoint Protection Platforms (EPP):
Most ransomware attacks stem from end devices such as laptops, desktops, and mobile devices linked to the organization’s network. EPP solutions are designed to secure individual endpoints such as laptops, desktops, and mobile devices. They provide antivirus, anti-malware, host-based intrusion detection/prevention systems and behavioral analysis capabilities using artificial intelligence to detect and block ransomware threats. EPPs often include features like real-time scanning, heuristic analysis, and threat detection and prevention. They scan files and processes in real-time, identify known threats, and block or quarantine infected files.
2. Next-Generation Firewalls (NGFW):
NGFWs combine traditional firewall capabilities with advanced security features. They use deep packet data inspection, application awareness, and intrusion prevention systems (IPS) to identify and block malicious traffic that may carry ransomware payloads. They often integrate threat intelligence feeds to stay updated on the latest ransomware signatures and indicators of compromise. NGFWs can also enforce policies for network segmentation and user access control.
3. Intrusion Detection/Prevention Systems (IDS/IPS):
IDS and IPS solutions monitor network traffic for potential security breaches and malicious activities. They can detect and block ransomware-related network communications, such as command-and-control (C2) traffic or attempts to exploit vulnerabilities. IDS provides real-time alerts for suspicious network events, while IPS actively blocks or mitigates potential threats. They can help detect and prevent ransomware attacks from spreading across the network.
4. Threat Intelligence Platforms:
Threat intelligence platforms collect and analyze data from various sources to identify emerging threats, including new variants of ransomware. By leveraging threat intelligence, organizations can proactively update their security measures and stay ahead of evolving ransomware threats.
5. Security Information and Event Management (SIEM):
SIEM tools collect and analyze security event logs from various sources, such as firewalls, network devices, endpoints, and servers. By correlating and analyzing this data, SIEM solutions can detect and alert organizations about potential ransomware attacks. They can identify patterns indicative of ransomware attacks and trigger real-time alerts for immediate action. They provide centralized visibility into security events, facilitate incident response, and enable proactive threat hunting.
6. Application Whitelisting:
Application whitelisting involves allowing only authorized applications to run on systems, blocking any unauthorized or malicious software, including ransomware. This approach prevents the execution of unknown or suspicious programs and restricts the ability of ransomware to infiltrate the network.
7. Network Segmentation:
Network segmentation involves dividing a network into smaller multiple isolated subnetworks, typically based on user roles. By segregating critical assets and limiting lateral movement, implementing firewalls and access controls to restrict unauthorized access, even if one segment gets compromised by ransomware, it won’t easily spread to other parts of the network. This strategy helps contain and mitigate the impact of ransomware attacks.
8. Patch Management Systems:
Regularly updating software and operating systems is crucial for preventing ransomware attacks. Patch management systems automate the process of identifying, deploying and verifying patches security patches. This ensures that systems are up to date and protected against known vulnerabilities. Automating this process reduces the chances of exploitation by ransomware or other malware that target known weaknesses.
9. Vulnerability Management Systems:
Regularly scanning and patching systems and software is essential to prevent ransomware attacks that exploit known vulnerabilities. Vulnerability management systems help identify vulnerabilities, prioritize their remediation, and ensure systems are up to date with the latest patches.
10. Data Backup and Disaster Recovery:
While they do not directly prevent a ransomware attack, having robust backup and disaster recovery solutions are essential for recovering from ransomware attacks. Regularly backing up critical data and ensuring its integrity allows organizations to restore their systems to a clean state in the event of a ransomware attack, without paying the ransom. Offline or off-site backups (isolating backups from the main network), using reliable backup solutions that enable fast recovery are particularly important to prevent ransomware from encrypting backup data, restoring their data quickly and minimizing downtime.
11. User Education and Awareness:
Educating employees about ransomware threats, best security practices, and how to identify and report suspicious emails or websites through regular security awareness programs can significantly reduce the risk of successful attacks. This is a critical investment in protecting your organization from security incidents and ensuring that your security tech is used appropriately.
12. Email Security Gateways:
Ransomware is commonly delivered through phishing emails or malicious attachments. Email security gateways employ advanced filtering techniques, including content analysis, spam detection, and URL reputation checks, to block malicious emails before they reach users’ inboxes.
13. Web Filtering and Content Security Solutions:
Web filtering technologies and content security solutions can filter internet traffic and prevent users from accessing malicious websites or downloading infected files. By leveraging URL filtering, reputation checks, and content analysis, these solutions can block known ransomware distribution channels, prevent accidental downloads and reduce the risk of employees inadvertently falling victim to phishing attacks.
14. Behavior-Based Threat Detection:
Advanced security solutions employ behavior-based analytics to detect ransomware attacks based on abnormal system or user behavior. By analyzing patterns, file access permissions, and file modifications, these solutions can identify ransomware activity that might not be caught by traditional signature-based detection methods.
Security Tech Vendors
Sr. No. | Security Tech | Vendors |
|---|---|---|
1 | Endpoint Protection Platforms (EPP) | Crowdstrike, Sentinel One |
2 | Next-Generation Firewalls (NGFW) | Palo Alto Networks, Fortinet |
3 | Intrusion Detection/Prevention Systems (IDS/IPS) | Cisco, Fortinet |
4 | Threat Intelligence Platforms | Crowdstrike, Palo Alto Networks, Cisco Talos |
5 | Security Information and Event Management (SIEM) | Securonix, Splunk, MS Azure Sentinel |
6 | Application Whitelisting | (Included in NGFW) |
7 | Patch Management Systems | MS SCCM, Managengine, N-Able |
8 | Vulnerability Management Systems | Qualys, Nessus |
9 | Data Backup | Arcserve, Veeam, Carbonite |
10 | User Education and Awareness | KnowB4 |
11 | Email Security Gateways | Proofpoint |
12
| Web Filtering and Content Security Solutions | Checkpoint, Cisco |
13 | Behavior-Based Threat Detection | Crowdstrike, Cisco |
Disclaimer: We have recommended these vendors based on years of consulting experience. No other parameters have been considered for this list.
It’s important to note that while these technologies can significantly enhance an organization’s security posture, a holistic approach that includes user education, security policies, and incident response planning is necessary to effectively combat ransomware threats.
How databrackets can help you prevent Ransomware
Experts at databrackets have extensive experience working with clients across a variety of industries. We have customized services to help you detect and prevent Ransomware. They include:
- Security Tech Consulting: Our certified experts understand your risk exposure and recommend best-in-class tools to mitigate the risks.
- Customized Policies and Procedures: Based on our assessment and after understanding your processes and procedures, we leverage our extensive policy templates and customize them for your organization.
- Customized Training: We customize our training content based on the roles in your organization and your existing procedures.
- Regular Compliance Audits: We conduct regular audits to support your business requirements for periodic regulatory and customer-contract based evaluation.
- Regular Vulnerability Scans and Pen Testing: We conduct Vulnerability Scans and Third party Pen Testing periodically.
- Managed Security Services: We offer managed compliance and security services to continuously monitor and update your security team about your security posture.
- Backups & Disaster recovery: We help you design a plan & implement solutions for Business Continuity.
Our team has supported organizations across a wide variety of industries to align their processes with security frameworks like HIPAA, 21 CFR Part 11, ISO 27001:2022, SOC 2, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Related Links:
What are the new controls added to ISO 27001 in 2022?
How to Select a Security Vendor
Sources of Ransomware Attacks on Healthcare Systems
Can you have a Ransomware attack if you are HIPAA-compliant?
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.
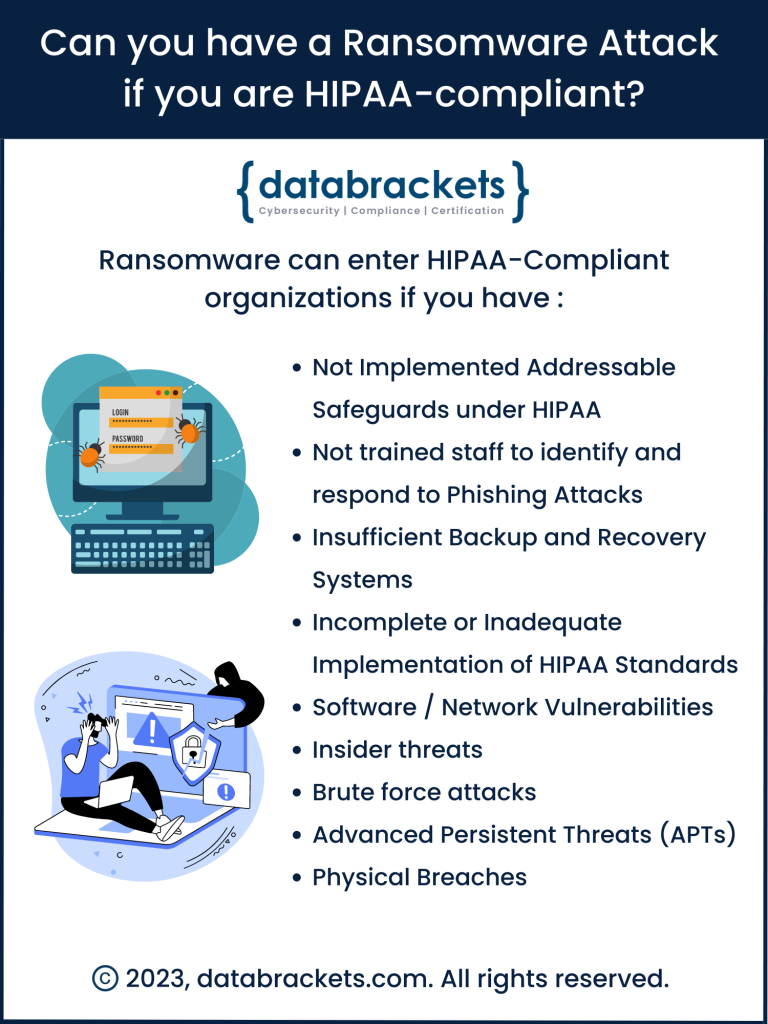 The short answer:
The short answer: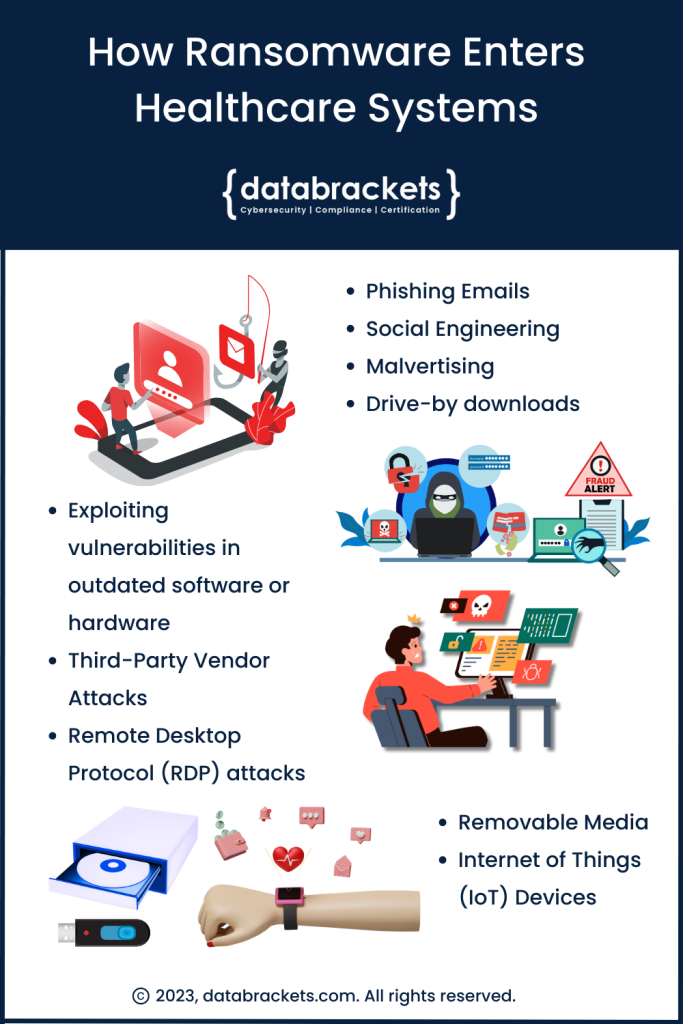 A cohort study published in The Journal of the American Medical Association in December of 2022 revealed that Ransomware attacks targeting Healthcare delivery organizations more than
A cohort study published in The Journal of the American Medical Association in December of 2022 revealed that Ransomware attacks targeting Healthcare delivery organizations more than