In the rapidly evolving landscape of healthcare, the integration of technology has become indispensable, particularly in the field of radiology where digital systems are fundamental to diagnosis and treatment. However, as the reliance on digital platforms increases, so does the vulnerability to cyber threats. Hence, ensuring robust cybersecurity measures alongside strict compliance protocols has become imperative for the radiology sector.
The convergence of sensitive patient data, advanced imaging technologies, and interconnected networks underscores the critical need for tailored cybersecurity and compliance best practices. Not only do these practices safeguard patient confidentiality and data integrity, but they also uphold the reliability and trustworthiness of diagnostic procedures, ultimately contributing to the delivery of high-quality patient care in radiology.
With over a decade of experience in supporting radiology organizations to meet compliance and cybersecurity requirements, our certified experts have identified security tech, policies, training, and testing to enhance your cybersecurity posture. These are in keeping with industry best practices. The price point of implementing these industry best practices varies depending on your set-up. One way to ensure you are making the right choices for your organization is to undergo a Security Risk Analysis to detect areas of improvement and design a comprehensive cybersecurity strategy to integrate the best practices ideal for your organization.

1. Compliance & Customer Contracts for Radiology
1. HIPAA Compliance
Ensure adherence to the Health Insurance Portability and Accountability Act (HIPAA) federal regulations, which govern the security and privacy of patient health information.
If applicable, comply with the General Data Protection Regulation (GDPR) standards, particularly when dealing with patient data of European Union residents.
Conduct regular third-party independent cyber security audits and assessments to ensure compliance with relevant data protection regulations and standards and insurance cybersecurity requirements.
4. Customer Contracts
Most customers, including hospitals and other entities that share sensitive data, mandate that their vendors perform regular cybersecurity audits and tests.
2. Cybersecurity Best Practices for Radiology
1. Firewalls
Install and maintain robust firewalls to monitor and control incoming and outgoing network traffic, protecting against unauthorized access. Firewalls safeguard radiology systems by controlling incoming and outgoing network traffic, ensuring data integrity and patient confidentiality. They act as a crucial barrier, shielding radiology networks from unauthorized access and potential cyber threats.
Utilize encryption technologies to secure patient data both at rest and in transit, ensuring that even if data is intercepted, it remains unreadable. Encryption in radiology ensures patient data remains secure, safeguarding sensitive medical information from unauthorized access. Through advanced cryptographic techniques, patient confidentiality is maintained, fostering trust in the healthcare system.
Deploy IDS and IPS solutions to detect and prevent unauthorized access, malware, and other security threats. In radiology, Intrusion Detection Systems (IDS) monitor network traffic for potential threats, alerting administrators to suspicious activities such as unauthorized access to patient data. Meanwhile, Intrusion Prevention Systems (IPS) in radiology actively intervene to block or mitigate cyberattacks, safeguarding sensitive medical information and ensuring the integrity of diagnostic processes.
4. Regular Security Updates
Stay current with security patches and updates for all software, hardware, and systems to address vulnerabilities and enhance overall security posture. Regular security updates for radiology software ensure continuous protection against evolving cyber threats, safeguarding sensitive patient data and maintaining the integrity of medical imaging systems, prioritizing patient confidentiality and operational stability in healthcare environments.
5. Endpoint Protection
Implement endpoint protection solutions to secure devices such as computers, mobile devices, and medical equipment from malware and other cybersecurity threats. Endpoint Protection for radiology ensures robust security measures, shielding critical medical imaging devices from cyber threats, preserving patient data integrity and confidentiality. With real-time monitoring and advanced encryption, it fortifies the digital perimeter of radiological systems, safeguarding against unauthorized access and potential breaches.
6. Security Information and Event Management (SIEM)
Utilize SIEM tools to collect, analyze, and correlate security event data, enabling proactive threat detection and incident response. Utilizing Security Information and Event Management (SIEM) in radiology ensures robust monitoring and detection of potential threats, safeguarding sensitive patient data and maintaining regulatory compliance. SIEM solutions offer real-time analysis of security events within radiology systems, enabling prompt response to breaches or anomalies, thereby enhancing overall cybersecurity posture in healthcare environments.
7. Identity and Access Management (IAM)
Implement IAM solutions to manage user identities, control access to systems and data, and enforce least privilege principles. Identity and Access Management (IAM) in radiology ensures that only authorized healthcare professionals can access sensitive patient data, safeguarding patient privacy and maintaining compliance. IAM systems in radiology streamline user authentication, facilitating seamless access to critical imaging resources while bolstering security against unauthorized entry or data breaches
8. Data Loss Prevention (DLP)
Deploy DLP solutions to monitor, detect, and prevent unauthorized access or transmission of sensitive patient data, both within the organization and externally. Data Loss Prevention (DLP) in radiology ensures secure handling of sensitive patient information, safeguarding against unauthorized access or inadvertent disclosure, preserving patient confidentiality and regulatory compliance. By implementing DLP measures, radiology facilities mitigate risks of data breaches, maintaining integrity and privacy of medical records essential for patient care.
9. Other security best practices
Based on your environment & architecture, the security technology, policies and procedures need to be appropriately chosen and implemented.
3. Policies and Procedures for Radiology
1. Data Classification
Establish a data classification policy to categorize patient data based on sensitivity and define appropriate handling and protection measures for each category. Data classification in radiology involves organizing medical images and patient information into categories based on factors like pathology, anatomy, and imaging technique, aiding in efficient retrieval and analysis for accurate diagnoses and treatment planning. By categorizing radiological data, healthcare professionals can streamline interpretation processes, enhance data security measures, and facilitate research endeavors aimed at improving patient outcomes.
2. Access Control Policies
Implement access control policies and procedures to ensure that only authorized individuals have access to patient data, based on the principle of least privilege. Access control policies for radiology ensure only authorized personnel access sensitive patient images and records, safeguarding patient privacy and medical data integrity with strict authentication measures and role-based permissions. Implementation involves meticulous regulation of user privileges, encryption protocols, and audit trails to maintain confidentiality and compliance with healthcare regulations.
3.Incident Response Plans and Procedures
Develop a comprehensive incident response plan outlining procedures for detecting, responding to, and mitigating data breaches or security incidents promptly. In radiology, an incident response plan ensures swift and coordinated action in the event of equipment failure or data breach, safeguarding patient information and maintaining operational continuity. By delineating roles, protocols, and communication channels, the radiology incident response plan mitigates risks, minimizes downtime, and upholds quality standards in diagnostic imaging services.
4. Documented Procedures
Document all security-related procedures, including data handling, storage, transmission, and disposal, and ensure that employees are trained on and adhere to these procedures consistently. Documented procedures in radiology ensure precision, guiding technicians through each step with clarity and consistency. These protocols safeguard accuracy and streamline diagnostic processes, enhancing patient care.
5. Business Continuity Planning
Effective business continuity planning for radiology ensures uninterrupted patient care amidst emergencies, safeguarding critical imaging services. Proactive measures, including redundancy protocols and remote access solutions, mitigate risks and uphold operational resilience in radiology practices.
6. Business Associate Contracts
A business associate is a person or company that performs certain functions or activities that involve the use or disclosure of protected health information (PHI) on behalf of the healthcare provider, or provides services to a Radiology firm (i.e. the covered entity). It is important to include all key elements in your business contract.
Key elements of a Business Associate Contract include:
- The nature of the services being provided by the business associate and the use of PHI involved.
- Safeguards that the business associate must implement to protect PHI.
- The business associate’s obligation to report any unauthorized use or disclosure of PHI, including breaches of unsecured PHI, to the covered entity.
- Requirements for the business associate to ensure that any subcontractors that create, receive, maintain, or transmit PHI on behalf of the business associate agree to the same restrictions and conditions.
- The radiology firm’s right to terminate the contract if the business associate violates a material term of the agreement.
4. Staff Training for Radiology
1. Phishing Training
Radiology employees undergo phishing training to enhance their awareness, recognizing and thwarting potential cyber threats lurking in deceptive emails. Through simulated exercises, they learn to identify red flags and safeguard sensitive medical information from phishing attacks.
2. Security Awareness Training
Security awareness training for radiology employees ensures vigilant protection of sensitive patient data, fostering a culture of confidentiality and compliance within the healthcare environment. Empowering staff with the knowledge to identify and mitigate cybersecurity risks strengthens the overall security posture, safeguarding both patient privacy and organizational integrity.
3.Compliance Training
Compliance-oriented training for radiology employees ensures adherence to rigorous safety protocols and regulatory standards, minimizing risks associated with medical imaging procedures. By emphasizing compliance with industry guidelines and best practices, radiology staff are equipped to deliver quality patient care while maintaining ethical and legal integrity.
4. Policy and procedures training based on roles
Policy and Procedures training tailored to radiology roles ensures precise adherence to safety protocols and regulatory standards, enhancing patient care and operational efficiency within the radiology department. By aligning training with specific job functions, radiology employees gain the expertise needed to navigate complex imaging processes with accuracy and confidence.
5. Automated and Manual Security Testing for Radiology
1. Vulnerability Assessment & Pen Testing
Automated and Manual Vulnerability Assessment & Pen Testing for Radiology involves evaluating and fortifying digital systems to protect sensitive medical data from cyber threats. While there are differences between these 2 types of security testing methods, there are several benefits of conducting both to test different aspects of your cybersecurity strategy.
2. Areas of Pen Testing for Radiology
While there are several Benefits of Pen Testing for Radiology, there are specific areas which Pen Testers focus on for Radiology organizations. They are:
ii. Application Testing: In radiology application testing, precision and accuracy are paramount to ensure reliable diagnostic outcomes. Rigorous testing protocols validate the software’s ability to interpret medical images with utmost clarity and clinical relevance.
iii. Mobile App Testing: Ensuring precision in diagnostic accuracy, mobile app testing for radiology rigorously evaluates image resolution and data transfer reliability. Each pixel scrutinized, every feature vetted, mobile app testing for radiology ensures seamless integration into clinical workflows.
iv. IoT Testing: In IoT testing for radiology, meticulous verification of data accuracy and real-time transmission integrity is imperative to ensure seamless integration with diagnostic imaging systems. Rigorous validation protocols are essential to guarantee the reliability and security of IoT devices, safeguarding the confidentiality and integrity of sensitive patient information in radiological settings.
Static code testing for radiology involves analyzing the source code without executing it, aiming to detect potential issues and vulnerabilities in the software used for medical imaging processes. Dynamic code testing, on the other hand, involves running the software and examining its behavior in real-time to ensure its functionality and reliability in radiology workflows.
6. AI in Radiology
AI in radiology has revolutionized medical imaging, enhancing diagnostic accuracy and efficiency. Through advanced algorithms, AI assists radiologists in detecting anomalies and expedites patient care. Its integration promises to streamline workflows and improve patient outcomes in diagnostic processes.
Radiologists need to exercise caution with AI, and ensure that it is used to complement rather than replace their expertise, preserving human judgment and empathy in patient care. They need to remain vigilant in validating AI outputs, recognizing its limitations and potential biases to maintain diagnostic accuracy and patient trust.
How databrackets can help you with Security Best Practices for Radiology
The rapid progression of radiology digitization brings forth an expanding realm of risks. Weakly secured systems offer hackers straightforward avenues to exploit vulnerabilities, posing considerable threats to business continuity. With radiology infrastructure often accessible externally, it’s crucial for organizations in this field to continuously bolster their security measures and verify their efficacy. Proactive enhancements in security are imperative to mitigate risks and safeguard the integrity of radiological operations amidst the dynamic digital environment.
The security experts at databrackets bring years of extensive Radiology industry experience to the table, along with a deep understanding of industry-standard security practices. Our Vulnerability Assessment & Pen Testing capabilities have been accredited by the A2LA for ISO 17020 Conformity assessment for inspection bodies. We possess comprehensive knowledge of common pitfalls in system configurations, recognizing factors such as outdated software in medical devices, inadequately configured firewalls, and unpatched systems that often lead to security vulnerabilities. Through meticulous scoping and testing using a variety of tools, we meticulously uncover all potential vulnerabilities visible to attackers, ensuring thorough detection and protection for our clients’ systems and data.
Our client engagement starts with your business objective in mind. Vulnerability Assessment & Pen Testing is requested for several reasons:
- To secure your environment
- To meet certain regulatory compliance or certification requirements
- To fulfill a request made by your customer
- A combination of the reasons mentioned above
Once we understand what you require, our exercise focuses primarily on scoping of the engagement and setting expectations. We use a variety of tools depending on the type of test and systems in which we need to identify vulnerabilities & conduct pen testing. Our process includes:
- Discovery
- Identifying and finalizing assets
- Identifying vulnerabilities
- Exploitation of the vulnerabilities (Pen Testing)
- Validation of the issues identified
- Remediation/Recommendations
- Re-testing
Apart from using the tools best in the industry, we also focus on remediation and retesting of the environment. We just don’t give hundreds of pages of reports without any help to eliminate the risks. We help our clients prioritize the risks based on the context, patch the systems and select security tech, policies and procedures that are considered best practices in their industry. We also set up continuous monitoring after our tests to track any changes to your environment & send you timely alerts.
As we continue to work with our clients, we sharpen our understanding of your specific environment and system. This helps us to design cadence for continuous protection and monitoring using the right tools to ensure continual improvement and proactive identification of issues for the future. You can contact us for a customized quote or schedule a consultation.
You can also meet us in-person at RSNA 2024, at South Hall Level 3 – Booth No. 3174.
databrackets overview
Our team of security experts has supported organizations across a wide variety of industries to align their processes with security frameworks like ISO 27001:2022, SOC 2, HIPAA, 21 CFR Part 11, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC 2.0 etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Related Links:
Technologies To Detect And Prevent Ransomware Attacks
Sources of Ransomware Attacks on Healthcare Systems
What are the new controls added to ISO 27001 in 2022?
How to Select a Security Vendor
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.


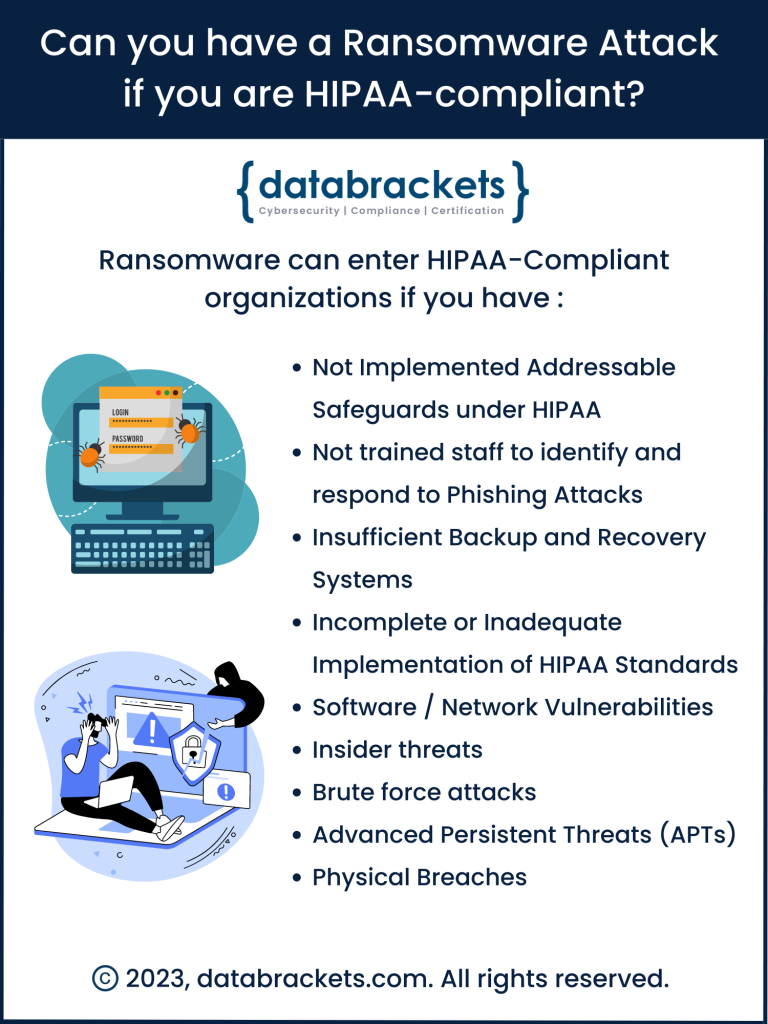 The short answer:
The short answer: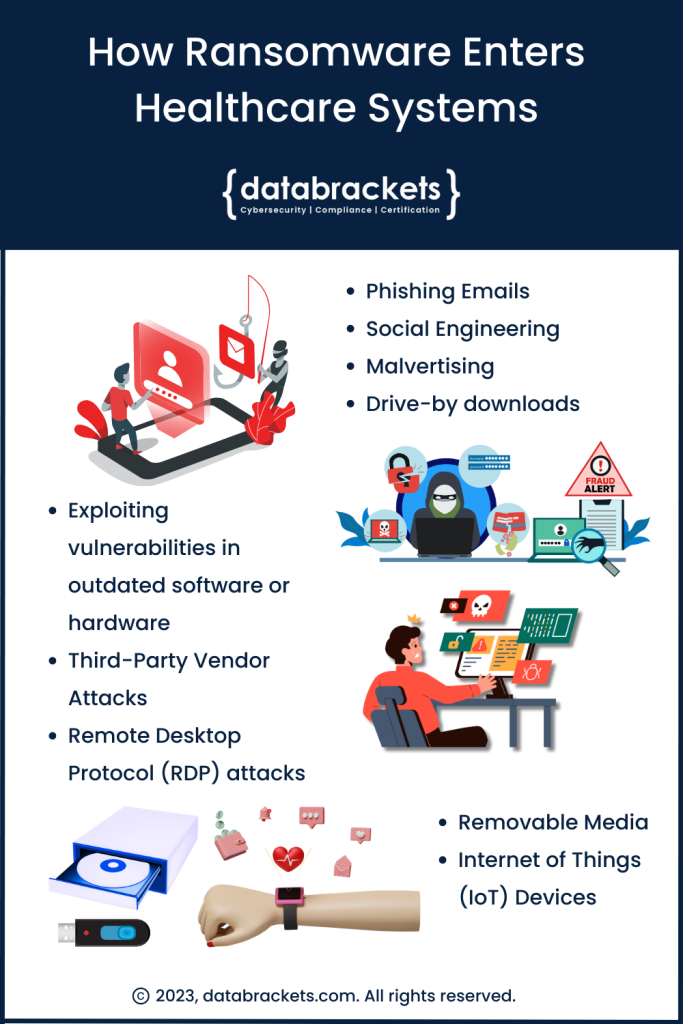 A cohort study published in The Journal of the American Medical Association in December of 2022 revealed that Ransomware attacks targeting Healthcare delivery organizations more than
A cohort study published in The Journal of the American Medical Association in December of 2022 revealed that Ransomware attacks targeting Healthcare delivery organizations more than 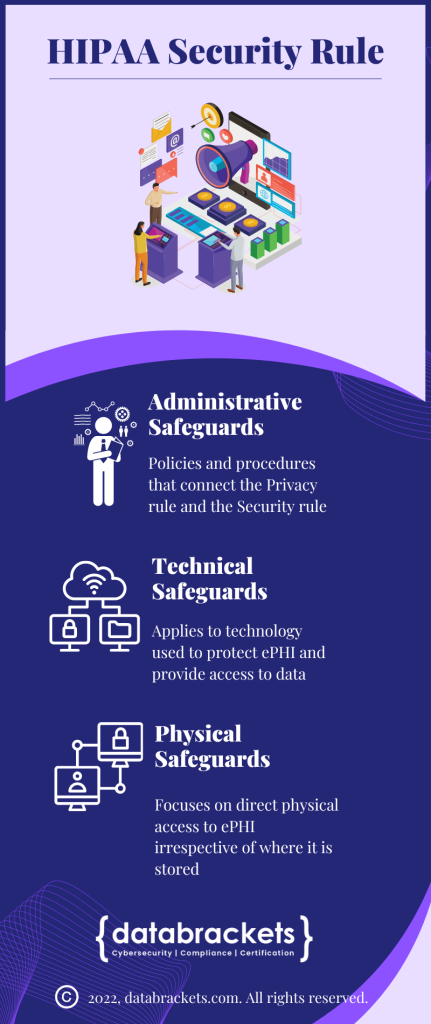
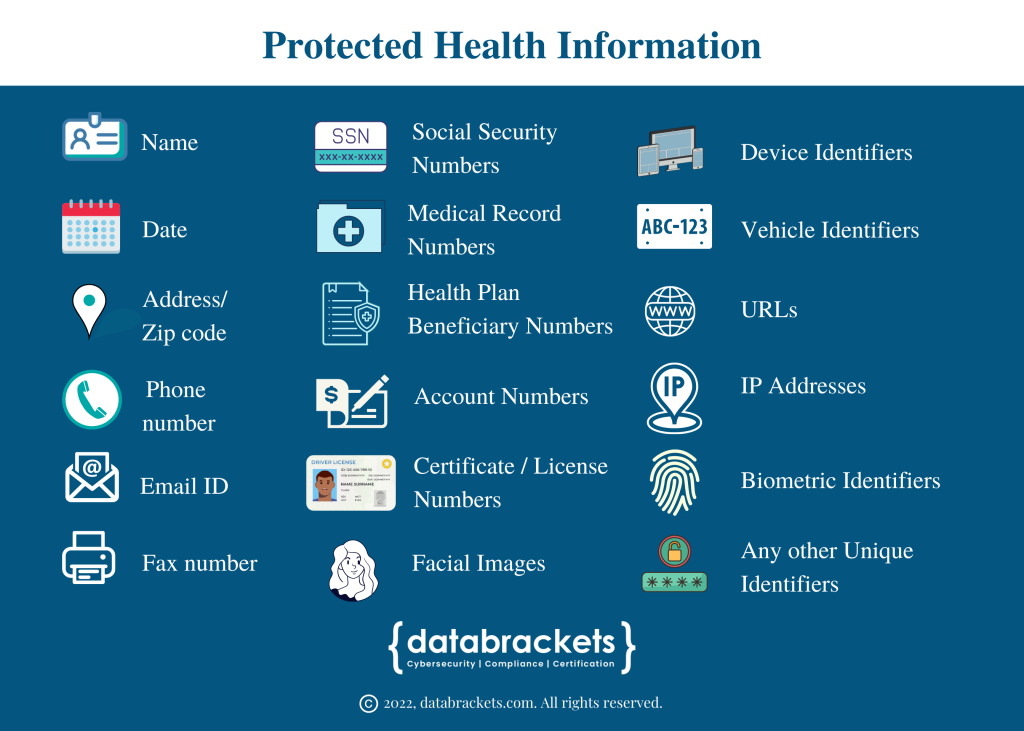
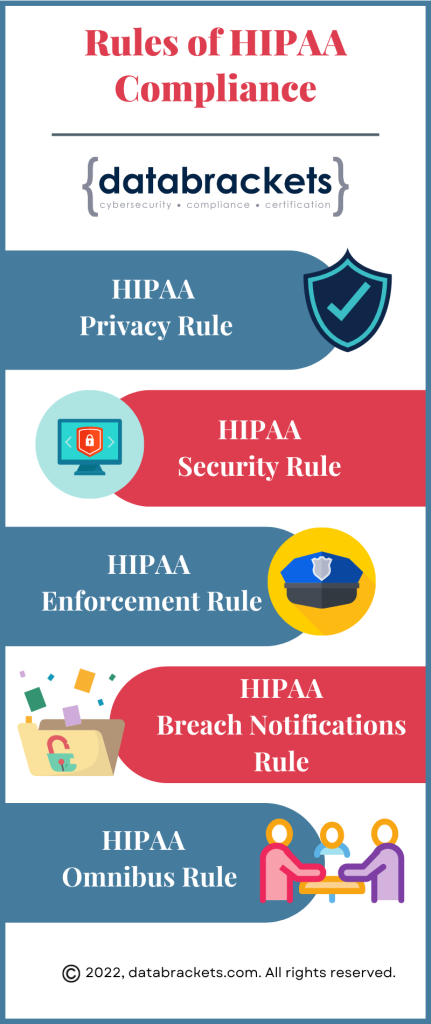 The Health Insurance Portability and Accountability Act of 1996 (
The Health Insurance Portability and Accountability Act of 1996 (